On Password Security
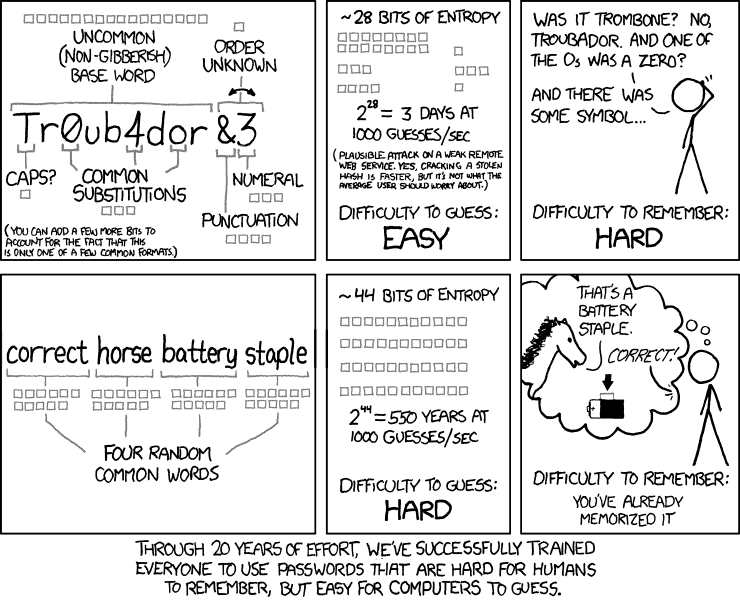
With the recent wave of websites and services that have been compromised, and the breaches that happened before that last wave, I'd like to take a look at password security on the Internet, and what we as users can learn from the breaches.
Probably the most important lesson to be learned from the hacks is that a password's strength does not really prevent it from being stolen. Even if you have selected the most secure password on the planet, it can still be stolen by hackers who manage to dump the password database. Most services do not save passwords in plain text anymore, but there are probably some out there that still do. If that is the case, your secure password is as secure as qwerty or password1.
To make matters complicated, you usually do not know how your passwords and information are protected. While some services, especially those in the security sector, may reveal information about how your information are secured, the majority of services keep tight lipped about that.
Since we do not know how services protect our data, it has become important to make sure that the impact of a successful hacking attempt is as low as possible.
- Make sure you use a strong password on every Internet service
- Make sure it is unique and not used on any other site
Strong passwords
As I have mentioned earlier, a strong password does not prevent it from being stolen if hackers manage to dump the password database or other databases of a service that you have registered an account with. The passwords are usually encrypted though. It is however only a matter of time until passwords get decrypted. Attackers usually have lists with common passwords at their disposal that they try first, before they may switch to brute forcing. Brute Forcing on the other hand is not really a feasible option, considering that the attacker would have to run all possible password combinations on all user accounts that the dictionary attack did not succeed to decrypt. If the allowed characters are upper and lower case, and numbers, it would take a very long time to decrypt the passwords, especially if strong passwords have been set by users.
As long as you use a secure password, the chance that it will be decrypted is slim. It is not impossible though, but the majority of hackers may go after the easy prey instead as it is quite possible to decrypt a large portion of user passwords this way.
Unique passwords
A strong password does not do you any good if it has been saved in plain text, or if someone else got hold of it in another way. That's why it is important to pick unique passwords as well. Even if a password is compromised, that password will only grant access to one website or service, and not dozens or hundreds of services or websites.
It also reduces the time it takes to react when a site reports that user data has been compromised. Instead of having to change passwords on dozens of sites, you only need to change it on one. It goes without saying that each unique password needs to be as strong as possible as well.
Too many passwords to remember
If your memory is really good, you may be able to remember all of your secure passwords. If it is not, and that's usually the case, you may need some aid in form of a program or method that you can use.
