Cryptocat an encrypted private chat alternative
If you don't trust companies such as Google, Microsoft or Facebook when it comes to communication, for instance because of the recording of your chat conversations on said networks and possibility that those records are made available to third parties or used for user profiling, you may prefer a secure solution instead.
Note: Cryptocat was discontinued in 2016. You may use a desktop program for Windows, Mac or Linux instead, or switch to Cryptodog for Chrome which is a fork of the original extension.
Cryptocat

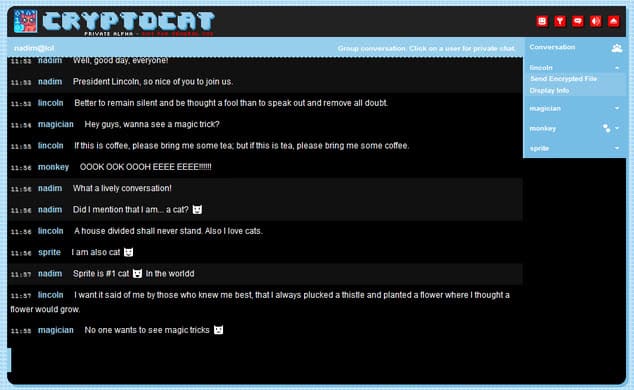
Cryptocat, available as a browser extension for Firefox, Google Chrome and Safari, may be that alternative. Probably the biggest difference to existing secure communication services is the ease of use with which you can get started. Instead of having to generate and exchange keys before you can even get started, you simply select the name of a chat room and a user name to connect.
The service creates an encryption key for you during set up. The chat room looks like all other chat rooms you may have come across. You see users who joined it on the right, and the actual messages on the left. Options are available to either chat privately with a select user, or publicly to the whole group of users.
It feels a bit strange that there is no option to password protect a chat room, considering that anyone guessing the name could enter it. While you'd then see the new user in the user list, it may happen that you overlook that at first, or have troubles locating the user if there are lots of users in that chat room.
It also needs to be noted that while chat is encrypted, your IP address is not. The developers suggest TOR to overcome this issue. Any non leaking VPN or proxy connection should suffice though.
The developers have used the following algorithms and technologies to secure communication between users:
- AES-CTR-256 for encryption and decryption
- Curve25519 for Elliptic Curve public key generation
- SHA-512 for generating 512-bit message authentication codes, shared secrets and key fingerprints
- Off-the-Record encryption support
- Cryptocat now uses the standard XMPP-MUC protocol for multi-user Instant messaging transport.
I suggest you read the full protocol specification here [pdf] if you are interested about the technical implementation.
Here is the rather unorthodox promo video:
Cryptocat is an easy to use solution which that requires no initial setup, like account creation or public key exchange, to function. The developers note that it is still an experimental service and that it should be used with that in mind.






















For those who want to give this a try, when I uninstalled the addon it also rearranged / removed most of my toolbar customization settings.
Do a backup first or prepare to rearrange!
Much of what I said doesn’t apply to what your article recommends. Your links point to Crypto.cat v2, and it looks like v1 was pulled. It might be relevant to the story to point out that this is v2 and why it requires addons to use now.
Simplified excerpt of the vulnerability from http://www.wired.com/threatlevel/2012/08/wired_opinion_patrick_ball/all/ cited by Schneier:
“But there’s a problem. If an attacker can get access to your key and your passphrase, all your encrypted data is now accessible to him. Remember that the host already has your key. All they need is your passphrase. So if the host wants to attack you, all they need to do is send you a special encryption engine that captures your passphrase the next time you use the service. As usual, it does all the encryption and decryption for you, right on your computer. But it also remembers your passphrase, and sends it secretly back to the host. This is the heart of the attack: if the server sends you a special applet that spies on you, all your encrypted data is now wide open.”
Note that if any single member of the chat fails to use the chrome browser extension, it’s as though no one is, effectively. Crypto.cat v2 should amend this, but as a result, it requires an addon always for all users.
The new (current) version of Cryptocat is *only* offered as an addon for Chrome, Firefox and Safari. The non-addon versions have all been shut down.
Sorry, Nadim. It wasn’t obvious that this article was an indirect announcement of v2. I admire your work.
You might want to mention that if you don’t use the chrome extension (or whatever future extensions they offer for other platforms), it might not be very secure.
“CryptoCat is one of a whole class of applications that rely on what’s called “host-based security”. The most famous tool in this group is Hushmail, an encrypted e-mail service that takes the same approach. Unfortunately, these tools are subject to a well-known attack. I’ll detail it below, but the short version is if you use one of these applications, your security depends entirely the security of the host. This means that in practice, CryptoCat is no more secure than Yahoo chat, and Hushmail is no more secure than Gmail. More generally, your security in a host-based encryption system is no better than having no crypto at all.”
– http://www.schneier.com/blog/archives/2012/08/cryptocat.html for more details.
https://blog.crypto.cat/2012/08/moving-to-a-browser-app-model/ This is their attempt to overcome this large security flaw. Please don’t trust host-based encryption systems with your mission critical information.
The new (current) version of Cryptocat is *only* offered as an addon for Chrome, Firefox and Safari. The non-addon versions have all been shut down. This move has been exactly to address this criticism. Therefore, this discussion no longer applies.