GAuth Authenticator: use Google 2-Step Authentication without mobile phone
2-step authentication, sometimes also called 2-factor authentication, adds a second authorization step to the sign in process or other processes on the Internet. This blocks many login related attack forms like brute forcing or phishing that are common on today's Internet as attackers not only need the username and password of the account, but also another code that is generated on the fly during the log in process.
Companies like Google, Facebook or Microsoft, use mobile phones for that. Google account owners for instance can either get a SMS message containing the code when they sign in on a device that is not registered yet, or run an app on the phone instead to generate the code directly. A backup code is generated during setup of 2-step verification on Google in case the phone gets lost or stolen.
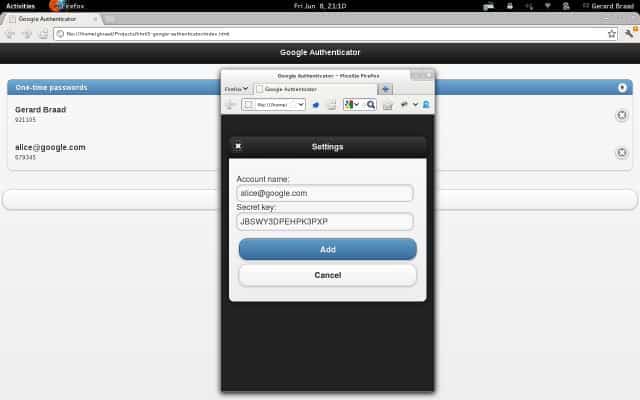
GAuth Authenticator is a browser extension, app and online service that offers another option. It allows you to generate secret keys locally, which may be useful if you do not have your phone with you. Tokens are stored in localStorage on the computer, so that it should only be used on a device that you trust and have control over.
The app is available for Symbian, Windows Phone, webOS and Android devices. It does not really make sense to install the app on an Android device, considering that Google Authenticator, the official app, is also available for the operating system. For devices where the official Google app is not available, it may be an option provided that you trust the author of it. The developer has released the source code on Github where it can be analyzed by users proficient enough to do so.
The Chrome app is listed on the Chrome Web Store, and according to information posted there, no data is transmitted which indicates that everything is handled offline.
I can see me using this app as a last resort if everything else fails. Even with the release of the source code I'd feel uncomfortable using the program unless there is no other option available. What about you? Would you use a third party program like this? (via Caschy)
Advertisement


















I have been using the GAuth Website for quite a while now and it works perfectly for me and I have never had any problems with it, It is Open Source and it is safe and secure since everything gets saved in the Web Browser Software that you use. Also, Once you delete the 2SV or the 2FA Codes from the Website and delete the Web Browser Software History, Cookies and etc… Then nothing gets saved and everything gets deleted from there. I don’t see any problems with it user wise but security wise, I have never checked on the Web Browser Software if my 2SV or my 2FA Authenticator Codes are saved on my Laptop in normal text or in encrypted text. If it is in normal text then they need to add encryption on there so when it gets saved on my Laptop in a file via the Web Browser Software that I use then it stays in encrypted form, If they have already done this then well done on making a great 2SV or 2FA Online Authenticator Website.
I think your a disillusioned person and not for other fact that some people might be disillusioned in this case over a uncontrollable need to feel safe and then not follow through or to follow the next best thing a commercialized version of a application that does not work.
The idea is like in any security to preform some sort of de-localization between user and user Allis to fragment the responsibility of one account across several layers or in this case devices.
It is a layer of abstraction simply put.
In mostly I’m confused in your point of writing this review. If your intention was to simply dismiss the application as a faux; I cant understand why in the world you would write so much about a project and simply say something as passing as “Even with the release of the source code I’d feel uncomfortable using the program unless there is no other option available.”
I have used this program and it simply works. Ive used it for Amazon AWS authentication and other gmail authentication its a great way to secure yourself from a catastrophe if your OpenID account is frozen, of the many confusing things that happens as a result of the other newer systems out there like OpenID.
It is not however as convenient as having a localized application. Also with the latest release of google-chrome the GAuth needs a update.
Feature requests, or other suggestions are welcomed!