Microsoft Security Bulletins For February 2013 Released
Patch day has arrived and boy it is a big one. A total of 12 security bulletins are released today that address a total of 57 different vulnerabilities in Microsoft products. The majority of vulnerabilities affect one or multiple versions of the Windows operating system, Internet Explorer, Microsoft Office, Microsoft Server Software and the Microsoft .Net Framework.
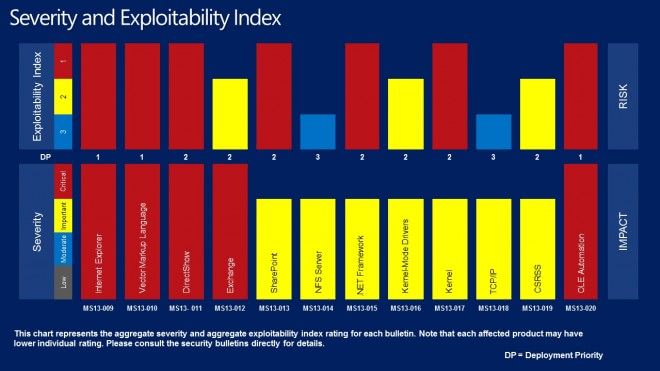
When you look at the maximum severity rating, that is the highest rating that at least one Microsoft product received, you will notice that five bulletins have received the highest possible rating critical, while the remaining seven vulnerabilities one of important, the second highest rating.
Operating system distribution
Here is the list of bulletins by operating system. First the desktop systems and then the server operating systems.
- Windows XP: 4 critical, 3 important
- Windows Vista: 3 critical, 3 important, 1 moderate
- Windows 7:Â 2 critical, 4 important, 1 moderate
- Windows 8:Â 2 critical, 2 important, 1 moderate
- Windows RT: 2 critical, 1 important, 1 moderate
- Windows Server 2003: 2 critical, 3 important, 1 moderate
- Windows Server 2008: 2 critical, 4 important, 1 moderate
- Windows server 2008 R2: 1 critical, 6 important, 1 moderate
- Windows Server 2012: 1 critical, 4 important, 1 moderate
Revised Advisories
Security Advisory 2755801 revised to address Adobe Flash Player issues in Adobe Flash Player in Internet Explorer 10 on Windows 8.
Deployment Guide
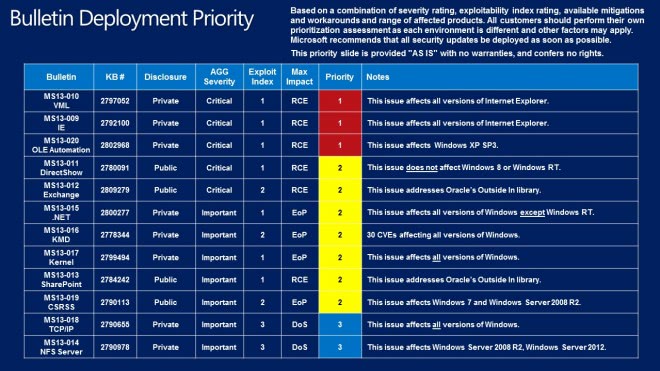
Every month, Microsoft releases a graphic that details the suggested deployment priority for businesses and computer networks. The suggested course of action is to start at the top and work your way down to the bottom. The order is computed by several variables, including the severity rating, exploitability index rating, available mitigations and workarounds, and the range of affected products.
Severity and Exploitability Index
The February 2013 bulletins
- MS13-009 Cumulative Security Update for Internet Explorer (2792100) - This security update resolves thirteen privately reported vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-010 Vulnerability in Vector Markup Language Could Allow Remote Code Execution (2797052) - This security update resolves a privately reported vulnerability in the Microsoft implementation of Vector Markup Language (VML). The vulnerability could allow remote code execution if a user viewed a specially crafted webpage using Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-011 Vulnerability in Media Decompression Could Allow Remote Code Execution (2780091) - This security update resolves one publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted media file (such as an .mpg file), opens a Microsoft Office document (such as a .ppt file) that contains a specially crafted embedded media file, or receives specially crafted streaming content. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-012 Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution (2809279) - This security update resolves publicly disclosed vulnerabilities in Microsoft Exchange Server. The most severe vulnerability is in Microsoft Exchange Server WebReady Document Viewing, and could allow remote code execution in the security context of the transcoding service on the Exchange server if a user previews a specially crafted file using Outlook Web App (OWA). The transcoding service in Exchange that is used for WebReady Document Viewing is running in the LocalService account. The LocalService account has minimum privileges on the local computer and presents anonymous credentials on the network.
