How To Remove UTM_ Tracking Tokens In Your Browser
If you read a lot of blogs, you may notice that links on those blogs sometimes contain utm_ tokens after the web address they point to. You find this usually if another blog is listed as the source, but may encounter utm tracking links in other situations as well.
If you open Google Reader or your feed reader of choice, you may notice that many of the feeds that you are subscribed to use these utm_ tracking values.
These are generated by the Urchin Traffic Monitor which services like Feedburner make use of to provide webmasters with additional traffic related information.
Update: Google discontinued Urchin and integrated the technology into the company's Google Analytics product.
Internet users may have two issues with these tracking tokens. Tokens increase the size of the web address significantly, often by more than double the stripped down size. If you want to post the link on a social networking site for instance, you may prefer to display a cleaner link, especially since some users may be deterred by the tracking added to the url.
While you could use an URL shortening service for that it would open a new can of worms as the original link would be obfuscated because of it.
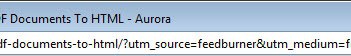
Take a link like this one, pointing to one of the latest articles on example.com
http://www.example.com/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Example+%28Example%29&utm_content=Google+Reader
More than half of that link is created by Feedburner, and not necessary to open the web page in the browser of choice.
You can strip the tracking tokens part of the address manually if you are a webmaster, but if you are a user who wants to visit a site, it is not really that feasible. While you could copy the web address, paste it into the browser's address, bar, remove all utm_ parameters, before loading the website that you want to visit, it is to time consuming and likely that you will forget to do this from time to time.
Remove UTM in Firefox or Chrome
Firefox users can install au-revoir-utm instead, which seems to work faster than the userscript. It still seems to load the tracking url first though, before it strips it off any utm_ tags. The extension has been criticized for not working on pages that do not start with ?after the original address, and that all tags, and not just utm parameters are stripped by it.
Google Chrome users finally can install Tracking Token Stripper, which too strips the tokens after the page has loaded.
Userscript (no longer working)
Update: The user script does not work anymore. We have removed the link to it as a consequence. The browser extensions listed above however seem to work just fine.
UTM-Remover is a userscript that removes UTM information from links that you open in the browser automatically. All you need to do is install the script, after which it will start doing its magic in the background without your doing. The developer notes that the script is configured to run on all Internet sites by default, and asks users to change that if they prefer to use it only for select sites.
Please note that the site is opened first, and that the tokens are removed afterwards, which means that the tracking itself is still taking place. The userscript does however remove the tracking parameters from links posted on a website.






















The aurevoir UTM thing looks to be pretty much some corporate apologists software. From their readme:
“So this extension removes them.
It’s just changing the displayed URL for copy/paste love without redirection so it should not slow down your browsing.”
IT DOES NOT STOP THE SPYING!
It just hides it from you, it further follows web browser paradigms that the URL is not for the user to see or work with (hence the messing with the URL bar post FF2 or so, the colouring, the protocol removal…..
The web is a cess pool of spyware these days, and I have got to the point where I just do not care at all if some proprietary web-based application breaks because I am preserving privacy. GMail or some shit not working? A feature, not a bug.
It is just a shame that it looks like JS is needed to deal with these things, when running JS is a dangerously stupid thing to be doing. Running code off an untrusted network? What kind of arrogant wanker expects people to do that?
I use a Privoxy rule so far to try and avoid this instance of Google malware, but it doesn’t work against HTTPS. There are also many other utm-a-likes, axzz….. for example. http://site/path/file.htm#.Un1qU3Id is another one, when the anchor #.Un1qU3Id does not exist at all in file.htm.
Google document their malware, and so finding all the possible malware-traits isn’t too hard.
[code]
{+redirect{s@^(http://.*)[\#|\?|&]utm_(?:source|medium|campaign|term|content|hp_ref|cid)=.+$@$1@ig} \
}
/.*[\#|\?|&]utm_
[/code]
This messes up Google Reader. It causes the word “undefined” to appear next to the title of each feed item.
Also checked other UTM removal scripts. They either do not work or make a mess. Scripts should be fixed every few month. Regrettably it is true for only small percentage of scripts.
When installing UTM-Remover I noticed that the script specifically excludes Gmail. This is unfortunate, but apparently necessary; the script itself explains:
// Excluding gmail as it will not load with script as pointed out by nascent at userscripts //
@exclude https://mail.google.com/*
Still it seems worthwhile to try it out for what it will do outside of Gmail.
P.S.
Instantaneous fail. The script causes an infinite reload loop (which was supposed to be fixeds, according to discussion on its homepage.
Sorry I had to delete the script.
The same for me. Uninstalled.
Thanks for the tip, Martin.
Looks promising! :)
I need something to prevent tracking cookies from invading my system, though Firefox and Do Not Track Plus doesn’t quite seem to cut it.
I usually end up having to run SuperAntiSpyware to clean out over 70 of such cookies, which can be annoying!
Excellent find as usual, Martin.
That would certainly help lots of folks.
Personally, I have used a a small bash script that runs in my proxy server to retrieve feedproxy URLs and then remove the tracking information, and then build a clean list for my reading.
A typo: Tracking “Token” Stripper
Thanks and corrected.