Microsoft Security Bulletins For January 2013 Released
It is the first Microsoft patch day of the new year and we continue our monthly series where we look at the security bulletins that get released, how the bulletins are best deployed and what you need to know besides that. Microsoft has released a total of seven bulletins of which two have a maximum severity rating of critical, the highest possible rating while the remaining five bulletins have received a severity rating of important.
What that means? There is at least one Microsoft product version that is affected by that severity. When you look at the products you will notice that six of the seven bulletins fix issues in Microsoft's Windows operating system, two in Microsoft's .Net Framework and Microsoft Server Software, and one in Microsoft Office and Developer Tools.
The January 2013 Security Bulletins
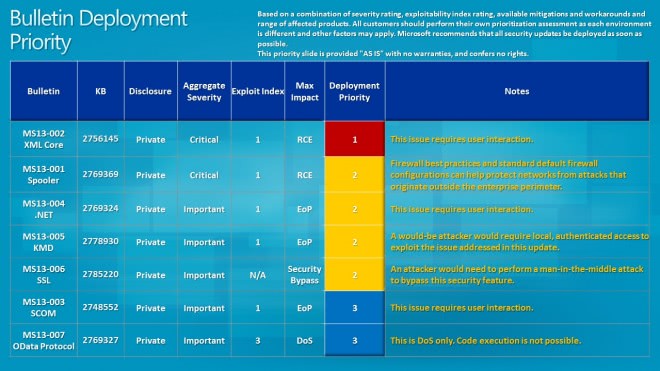
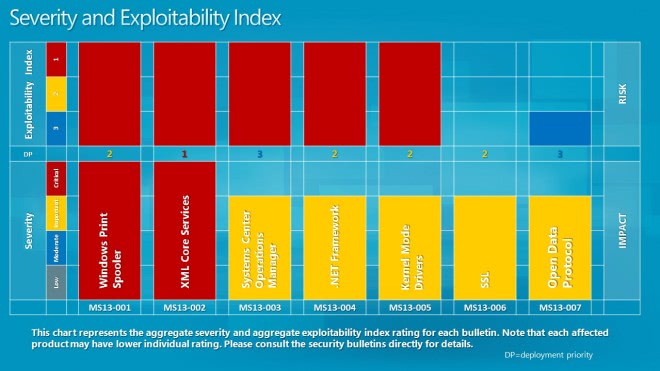
- MS13-001 - Vulnerability in Windows Print Spooler Components Could Allow Remote Code Execution (2769369) - This security update resolves one privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a print server received a specially crafted print job. Firewall best practices and standard default firewall configurations can help protect networks from attacks that originate outside the enterprise perimeter. Best practices recommend that systems connected directly to the Internet have a minimal number of ports exposed.
- MS13-002 - Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (2756145) - This security update resolves two privately reported vulnerabilities in Microsoft XML Core Services. The vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker would have no way to force users to visit such a website. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes the user to the attacker's website.
- Ms13-003Â - Vulnerabilities in System Center Operations Manager Could Allow Elevation of Privilege (2748552) - This security update resolves two privately reported vulnerabilities in Microsoft System Center Operations Manager. The vulnerabilities could allow elevation of privilege if a user visits an affected website by way of a specially crafted URL. An attacker would have no way to force users to visit such a website. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes users to the affected website.
- MS13-004 - Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (2769324) - This security update resolves four privately reported vulnerabilities in the .NET Framework. The most severe of these vulnerabilities could allow elevation of privilege if a user views a specially crafted webpage using a web browser that can run XAML Browser Applications (XBAPs). The vulnerabilities could also be used by Windows .NET applications to bypass Code Access Security (CAS) restrictions. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-005 - Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - This security update resolves one privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker runs a specially crafted application.
- MS13-006 - Vulnerability in Microsoft Windows Could Allow Security Feature Bypass (2785220) - This security update resolves a privately reported vulnerability in the implementation of SSL and TLS in Microsoft Windows. The vulnerability could allow security feature bypass if an attacker intercepts encrypted web traffic handshakes.
- MS13-007 - Vulnerability in Open Data Protocol Could Allow Denial of Service (2769327) - This security update resolves a privately reported vulnerability in the Open Data (OData) protocol. The vulnerability could allow denial of service if an unauthenticated attacker sends specially crafted HTTP requests to an affected site. Firewall best practices and standard default firewall configurations can help protect networks from attacks that originate outside the enterprise perimeter. Best practices recommend that systems that are connected to the Internet have a minimal number of ports exposed.
Overview of affected Windows systems and their severity rating.