- MS13-020 Vulnerability in OLE Automation Could Allow Remote Code Execution (2802968) - This security update resolves a privately reported vulnerability in Microsoft Windows Object Linking and Embedding (OLE) Automation. The vulnerability could allow remote code execution if a user opens a specially crafted file. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-013 Vulnerabilities in FAST Search Server 2010 for SharePoint Parsing Could Allow Remote Code Execution (2784242) - This security update resolves publicly disclosed vulnerabilities in Microsoft FAST Search Server 2010 for SharePoint. The vulnerabilities could allow remote code execution in the security context of a user account with a restricted token. FAST Search Server for SharePoint is only affected by this issue when Advanced Filter Pack is enabled. By default, Advanced Filter Pack is disabled.
- MS13-014 Vulnerability in NFS Server Could Allow Denial of Service (2790978) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow denial of service if an attacker attempts a file operation on a read only share. An attacker who exploited this vulnerability could cause the affected system to stop responding and restart. The vulnerability only affects Windows servers with the NFS role enabled.
- MS13-015 Vulnerability in .NET Framework Could Allow Elevation of Privilege (2800277) - This security update resolves one privately reported vulnerability in the .NET Framework. The vulnerability could allow elevation of privilege if a user views a specially crafted webpage using a web browser that can run XAML Browser Applications (XBAPs). The vulnerability could also be used by Windows .NET applications to bypass Code Access Security (CAS) restrictions. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-016 Vulnerabilities in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778344) - This security update resolves 30 privately reported vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit the vulnerabilities.
- MS13-017 Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2799494) - This security update resolves three privately reported vulnerabilities in all supported releases of Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit the vulnerabilities.
- MS13-018 Vulnerability in TCP/IP Could Allow Denial of Service (2790655) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow denial of service if an unauthenticated attacker sends a specially crafted connection termination packet to the server.
- MS13-019 Vulnerability in Windows Client/Server Run-time Subsystem (CSRSS) Could Allow Elevation of Privilege (2790113) - This security update resolves a publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to a system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
How to download and install the February 2013 updates
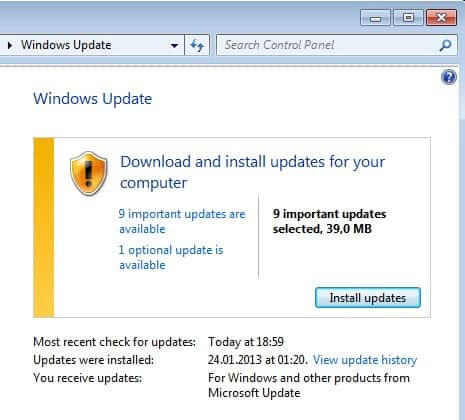
The majority of Windows users should receive the updates automatically as Windows is configured by default to install important security updates automatically. You can speed that up by checking for updates manually. On Windows 7 and older versions, you enter Windows Update in the start menu and select the appropriate option which should either open a web browser or the control panel.
On Windows 8 you tap on the Windows key to get to the start screen interface, enter Windows update, select Settings on the Charms Bar, and then Check for updates in the results listing.
Here you can click on check for updates to run a manual update check. Windows should pick up the new updates right away so that you can download and install them to your system.
If you need to or want to test updates before you install them you should download them from Microsoft's Download Center instead where they are available as standalone updates and as a monthly security ISO disc image that you can download and burn to DVD or mount on the system.
