New Internet Explorer 0-day Vulnerability (Sept. 2012)
Microsoft has published a security advisory today that is informing system administrators and end users about a new 0-day vulnerability affecting Internet Explorer 6, 7, 8 and 9 but not IE 10. The vulnerability is already actively exploited on the Internet which makes it a pressing matter for all Windows users who work with Internet Explorer.
The advisory itself does not reveal much about the vulnerability other than that its a remote code execution vulnerability that is giving the attacker the same rights as the logged in user if exploited successfully. Internet Explorer users need to actively visit a website or open an HTML page in the browser for the attack to be successful. A specially prepared web page or hacked website are two possible scenarios.
A remote code execution vulnerability exists in the way that Internet Explorer accesses an object that has been deleted or has not been properly allocated. The vulnerability may corrupt memory in a way that could allow an attacker to execute arbitrary code in the context of the current user within Internet Explorer. An attacker could host a specially crafted website that is designed to exploit this vulnerability through Internet Explorer and then convince a user to view the website.
Internet Explorer on Windows Server versions runs in restricted mode which mitigates the vulnerability. The same is true for Microsoft email clients such as Microsoft Outlook, as HTML emails are also opened in the restricted zone. HTML links on the other hand that open in Internet Explorer are still dangerous.
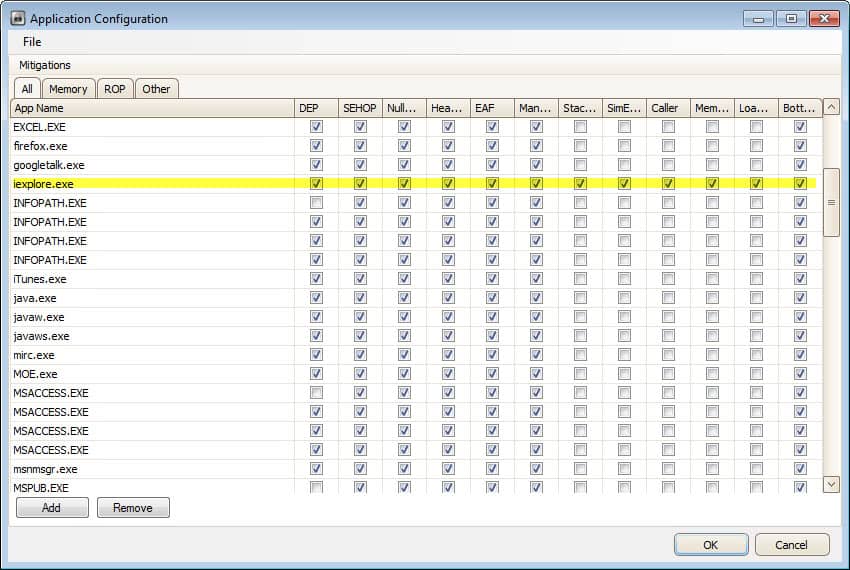
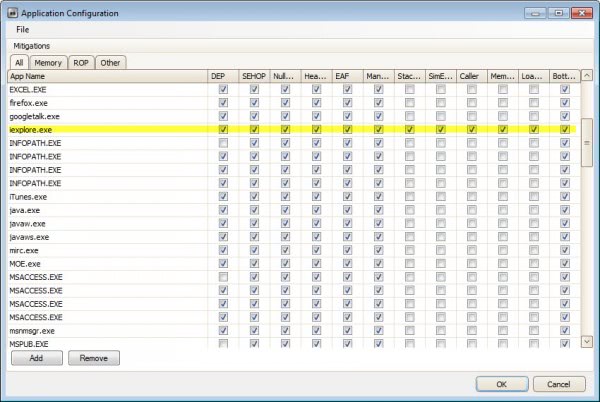
EMET, the Enhanced Mitigation Experience Toolkit, can be used to mitigate the vulnerability. You need to add Internet Explorer once you have installed the application. To do that you can either load one of the default configuration files or add iexplore.exe manually to the program.
Microsoft offers two additional mitigation workarounds.
- Set Internet and Local intranet security zone settings to "High" to block ActiveX Controls and Active Scripting in these zones, and add sites you trust to the Trusted Sites zone
- Configure Internet Explorer to prompt before running Active Scripting or to disable Active Scripting in the Internet and Local intranet security zone
You find detailed instructions on how to do that on the security advisory page. I have been running EMET on my systems ever since I discovered the application and have not experienced any issues doing so. Great program, definitely recommended.
In other news: while Internet Explorer 10 is not listed as vulnerable, it is still running a vulnerable Flash version. (thanks Ilev)
Advertisement












I just read the following on a Windows Technet blog:
“…we have tested EMET 3.0 on the Windows 8 Consumer Preview and it works great – we encountered no problems at all, so we encourage you to use EMET on all versions of Windows.”
Can anyone think of a reason why Microsoft wouldn’t have installed EMET as standard on Windows 8?
Maybe because it has not been tested on the Windows 8 RTM, or there was not enough time to implement it natively into the operating system. I think it is very likely that we will see the tool being integrated into either Windows 8 soon or Windows 9.
MS has now issued a ‘Fix it’ – a small bit of software -to repair IE so it’s usable again.
See this tutorial which includes links to the Fix it (Microsoft Fixit 50939):
http://dottech.org/81605/microsoft-releases-patch-for-internet-explorer-vulnerability-download-the-fix-now-to-stay-safe
I’ve used IE several times this week before I heard about the vulnerability. Is there an easy way to find out whether I’ve been infected?
Its really harmful i have found some more information from here- http://www.hackersnewsbulletin.com/2012/09/zero-day-vulnerability-in-internet.html
German Government warns users to stay away from IE until Microsoft fix this hole.
http://www.reuters.com/article/2012/09/18/us-microsoft-browser-idUSBRE88G1CA20120918
I wonder if this might be the reason there was an update to Adobe Flash today? (and Adobe Shockwave)
No, they did not.
http://helpx.adobe.com/flash-player/release-note/fp_114_air_34_release_notes.html
Martin,
I would like to install EMET but am afraid it will break some of the security applications
(anti-virus, Heuristic defense ….) on Windows 7. The latest stable version is 3.0 while
version 3.5 is beta.
Ilev I have not noticed anything like that. Remember that you configure EMET to work explicitly with executables you specify and nothing else.
Thanks. Will consider.
While Microsoft doesn’t reveal much about the vulnerability, others have revealed that the
vulnerability installs the “Poison Ivy” trojan.
More info regarding the vulnerability :
https://community.rapid7.com/community/metasploit/blog/2012/09/17/lets-start-the-week-with-a-new-internet-explorer-0-day-in-metasploit
Ilev thanks for posting additional information.