- Windows XP SP 3 - 1 critical, 2 important
- Windows Vista SP2 - 1 critical, 4 important
- Windows 7 - 2 critical, 4 important
- Windows 8 - 1 critical, 4 important
- Windows RT - 1 critical, 4 important
- Windows Server 2003 - 2 important, 1 moderate
- Windows Server 2008 - 4 important, 1 moderate
- Windows Server 2008 R2 - 1 critical, 4 important, 1 moderate
- Windows Server 2012 - 4 important, 1 moderate
Deployment guide and severity index
Revised advisories
Microsoft has revised two advisories this month. First Security Advisory 2755801 which addresses the latest issues in Adobe Flash Player for Internet Explorer 10. It is a cumulative update that contains all previous updates for Flash Player.
The second revised advisory is Security Advisory 973811 which adds a Fix It that automatically "sets Windows XP and Server 2003 systems to only allow NTLMv2".
How to download and install the January 2013 updates
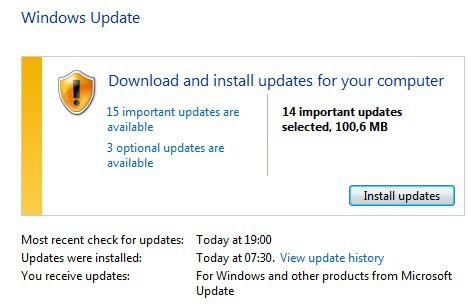
You have a couple of options to download and install the new security updates. If you have automatic updates enabled you do not really need to do anything. I'd still suggest you open Windows Update to check for new updates right away as it can take a while before Windows picks those up manually.
If you do not have automatic updates enabled you can download the updates from Microsoft's Download Center. Here you find each update listed that was released today, as well as a monthly security ISO DVD that contains them all.
You may want to consider the second option if you need to deploy the updates on multiple machines as you need to download them once only using the method.
Advertisement


















It’s the Core XML services … Uninstall it, hide it in updates and don’;t use that insecure since day pne piece of crap they call Internet Explorer and you’ll be safe from the vulnerability it is **supposed** to fix …
How did I find it?
First it hosed the database for my TV tuners as well as the program guide links … Had that happen once before a few months back … Tuner and program guide both XML based …. Then it scrambled all by TV Series and Movie data in MY Movies … again XML based …. This was 4 hours pissed away on Thursday … Gee thanx Microsoft, ever hear of error checking?
But the final straw was Friday, after playing a game where I shut down a lot of stuff before I play I did a reboot to get everything back … Got stuck in a wicked boot loop, finally made it into safe mode and shut down a couple of start up files and tried to reboot back into Windows (Win7 64 bit BTW) and got stuck n a boot loop again and finally did something I don’t like to do … hit the reset button and rebooted into safe mode again (took 3 tires) Turned off some more start up and check the logs and now it’s showing a bad block on C: drive So I schedule a disk scan on reboot and find the location of the bad block, a text log file for my UPS it writes on start up ,,, Once again XML based
So after checking what was updated again (I too was thinking .NET at this time) and saw that XML Core services had been updated it dawned on me THAT was the problem and since it’s a security update for something that’s only an issue with Internet Explorer (Which is why I use Firefox in the 1st place) I uninstalled it and issues all disappeared
Delete the Core XML update, use Firefox or Chrome … or about anything but Internet Exploder ….. and wait for Microsoft to fix THEIR screw up ……
Windows update history shows 27 since 1 Jan and there are more at the end of Oct on my computer
Thanks ilev. Quite helpful since the list of updates here on this Win 7 Pro 64 is substantially different then the ones Martin presented (based on KB numbers). Most of the different updates here were included in your list.
@Jojo
The culprit are the .net updates.
DONT INSTALL, MAKE BACKUPS OF EVERYTHING AND RESTORE POINTS!! I was one of the thousands that these updates gave BSOD blue screens of death errors. I think it is either the security attack KBs or the Net Framework updates.. not sure check out the blogs on the crashes..
Took nearly 25 minutes of wall time to install 11 fixes on WinXP system. I think there were 14 fixes for Win7. That took about 15 minutes to complete. Whew.
MS13-001/KB2769369 – Vulnerability in Windows Print Spooler Components Could Allow Remote Code Execution (Windows 7 and Windows 7 SP1, all editions of Server 2008 R2 including Core installation). This critical update addresses one vulnerability present in Windows 7 and Server 2008 R2 that could be exploited to allow an attack to remotely execute code on the computer by sending a specially crafted print job to a print server. It does not affect other versions of Windows. If you’re running Server 2008 R2 in Server Core installation and the Printing-ServerCore-Role setting is not enabled, you won’t be offered this update. Proper firewall configuration can help mitigate this vulnerability. This update requires you to restart the system.