Advertisement
















57 isn’t mind-numbing. What’s mind-numbing are the 100s (or 1,000s) of remaining flaws and bugs — the majority of which will _never_ be fixed.
I would add the even more mind-numbing is the fact that Microsoft’s programmers are copying un-secure code for 20 years from one version of IE ,NT Kernel… to the next and next, and next… versions.
Another mind-numbing is the fact that all/most security bugs were found by outsiders.
Patch Tuesday
Most of this month’s updates affect various versions of Windows itself, with a few impacting IE, Office, the .NET Framework, and Microsoft Server software.
MS13-009/KB 2792100 – Cumulative Security Update for Internet Explorer. (Supported versions of Windows XP, Vista, 7, 8 and RT, and Windows Server 2003, 2008/2008 R2 and 2012). This update addresses a whopping thirteen vulnerabilities in Internet Explorer 6, 7, 8, 9 and 10 that could allow an attacker to remotely execute code if a user visits a malicious web page. It’s rated critical for IE running on Windows client operating systems and moderate for IE running on Windows server operating systems. Server core installations are not affected, but the IE 10 preview release for Windows 7 is. This update requires you to restart the system.
MS13-010/KB 2797052 – Vulnerability in Vector Markup Language Could Allow Remote Code Execution. (Supported versions of Windows XP, Vista, 7, 8 and RT, and Windows Server 2003, 2008/2008 R2 and 2012). This update addresses one vulnerability in the Vector Markup Language (VML) that could allow an attacker to remotely execute code if a user visits a malicious web page. It’s rated critical for IE running on both Windows client and server operating systems. Server core installations are not affected, but the IE 10 preview release for Windows 7 is. This update requires you to restart the system.
MS13-011/KB 2780091 – Vulnerability in Media Decompression Could Allow Remote Code Execution. (Supported versions of Windows XP, Vista, Server 2003 and Server 2008). This update addresses one vulnerability that could allow an attacker to remotely execute code if the user opens a malicious media file, or an Office document that contains a malicious embedded media file. It can also be exploited by streaming malicious media content. It’s rated critical for both Windows client and server operating systems. Windows 7, 8, and RT clients and Windows Server 2008/2008 R2 and 2012 (including Server core installations) are not affected. This update may require you to restart the system.
MS13-012/KB 2809279 – Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution. (Supported versions of Exchange Server 2007 and 2010). This update addresses multiple vulnerabilities in Microsoft Exchange Server that could allow an attacker to remotely execute code if a user previews a malicious file in Outlook Web Access (OWA). It’s rated critical for both affected versions of Exchange. Exchange Server 2003 SP3 is not affected. This update may require you to restart the system.
MS13-013/KB 2784242 – Vulnerabilities in FAST Search Server 2010 for SharePoint Parsing Could Allow Remote Code Execution. (Microsoft FAST Search Server 2010 for SharePoint SP 1). This update addresses a vulnerability in Microsoft FAST Search Server 2010 for SharePoint that could allow an attacker to remotely execute code when a user account with a restricted token is logged in. It’s rated important. The vulnerability is in the Oracle Outside libraries and the Advanced Filter Pack is the affected feature. FAST Search Server 2010 for Internal Applications, for Internet Business and for SharePoint Internet Sites are not affected. This update may require you to restart the system.
MS13-014/KB 2790978 – Vulnerability in NFS Server Could Allow Denial of Service. (Windows Server 2008 R2 and Windows Server 2012, including Server Core installations with NFS role enabled). This update addresses a vulnerability in the listed versions of Windows Server that could allow an attacker to launch a denial of service (DoS) attack by attempting a file operation on a read-only share. It’s rated Important but does not affect Windows client operating systems or Windows Server 2003 and 2008 systems, nor does it affect any server on which the NFS role is disabled. This update may require you to restart the system.