Password managers come to mind. Instead of having to remember dozens of strong passwords, you only need to remember the one that is protecting the password manager's database. Programs that you can use in this regard are Last Pass or KeePass which both offer more than just keeping your passwords secure and available on demand. Both let you create strong passwords which you can then make use of and save in the password manager.
You can also use your browser's passwords manager if you prefer that, but remember that it needs to be protected with a master password, especially in a multi-user environment.
Site got hacked, what now
If a website has been hacked that you have a user account at, you need to react as quickly as possible to resolve the situation. If you can't do that right now, I'd still recommend to request a password reset to invalidate the old password right away. For that, you need access to the email address associated with the account. Once you have done that, the hacker can't access the account anymore even if the password gets decrypted. You can then later on change the account password. This is especially useful if you are using a password manager but do not have access to it at that time, for instance because of being at work.
You also may want to monitor your email address and the site's news section or blog for further announcements. The announcement may offer additional information and provide recommendations on how to react to the breach.
Closing Words
With sites and services moving into the cloud, security by large has been taken out of the user's hands, at least when it comes to password security. Users still need to follow the guidelines outlined above, but once they do, they really can't do anything else to improve the security of their account.
It is up to the companies and services to step up and make sure that their users are protected from attacks, for instance by properly for instance by not saving password in plain text format, or salting passwords. Companies furthermore need to actively monitor their networks, and have emergency plans in place that allow them to react quickly if a breach is discovered.
The best course of action is to reset user account passwords in this case to protect the accounts the moment the breach has been noticed.
Advertisement
















Came across this program the other day that will generate multi-word pass phrases like the XKCD example above.
http://pwgen-win.sourceforge.net/
Hello great article I am using roboform to manage my passwords and cannot do without, especially since the recent Linkedin hack I find it necessary
KeePass stores your passwords in an encrypted data base ON YOUR computer! Not the cloud. It’s a very nice and secure program, have been using it for about 3-years, now. Of course, you can always keep a piece of paper with you with all of your passwords written on it. I used to do this until I discovered KeePass.
Not that it’s necessary, but if you feel the need to double the security of your KeePass database, you can use something like a password-protected archive (WinRar, WinZip, 7-Zip) and/or Truecrypt to store the Keepass data base in it. Just use a different and very strong password for each. This will provide an additional layer of security should your password data base fall into the wrong hands.
If you store your passwords on a removable thumb drive, I highly recommend you secure your data base as mentioned above. Those small thumb drives can be easily stolen or lost, so use some sort of security method on them. Just search the internet for better ways to protect files.
Good luck and give Keepass a try!
The genesis of the XKCD comic is here:
The Usability of Passwords
http://www.baekdal.com/insights/password-security-usability
Very interesting reading.
http://xkcd.com/936/ – linkback to the original content for the password security comic would be polite and also may help your readers discover the joy of xkcd! :)
So will we all act shocked when it’s discovered that password managers are saving our passwords “in the cloud” or dialing home and storing our passwords on the company server? Maybe an experienced user could detect/prevent this, but when such clauses creep into the fine print of the TOS in the middle of the night, most users will be unknowingly uploading their whole life right into the hands of the hackers, since it seems like we hear these stories virtually every day and corporate database security is a complete joke. And what are their consequences? Nothing, so what incentive do they have to fix it? They just send out an email saying “Gosh everybody, we don’t know how that happened but we’re looking into it. In the meantime, change your passwords!” and it blows over by the next day.
The best thing is to use 2-step verification where possible. Why? Because the hackers would need both your password and physical device to get into your account, and loosing a device would be a good warning that you should do something.
Additionally, there is one more rule: never log to anything important through public networks. this is especially true if the passwords are sent unencrypted, without HTTPS. Even if HTTPS is used, cookies might get hijacked.
There are still places limiting the strenght of the passwords setting a chars maximum.
People who doesn’t want to use a program like keepass and still find difficult to remember passwords can use sites like http://www.passwordcard.org/en to generate new strong passwords. This way they only need to remember a coordinate.