How To Detect A 64-bit Alureon Rootkit Infection
Alureon, or TDL, TLD3 and Tidserv, is the first rootkit that can infect 64-bit Windows PCs. Before that, only 32-bit systems were affected by rootkits, and many Windows users realized that in February, when Microsoft patch MS10-015 caused infected machines to display a blue screen. It obviously was not Microsoft's fault back then, which was first assumed by professionals and users alike. It turned out after some research that the TLD3 rootkit was responsible for that behavior.
The developers of the rootkit have improved it considerably since then, and managed to add the ability to infect 64-bit Windows systems. That's a first, and security vendors are alarmed about that trend.
However, the authors of these attacks have not been resting. Just under a month ago, we became aware of a new variant of Alureon that infects the Master Boot Record (MBR) instead of an infected driver. While this new variant did not affect 64-bit machines, it had an inert file called ldr64 as part of its virtual file system. More recently, we discovered an updated variant that successfully infected 64-bit machines running Windows Vista or higher, while rendering 64-bit Windows XP and Server 2003 machines unbootable.
Many security companies have already added detection of the 64-bit variant to their security applications, Microsoft for instance added signatures to Microsoft Security Essentials in the beginning of August.
Still, Windows 64-bit owners may want to verify for themselves that the rootkit is not installed on their operating system. As the information above suggest, Windows XP and Windows Server 2003 owners will immediately notice that something is wrong, as their operating system will fail to boot. Windows Vista or Windows 7 64-bit users should read on.
There are at least two options to do that, all with tools already included in the operating system:
Open a command prompt, with Windows-R, entering cmd and enter.
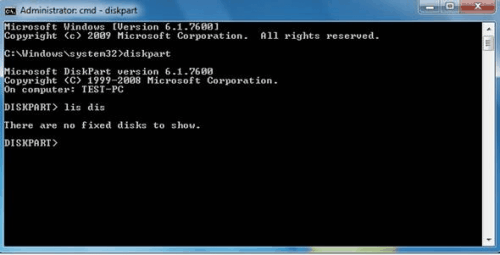
Use the command diskpart to open Diskpart in a new command line window.
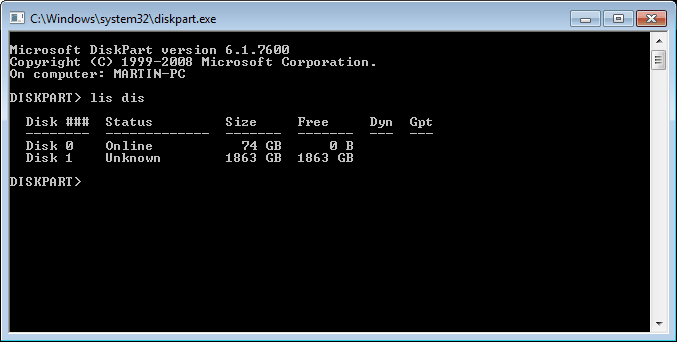
Enter lis dis in the new prompt, if it remains empty the computer is infected with the rootkit. If the disks display, it is not.
Good
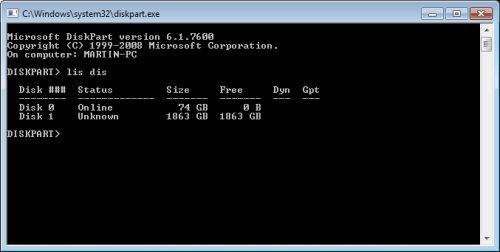
Bad
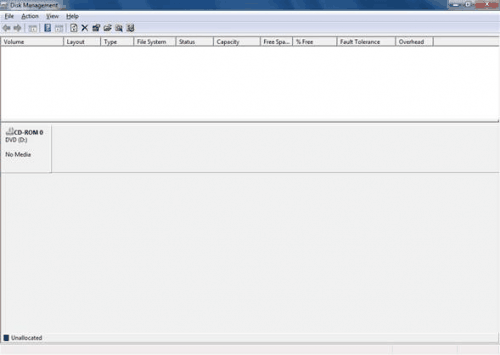
The second option to detect the 64-bit rootkit is the following: Launch Disk Management from the Computer Management pane.
If it does not show disks, it means the system is infected with the rootkit. If it shows disks, everything is fine.
Infected System
Additional information are available at Technet and Symantec.
How to Remove the Rootkit if the system is infected:
Several programs are able to remove the rootkit and repair the MBR so that the system boots normally after the repair.
Hitman Pro Beta 112 and later can do it for instance.
Advertisement




















completed both test checked good but, I still have a rootkit installed still redirecting my web browser (firefox) :(
easy to detect the presence. but very difficult to isolate the infected file. most probably it would be a legitimate system file.
example: C:\WINDOWS\system32\drivers\afd.sys
If it’s as easy to detect as that, then it’s not a very good rootkit, is it?
Hi,
How do you save / restore a dual boot Linux / Windows 7 ?
You can use this http://www.sysint.no/nedlasting/mbrfix.htm