Microsoft Patch Day October 2011 Overview
Microsoft releases Windows updates on the second Tuesday of the month. A total of eight different security bulletins have been released today by Microsoft. They update the operating system Microsoft Windows and other Microsoft products such as the .NET Framework, Microsoft Silverlight and Internet Explorer. Two of the eight bulletins have been given the highest possible severity rating critical, the remaining six one of important. Maximum severity means that there is at least one product affected by that vulnerability impact.
You find information about each security bulletin below. Please follow the links for information about affected operating systems and Microsoft applications. You find a summary of all security bulletins here.
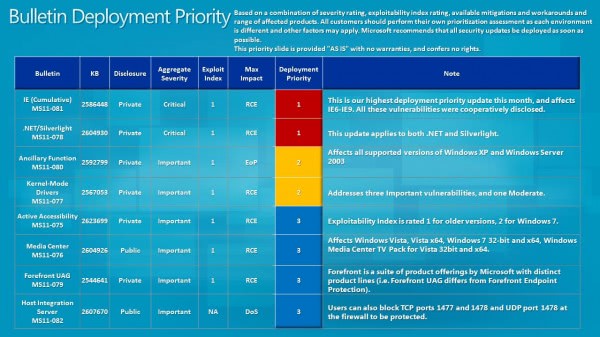
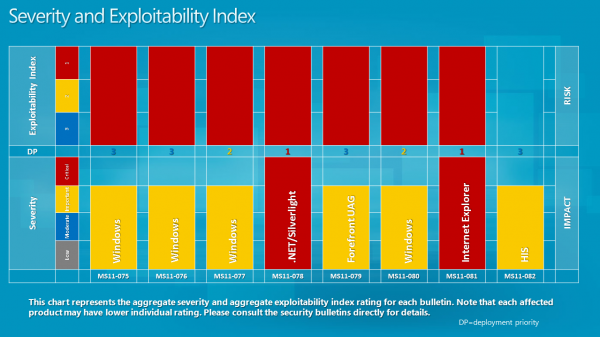
Here are the Bulletin Deployment Priority and Severity and Exploitability Index screenshots for October 2011:
And a video in which Jerry Bryant discusses this month's bulletins:
- MS11-078 - Vulnerability in .NET Framework and Microsoft Silverlight Could Allow Remote Code Execution (2604930) -
This security update resolves a privately reported vulnerability in Microsoft .NET Framework and Microsoft Silverlight. The vulnerability could allow remote code execution on a client system if a user views a specially crafted Web page using a Web browser that can run XAML Browser Applications (XBAPs) or Silverlight applications. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. The vulnerability could also allow remote code execution on a server system running IIS, if that server allows processing ASP.NET pages and an attacker succeeds in uploading a specially crafted ASP.NET page to that server and then executes the page, as could be the case in a Web hosting scenario. This vulnerability could also be used by Windows .NET applications to bypass Code Access Security (CAS) restrictions. - MS11-081 - Cumulative Security Update for Internet Explorer (2586448) - This security update resolves eight privately reported vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-075 - Vulnerability in Microsoft Active Accessibility Could Allow Remote Code Execution (2623699) - This security update resolves a privately reported vulnerability in the Microsoft Active Accessibility component. The vulnerability could allow remote code execution if an attacker convinces a user to open a legitimate file that is located in the same network directory as a specially crafted dynamic link library (DLL) file. Then, while opening the legitimate file, the Microsoft Active Accessibility component could attempt to load the DLL file and execute any code it contained. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a document from this location that is then loaded by a vulnerable application.
- MS11-076 - Vulnerability in Windows Media Center Could Allow Remote Code Execution (2604926) - This security update resolves a publicly disclosed vulnerability in Windows Media Center. The vulnerability could allow remote code execution if an attacker convinces a user to open a legitimate file that is located in the same network directory as a specially crafted dynamic link library (DLL) file. Then, while opening the legitimate file, Windows Media Center could attempt to load the DLL file and execute any code it contained. For an attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open a legitimate file.
- MS11-077 - Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2567053) - This security update resolves four privately reported vulnerabilities in Microsoft Windows. The most severe of these vulnerabilities could allow remote code execution if a user opens a specially crafted font file (such as a .fon file) in a network share, a UNC or WebDAV location, or an e-mail attachment. For a remote attack to be successful, a user must visit an untrusted remote file system location or WebDAV share and open the specially crafted font file, or open the file as an e-mail attachment.
- MS11-079 - Vulnerabilities in Microsoft Forefront Unified Access Gateway Could Cause Remote Code Execution (2544641) - This security update resolves five privately reported vulnerabilities in Forefront Unified Access Gateway (UAG). The most severe of these vulnerabilities could allow remote code execution if a user visits an affected Web site using a specially crafted URL. However, an attacker would have no way to force users to visit such a Web site. Instead, an attacker would have to persuade users to visit the Web site, typically by getting them to click a link in an e-mail message or Instant Messenger message that takes users to the attacker's Web site.
- MS11-080 - Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege (2592799) - This security update resolves a privately reported vulnerability in the Microsoft Windows Ancillary Function Driver (AFD). The vulnerability could allow elevation of privilege if an attacker logs on to a user's system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit the vulnerability.
- MS11-082 - Vulnerabilities in Host Integration Server Could Allow Denial of Service (2607670) - This security update resolves two publicly disclosed vulnerabilities in Host Integration Server. The vulnerabilities could allow denial of service if a remote attacker sends specially crafted network packets to a Host Integration Server listening on UDP port 1478 or TCP ports 1477 and 1478. Firewall best practices and standard default firewall configurations can help protect networks from attacks that originate outside the enterprise perimeter. Best practices recommend that systems that are connected to the Internet have a minimal number of ports exposed. In this case, the Host Integration Server ports should be blocked from the Internet.
Windows users can update their operating system by installing the security patches via Windows Update or Microsoft's Download Center with Windows Update being the better option if the patches do not have to be installed on multiple computer systems.
Updates are already live and available via Windows Update. Additional information are available at Microsoft's Security Response Center.
Advertisement


















Thanks Dan, for your comment I am very glad that you attended me on main mistake. Hopefully I will do better in main next comment.
Thanks again Martin, for this extensive and because of that ferry understandable and ferry readable explanation of this month Microsoft updates. Because of you effort I am learing every month a little bit more about main computer system, windows 7 and protection.
Hopefully you will keep up this gruesome work.
Hi Paul,
Just so you know (because I enjoy reading your comments), the word is spelled “very” (with a v) rather than ferry in English.
Cheers,
Dan