MS13-002/KB2756145 – Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (Windows XP SP3, Windows XP Pro x64 SP2, all editions of Windows Server 2003, Vista SP2, all editions of Server 2008, Windows 7 and Windows 7 SP1, all editions of Server 2008 R2 including Core installation, Windows 8, Server 2012 including Core installation, Windows RT, Microsoft Office 2003 SP3, 2007 SP2 and 2007 SP3, Microsoft Word Viewer, Microsoft Office Compatibility Pack SP 2 and SP3, Microsoft Expression Web SP 1 and SP2, all editions of Microsoft SharePoint Server 2007 SP2 and SP3, Microsoft Groove Server 2007 SP 2 and SP3). This critical update addresses two vulnerabilities in Microsoft XML Core Services. The list of affected software is long and complicated; there are a number of combinations of XML Core Services 3.0 and operating system versions and application or server software that are not affected (see the full security bulletin for this list). Further, the impact ranges from moderate to critical, depending on the OS/software affected. If exploited, the vulnerability could enable an attacker to remotely execute code on the computer, but the user would have to use IE to visit the attacker’s specially crafted website, so proper security precautions (e.g., not clicking links in email or instant messages) will help mitigate this vulnerability. This update may require you to restart the system.
MS13-003/KB2748552 – Vulnerabilities in System Center Operations Manager Could Allow Elevation of Privilege (Microsoft System Center Operations Manager 2007 SP 1, SCOM 2007 R2). This update addresses two vulnerabilities that are confined to SCOM 2007. SCOM 2012 is not affected. The vulnerabilities could be exploited to allow an attacker to obtain elevated privileges if a user could be convinced to visit a specially crafted web site. As above, the risk is reduced by proper security practices. The update for SCOM 2007 R2 is available from the Microsoft Download Center; the update for SCOM 2007 SP1 is not yet available but is expected to be released when testing is completed. This update does not require you to restart the system.
MS13-004/KB2769324 – Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (Windows XP SP3, Windows XP Pro x64 SP2, all editions of Windows Server 2003, Vista SP2, all editions of Server 2008, Windows 7 and Windows 7 SP1, all editions of Server 2008 R2 including Core installation, Windows 8, Server 2012 including Core installation, Windows RT). This important update affects virtually all currently supported editions of Windows and addresses four vulnerabilities in all versions of the .NET Framework, including an elevation of privilege issue and a vulnerability that allows bypass of Code Access Security restrictions. This update may require you to restart the system.
MS13-005/KB2778930 – Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privileges (Vista SP2, all editions of Windows Server 2008 including Core installation, Windows 7 and Windows 7 SP1, all editions of Server 2008 R2 including Core installation, Windows 8, Server 2012 including Core installation, Windows RT). This important update addresses one vulnerability in virtually all supported versions of Windows with the exception of Windows XP SP3 and Server 2003 SP2. The vulnerability is related to the way the Windows kernel-mode driver handles window broadcast messages and could be used to gain elevated privileges by an attacker who runs a specially crafted application. This update requires you to restart the system.
MS13-006/KB2785220 – Vulnerability in Microsoft Windows Could Allow Security Feature Bypass (Vista SP2, all editions of Windows Server 2008 including Core installation, Windows 7 and Windows 7 SP1, all editions of Server 2008 R2 including Core installation, Windows 8, Server 2012 including Core installation, Windows RT). This important update addresses one vulnerability in SSL/TLS in virtually all supported versions of Windows with the exception of Windows XP SP3 and Server 2003 SP2. An exploit could result in the attacker bypassing security after intercepting encrypted web traffic handshakes. The update requires you to restart the system.
MS13-007/KB2769327 – Vulnerability in Open Data Protocol Could Allow Denial of Service (Windows XP SP3, Windows XP Pro x64 SP2, all editions of Windows Server 2003, Vista SP2, all editions of Server 2008, Windows 7 and Windows 7 SP1, all editions of Server 2008 R2 including Core installation, Windows 8, Server 2012 including Core installation). This important update affects the .NET Framework and all currently supported versions of Windows with the exception of Windows RT. It addresses one vulnerability in the Open Data protocol (OData) that could enable an attacker to create a DoS attack by sending a special HTTP request to an affected site. The vulnerability is mitigated by proper firewall configuration. This update may require you to restart the system.
Other Updates/Releases
This is a fairly heavy month for non-security updates, with twelve updates – but light in comparison to the eighteen updates we had in December.
KB2796096 – Update for Internet Explorer Flash Player for Windows 8, Windows RT, and Windows Server 2012. Although listed in the “Non-security updates†on Microsoft’s web site, this update addresses security vulnerabilities in Adobe Flash Player in IE 10, which are described in Adobe’s Security Bulletin APSB13-01.
KB2726535 – Update for Windows 7, Windows Server 2008 R2, and Windows Server 2008. This update adds the Republic of South Sudan to the list of countries in the named operating systems.