MS13-015/KB 2800277 – Vulnerability in .NET Framework Could Allow Elevation of Privilege. (Supported versions of Windows XP, Vista, 7, 8, and Windows Server 2003, 2008/2008 R2 and 2012). This update addresses a vulnerability in the .NET Framework supported versions 2, 3.5, 3.5.1, 4, and 4.5 on the listed operating systems, which could allow an attacker to elevate privileges when a user visits a malicious webpage with a web browser that can run XAML Browser Applications, or possibly to bypass Code Access Security restrictions. It’s rated Important. It does not affect supported .NET Framework versions 1.0 SP3, 1.1 SP1, 3.0 SP2, or 3.5 SP1. It also does not affect .NET Framework 4.5 on Windows RT. This update may require you to restart the system.
MS13-016/KB 2778344 – Vulnerabilities in Windows Kernel-Mode Driver Could Allow Elevation of Privilege. (Supported versions of Windows XP, Vista, 7, 8 and RT, and Windows Server 2003, 2008/2008 R2 and 2012, including Server Core installations). This update addresses an incredible thirty vulnerabilities in all supported versions of Windows that could allow attackers to elevate privileges by logging onto the system and running a malicious application, due to the way the kernel-mode driver handles objects in memory. It’s rated Important, and there is no version of the Windows operating system that is not affected. This update requires you to restart the system.
MS13-017/KB 2799494 – Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege. (Supported versions of Windows XP, Vista, 7, 8 and RT, and Windows Server 2003, 2008/2008 R2 and 2012, including Server Core installations). This update is similar to the preceding one but addresses three vulnerabilities in the kernel itself that could allow an attacker to elevate privileges by logging onto the system and running a malicious application, due to the way the kernel handles objects in memory. It’s rated Important, and there is no version of the Windows operating system that is not affected. This update requires you to restart the system.
MS13-018/KB 2790655 – Vulnerability in TCP/IP Could Allow Denial of Service. (Supported versions of Windows Vista, 7, 8 and RT, and Windows Server 2008/2008 R2 and 2012, including Server Core installations). This update addresses a vulnerability in the listed versions of the Windows operating system that could allow an unauthenticated attacker to create a denial of service (DoS) attack by sending a special connection termination packet. This is made possible by the way the TCP/IP stack in those versions of the OS handles connection termination sequences. It’s rated important for affected versions of Windows Server and Moderate for affected versions of the Windows client operating system. Supported versions of Windows XP and Server 2003 are not affected. This update requires you to restart the system.
MS13-019/KB 2790113 – Vulnerability in Windows Client/Server Run-time Subsystem (CSRSS) Could Allow Elevation of Privilege. (Windows 7 for 32 bit and 64 bit systems, with and without SP1; all editions of Windows Server 2008 R2, including Server Core installation). This update addresses a vulnerability in the listed versions of the Windows operating system that could allow an attacker with valid logon credentials to elevate privileges by logging onto the system locally and running a malicious application, due to the way the Windows CSRSS handles objects in memory. Windows XP, Vista, Windows 8, and Windows RT are not affected, nor are Windows Server 2003, 2008, and 2012. This update requires you to restart the system.
MS13-020/KB 2802968 – Vulnerability in OLE Automation Could Allow Remote Code Execution. (Windows XP SP3). This update addresses a vulnerability in Object Linking and Embedding (OLE) Automation that could allow an attacker to remotely execute code if a user opens a malicious file. It’s rated critical and only affects Windows XP. Windows Vista, 7, 8, RT and Windows Server (including 2003) are not affected. This update requires you to restart the system.
Other Updates/Releases
KB2607607 – Language Packs for Windows RT. This update adds support for several eastern European languages. There’s no need to install it unless you need to use one of the following languages on your Surface RT or other Windows RT-based devices: Slovak, Bulgarian, Slovenian, Croatian, Estonian, Serbian, Kazakh, Lithuanian, Latvian.
KB2808380 – Update for Windows RT. This non-security update is designed to resolve an issue in Windows RT whereby the Windows Update service freezes after the RT device enters the “connected standby†state, after which you cannot download Windows Store apps or related updates.
KB2608659 – Update for Windows Server 2008 R2 x64 Edition. This is an update rollup for the SIS (Single Insurance Storage) component in Windows Storage Server 2008 R2 that fixes four issues regarding file corruption and loss of data.
