Scan your local network for UPnP vulnerabilities
A report by security company Rapid7 on Tuesday brought attention to a set of vulnerabilities in UPnP that puts millions of users at risk. According to the research paper, more than 80 million unique IP addresses "were identified that responded to UPnP discovery requests from the Internet", and at least half of those were vulnerable to at least one security vulnerability the researchers used to analyze the security of devices.
Attackers can take advantage of the vulnerabilities to execute code remotely on vulnerable systems to steal passwords and files, place malware on the systems or take them over completely.
This paper quantifies the exposure of UPnP-enabled systems to the internet at large, classifies these systems by vendor, identifies specific products, and describes a number of new vulnerabilities that were identified in common UPnP implementations. Over 1,500 vendors and 6,900 products were identified that are vulnerable to least one of the security flaws outlined in this paper. Over 23 million systems were vulnerable to a single remote code execution flaw that was discovered during the course of this research.
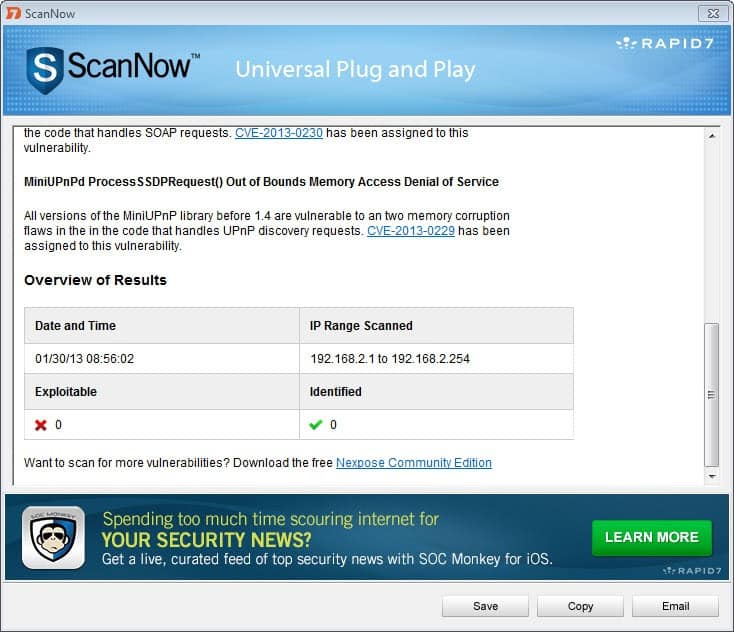
The research paper contains an "immediate actions" page that recommends a set of actions for Internet Service Providers, Businesses and home users. Both Home users and businesses can run a scanner that the researchers have created to find out whether their local network is vulnerable or not.
A couple of options are available if a vulnerable endpoint is discovered. The first course of action would be to find out if an update is available. This is usually done by contacting the manufacturer of the device, e.g. router, or searching on the manufacturer's website for updates. If there is no update, users may want to consider disabling UPnP on the device or replacing it if that is not possible at all.
A blog post on the Rapid7 website highlights how Mac and Linux users can scan networks for vulnerable devices.
Advertisement
















The subject of UPnP comes up rather frequently on Security Now. The focus is usually on Nat routers since using these is the single most effective barrier to any sort of intrusion (esp if it includes an embedded “hardware” firewall). Leaving router UPnP enabled could allow an exploit to bypass that master protection.
The several leading router brands I’ve used had a disable UPnP option. I first set up the LAN (including several computers, various wireless devices and a printer) then disable UPnP. The LAN settings are not affected.
Java is another frequent Security Now topic. The focus here is the browser plugin since that is the attack surface these drive-by exploits utilize
.
Uninstalling Java completely is just a sensible precaution if you don’t need it. I need Java for VirtualBox so I’ve disabled the plugin in Opera and Firefox.
Current Chrome and IE versions don’t even include a Java plugin by default so they’re ahead of the curve in that respect.
Coincidentally in the latest episode of Security Now (uploaded last night) Gibson and Leo Laporte cover this subject (again) in great detail. I’m watching it right now –
http://twit.tv/show/security-now/389
Interesting, thanks for posting that link.
I’m also using tomato firmware (Shibby build) on a cisco router. I have used the Gibson tool to disable UPnP in the past, but haven’t in years, and currently have UPnP enabled for ease of network access for devices and whatnot.
Ran the tool and it found no vulnerabilities at all here. Maybe tomato is on top of it? No idea, but all is well.
At any rate, good to check, thanks for the heads up.
I’m using Tomato firmware and I’m sure the patch for miniUPnP will be included in builds soon enough.
FWIW the scan identifies my Roku despite disabling UPnP… need to look into that.
Linksys router:
UPnP – Used by certain programs to automatically open ports for communication.
I don’t really think this is a new exploit. It’s been around for years. It’s just becoming popular, for some reason.
Disabling UPnP will not affect your Internet browsing or other online activity. It is a protocol used basically for network devices to communicate with each other. For example, most new routers are equipped with a UPnP routine that makes setting up a local area network as easy as the touch of a button, so you don’t have to configure everything manually.
I don’t know how to disable it in your computer, or if you even want to. But, you should be able to find a switch in your router UI to disable UPnP.
Thank you Beach Boy. This certainly helps.
Sorry for the typo. I mean Beach Bouy (not boy).
thank you Beach Boy.
unfortunately i uninstall java from my computer months ago because of security issues. now, here comes another security issue that require the use of what supposed to be a non-issue anymore. it is simply a lot of unresolved issues! i wonder who or what to blame. the parents? or the t.v.? another thing Martin, how may i disable UPnP, & how is internet surfing if i do so? thanks.
You have to disable UPnP to be safe. There is no chance those 1,500 vendors with 6900 product versions that were vulnerable through UPnP will ever update the devices with new Firmware.
The Department of Homeland Security urged computer users on Tuesday to disable a common networking technology feature, after researchers warned that hackers could exploit flaws to gain access to tens of millions of vulnerable devices.
The U.S. government’s Computer Emergency Readiness Team, on its website, advised consumers and businesses to disable a feature known as Universal Plug and Play or UPnP, and some other related features that make devices from computers to printers accessible over the open Internet.
UPnP, a communications protocol, is designed to let networks identify and communicate with equipment, reducing the amount of work it takes to set up networks. Dave Marcus, chief architect of advanced research and threat intelligence with Intel’s McAfee unit, said hackers would have a “field day” once the vulnerability in network devices is exposed….
http://www.reuters.com/article/2013/01/29/us-cybersecurity-bugs-idUSBRE90S06320130129
Alternatively, try Steve Gibson (GRC) Unplug’n’Pray
http://www.grc.com/unpnp/unpnp.htm
Tiny download, tests system lets you switch off uPnP
@ David
I was thinking it would be possible to just use their ShieldsUP online port scanner (using ‘user specified custom port probe’) and check to see if ports 1900, 2869 & 5000 are open, closed or stealth. But I suppose that wouldn’t really tell you if something has already opened a port using uPNP from inside your network.
https://www.grc.com/x/ne.dll?bh0bkyd2
The vulnerability is on routers. Unplug’n’Pray will NOT disable it on the router. Unplug’n’Pray disables UPnP service in Windows only.
Great, thanks for the link.