How Long It Would Take To Hack A Password
Password strength has become more of a issue in recent years. While it has always been important to select secure passwords, advancements in processing power and distributed computing (for instance cloud computing) have made it more of a pressing matter. Passwords that may have taken weeks or years to crack in the past are now crackable in days or even hours. That's a big security issue considering that many computer users are still selecting weak passwords as their account passwords.
Services that test a password strength can help users in evaluating their passwords. Will it take days, years or even longer to crack a selected password? That's what How Secure Is My Password will tell you.
Just head over to the service's website and enter a password in the form. You do not necessarily have to enter a password that you use actively. You can alternatively enter a comparable password to find out how long it would take to hack your password with a brute force, or maybe a combined dictionary and brute force attack.
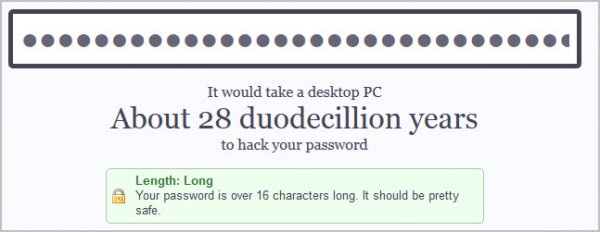
Experienced computer users know that they need to pick passwords that contain upper and lower case letters, digits as well as special characters to make it secure. Length suggestions vary from 12 to 16 in most cases. The How Secure Is My Password service suggests to use passwords with a length of at least 16 characters.
The password checker can be an eye opener for users who are using weak passwords. You can try out the service here or check our How Secure Is A Password guide for suitable alternatives.
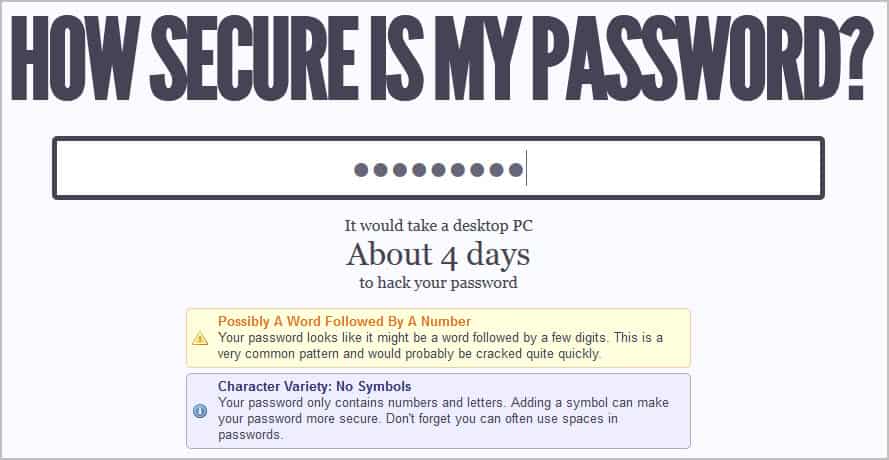
But the service is not only displaying the time it would approximately take to hack your password, it also displays information and tips that can help you select a more secure password. In addition, it compares the selected password against the list of the top 10k passwords used on the Internet.
The estimated time to hack a password is based on the processing power of a modern desktop PC. Depending on the infrastructure used, it may take considerable less time to hack a password.
Advertisement

















As a mathematician, I don’t understand why sites encourage use of a combination of digits, upper and lower case letters and symbols. Anyone trying brute force hacking will have to try every keyboard character in every position. This makes any 8-character password equally safe, unless a hacker was going to try all combinations of 8 letters before including digits and symbols. Surely two four-letter words with a symbol in the middle is adequate and memorable, e.g. past^work.
According to the information posted on the website, it would take approximated 15 days to hack your example password. And that’s a desktop PC. If you look at cloud computing, it would probably take a few minutes tops.
Oh, and the clever hacker starts with a popular password list plus variations, e.g add 1 to the word at the end automatically, before they start either to go through all numbers first or all letters. You could probably calculate which makes more sense depending on past password usage.
I recently changed all my credit card account passwords. It was a bit distressing to find that four of them no longer allow special characters, limiting me to only letters and numbers.
Anyone else think that is odd?
I still think it is odd that you get a four digit pin for some cards, or can only select a six digit password (numbers and letters only) for your online banking account. That’s highly problematic. And yes, I think that is odd and a huge oversight.
Well… My passwork will take 32 billion years, but… Nowadays, the problem is they take it instantly, ready “as-is” from Site’s data bases. lol
And remember that the calculation is based on a single desktop PC. If you use cloud computing for instance or make use of gpu acceleration then you may see that number drop significantly depending on the resources at hand.
Meena Bassem, Personally i am more satisfied with the 3 billion years that i goth, but I am thinking to changing it so i goth 1 quadrillion years.
My understanding is that most sites that require a password will lock out users after a few failed attempts. So how will hackers be able to check out a “universe” of passwords without wasting a lot of time?
While some sites may do that, other’s do not. Plus, it has happened more than once that hackers dumped a database with account information to attack it locally.
If you don’t mind, could you please clarify this part?
“Plus, it has happened more than once that hackers dumped a database with account information to attack it locally.”
Are you saying that they make both usernames and passwords available? In that case, even a strong password would be of no help.
No, I’m saying that most companies, except a few, encrypt the passwords when they store it in databases. Attackers who get access to the database server can download the data so that they can brute force it locally. This gets rid of access restrictions that may be in place online, e.g. blocking access for ten minutes after three wrong password tries.
is About 1 thousand years good enough?
There service seems to not provide results for some entries, especially for vulgar words or those that may be considered socially or politically undesirable to some groups.
I prefer Steve Gibson’s Password Haystack (http://www.grc.com/haystack.htm) for all my password checking needs.