Splitting passwords up to increase security
Splitting passwords up could be the next big thing next to 2-factor authentication schemes which companies such as Google, Facebook or PayPal have offered as an opt-in service to their users. The two solutions use different angles to improve the protection of user account data from attackers. Where 2-factor authentication is entirely the user's responsibility, splitting up passwords is entirely dependent on the webmaster and company running the server.
The idea itself is simple: instead of saving passwords in a single location, they are split up and saved in multiple locations. Attackers who attack the server infrastructure of a company therefore need to get into multiple servers instead of just one, and since it is possible to protect the servers in different ways, for instance by using different operating systems, firewalls, security scripts and personal, it reduces the possibility of a potential breach. The technique also protects the data from inside jobs, for instance when an admin downloads data from a database.
A new software by RSA brings the technology later this year on the market. RSA's approach is the following. Passwords are broken into pieces during account creation, and then randomly saved to different servers. When a user logs in, the supplied password is split into encrypted strings, which are then sent to the password servers. The password is split into as many pieces as there are password servers, and one part of the string is randomly sent to each password server.
The user string is then combined with the stored password piece, and all the newly created strings are then compared to determine whether the password is correct or not. RSI claims that it is mathematically impossible to determine the password from an individual string or all strings combined.
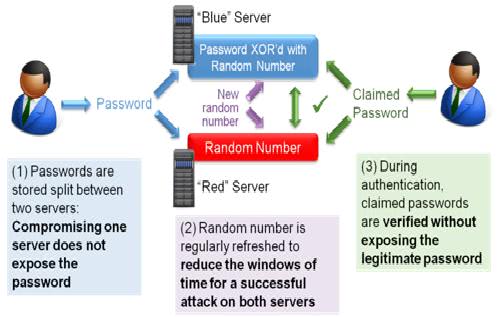
1)     Before it is stored, the password is transformed with a random number. The random number is stored in one server (“red†server) and the transformed password in a different server (“blue†server). Compromising one server is not sufficient to compromise the password.
2)Â Â Â Â Â At regular time intervals, a new random number is generated and both servers are updated with the new random number value, adding a time-based layer of protection:Â Both servers must be compromised at the same time for the password to be compromised.
3)     When an application needs to verify a password, the claimed password transformed with a new random number is sent to the “blue†server while the random number is sent to the “red†server. Each server can execute a new transformation involving the stored data and validate whether the claimed password matches the stored password without exposing the legitimate password
RSA calls the approach distributed credential protection, which is a version of long known technique called threshold cryptography. What is new is that the technology will be made available to the general public.
Using multiple servers may be problematic from an availability point of view unless parts of the password are supplied to more servers than necessary so that fallback servers are available when a server goes down.
You can read about the announcement on the official RSA blog.
Advertisement
















Excellent technical overview of an important security development esp given how pwd cracking/extraction research and techniques are getting more scary all the time.
Steve Gibson discussed this idea with Leo Laporte in the most recent Security Now episode. More from a practical or user perspective. You can read the transcript here or listen if you wish:
http://www.grc.com/securitynow.htm
This is really quite cool and I look forward to the future of it. I’ll just have trouble with trusting the sources that hold this information but I’m sure that those sources will expand.