KB2793210 – Update for Windows 8 and Windows Server 2012. This is a compatibility update that improves the user experience by reducing the problem of applications that don’t install or work correctly on Windows 8 and Server 2012.
KB2795944 – Update for Windows 8, Windows RT, and Windows Server 2012. This is a cumulative update for February 2013 that contains multiple performance and reliability improvements and resolves issues with redundant security confirmations, failure to wake from sleep, and crashes and freezes.
KB890830 – Windows Malicious Software Removal Tool – February 2013 (including Internet Explorer Version). As always, Microsoft has updated the malware definitions for the MSRT for Windows XP, Vista, Windows 7, Windows 8, Windows Server 2003, 2008 and 2008 R2. You should run the updated tool each month.
Updates since the last Patch Tuesday
There were quite a few out-of-band patches released between the January and February Patch Tuesdays:
KB2755801 – Update for Internet Explorer Flash Player for Windows 8. (Windows RT, Windows 8, Windows 8 Pro, Windows 8 Enterprise). On February 7, Microsoft released this update for Windows RT, Windows 8 and Server 2012 that (despite its classification as a non-security update) addresses a vulnerability in Flash Player for Windows 8 that could allow an attacker to gain control over a computer. Note that a restart may be required after installation.
Microsoft released five non-security updates on January 22
KB2607607 – Language Packs for Windows RT. (Windows RT). This was another update to add various languages to Windows RT, and need not be installed unless you need to use one or more of those languages on your device: Romanian, Basque, Galician, Hungarian, Turkish, Thai, Ukrainian, Greek, Catalan, Czech.
KB2793214 – Dynamic Update for Windows 8 and Windows Server 2012. (Windows 8, Windows 8 Pro, Windows 8 Enterprise and all editions of Windows Server 2012). This is a compatibility update for the legacy upgrade experience that will improve the process of upgrading to the latest version of Windows 8. It may cause a change in behavior of certain antivirus products including Norton, F-Secure and Panda.
KB2793216 – Dynamic Update for Windows 8 and Windows Server 2012. (Windows 8, Windows 8 Pro, Windows 8 Enterprise and all editions of Windows Server 2012). This compatibility update improves the web and media upgrade experience when upgrading to the latest version of Windows 8. It may cause a change in behavior of certain antivirus products including Norton, F-Secure and Panda.
KB2794119 – Update for Windows 8, Windows Server 2012, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Server 2003, and Windows XP. (Windows XP, Windows Vista, Windows 7, Windows 7 Embedded, all editions of Windows 8, Windows Server 2003, 2008 / 2008 R2, 2012). This update contains time zone (Daylight Saving Time) changes in Libya and Israel. There is no need to apply it unless you will be using those time zones. This update may cause issues with Microsoft Outlook. See the prerequisites for installation on your operating system.
KB2803748 – Update for Windows Server 2012. (All editions of Windows Server 2012). This update fixes a problem whereby the Failover Cluster Management snap-in crashes after you install update 2750149 on a Windows Server 2012-based failover cluster.
On January 14, Microsoft released one security update
MS13-008/KB2799329 – Security Update for Internet Explorer. (Internet Explorer 6, 7 and 8). This is an update for the listed versions of IE running on Windows XP, Vista, Windows 7, and Windows Server 2003, 2008 and 2008 R2. It addresses one vulnerability that could allow an attacker to execute code remotely if the user goes to a malicious web page. It is rated critical on Windows client operating systems and moderate on Windows servers. IE 9 and 10 are not affected.
Thank you very much for the complete list of updates :) Just got all of them in no time :)
Have you notice that this update parches a mind-numbing 57 separate flaws.?
Damn it, it’s time for a nice SP2 on Windows 7.
There won’t be sp2 for Windows 7. There won’t be any SPs any more for any Windows versions.
There will be just new Windows versions (paid) every year.
I read that too, but as far as I recall there was no official confirmation yet that this is indeed the case.
Thanks again for your help/ explanation with main this mount 14 updates.