KB2750147 – Update for Microsoft .NET Framework 4.5 on Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista. This update fixes some reliability, compatibility, performance and stability issues in .NET Framework 4.5 for the named operating systems.
KB2750149 – Update for Windows 8, Windows RT, and Windows Server 2012. Like the update above, this fixes some reliability, compatibility, performance and stability issues in .NET Framework 4.5 for the named operating systems.
KB2763674 – Update for Windows Server 2008 and Windows Vista. This update fixes an issue where you cannot run an application that is signed with a SHA-256 certificate on a computer running the named operating systems.
KB2770445 – Update for Microsoft .NET Framework 4.5 on Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista). This update resolves an issue in the Microsoft .NET Framework 4.5 (different from the above update) that causes digital signatures on files produced and signed by Microsoft to expire prematurely.
KB2770446 – Update for Microsoft .NET Framework 4.5 Language Packs for x64-based Systems. This update is like the one above that addresses prematurely expiring signatures, for x64-based systems.
KB2773072 – Update for Windows 7. This update makes Windows 7 compliant with game ratings issued by various countries and adds new rating systems in Australia, Brazil, South Africa and New Zealand.
KB2785094 – Update for Windows 8, Windows RT, and Windows Server 2012. This is a cumulative update for the named operating systems that resolves performance and reliability issues related to video playback quality when streaming from Windows Media Center to Xbox consoles, Bluetooth audio playback quality and an issue that prevents you from installing a Windows Store app update if the app is installed to multiple accounts.
KB2786081 – Update for Windows 7 and Windows Server 2008 R2. This update fixes an issue wherein IE 10 doesn’t save credentials for a website after you log off or restart a computer running the named operating systems.
KB2786400 – Update for Windows 7 and Windows Server 2008 R2. This update changes the default settings of the shaping behavior for Arabic text rendering in the named operating systems.
KB890830 – Windows Malicious Software Removal Tool – January 2013 and Windows Malicious Software Removal Tool – January 2013 Internet Explorer Version. This is the monthly update to the MSRT.
Updates since the last Patch Tuesday
There was only one update issued between the December and January patch Tuesday releases:
KB2798897 (January 3) – Update for Windows. This update was an out-of-band advisory that revokes the trust of fraudulent digital certificates.
Thank you very much ilev :)
Once again, your list of updates was really useful, I found all downloads for the updates in a few minutes.
Windows RT firmware updates :
The January update, which will be available later today, includes a few improvements for Surface with Windows RT.
This update provides System Firmware (UEFI) improvements including:
Improvements to audio playback when in Connected Standby
Additional capabilities for handling firmware updates during low battery situations.
To check for updates:
Open PC Settings, by swiping in from right edge (or, if using a mouse, point to upper-right corner of screen)
Tap or click Settings
Tap or click Change PC settings
Under PC settings, tap or click Windows Update
Tap or click Check for Updates
http://answers.microsoft.com/en-us/surface/forum/surfwinrt-surfupdate/what-is-in-the-january-update-182013/506e79dd-7b77-47b6-8ca6-c9222a1b031d
How To Prevent Windows Updates From Crashing Your PC
1.Most importantly, make sure your important data has been recently backed up!
2.Change Windows Update settings so new patches are no longer automatically installed.
3.Restart your computer before applying the updates
4.Make sure at least 20% of the space on the drive that Windows is installed on is free.
5.Create a restore point manually before applying updates.
6.Temporarily disable your antivirus program.
7.Install each update one at a time, restarting your computer after each one is applied.
http://pcsupport.about.com/od/system-security/a/prevent-windows-update-problems.htm
I myself follow steps 1-5.
I would like to add one more tip: If you can (home users are usually protected by routers firewalls…), wait a few days since the updates are released, so you give time for update issues or problems to be known and/or addressed (known issues documented or discussed in forums, updates re-released…) before you install them.
Hallo Martin,
First of all great news that your going thru with your explanatory mouthy Microsoft update news.
Because of your information again I understood Cristal clear were main, this mount 14, Microsoft updates were doing.
Any new thoughts concerning when Microsoft is going to upgrade main Windows 7 Microsoft Internet explorer 32 bit & 64 bit version 9 to a 32 bit & 64 bit version 10?
No news on that yet, sorry, but you will read it here first, well among the first ;)
Microsoft Security Advisory (2755801)
Update for Vulnerabilities in Adobe Flash Player in Internet Explorer 10
Windows 8 for 32-bit Systems
Windows 8 for 64-bit Systems
Windows Server 2012
Windows RT
http://technet.microsoft.com/en-us/security/advisory/2755801
No “Fix It” for the IE 6,7,8 “Fix it “.