Delete Data On SSD Permanently
Solid State Drives (SSD) are becoming increasingly popular and it seems it is only a matter of time until they replace the conventional platter-driven hard drives in computer systems around the world.
SSDs work differently than platter-based hard drives, especially when it comes to read and write processes on the drive. The most effective way to securely delete platter-based hard drives (overwriting space with data) becomes unusable on SSDs because of their design.
Data on platter-based hard disks can be deleted by overwriting it. This ensures that the data is not recoverable by data recovery tools. This method is not working on SSDs as it is not possible to specify the location to overwrite.
That's highly problematic for computer users who want to give their computer away or sell it to a third party as data on the SSD could be recovered by the new owner.
Several suggestions have been made on how to delete data on solid state drives permanently. We have decided to test those methods on an old OCZ Core Series II SSD to see how effective they are.
- Delete the files
- Format the SSD
- Encrypt the whole drive
- Issuing a secure erase command with HDDErase
The efficiency of the methods will be tested by running the data recovery software Recuva after each method. An effective method should leave no recoverable files behind.
Test System
- Windows 7 Professional 64-bit
- OCZ Core Series II SSD
- File recovery software Recuva
Deleting the files
This is a direct way to delete files on the Solid State drive. It is the only option in the article that can be used to delete files and folders selectively.
Deleting the files directly in Windows Explorer is not sufficient to protect the data from recovery software. Recuva found almost 100% of the files that have been deleted in Windows Explorer.
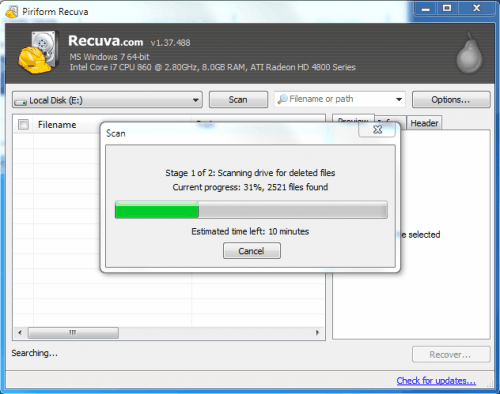
Deleting files directly in the operating system is therefor not an option to delete data permanently on solid state drives.
Formatting the Solid State Drive
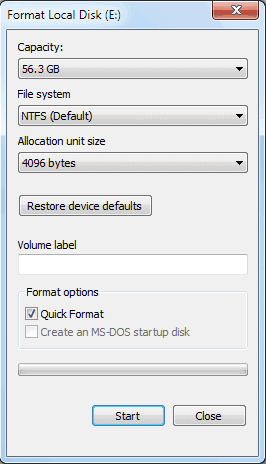
This is the easiest option as it can be executed directly without additional software requirements. Windows users need to locate the SSD in Windows Explorer, right-click it and select Format from the available options.

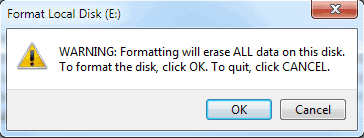
It is important to uncheck the Quick Format option to ensure that all data on the drive will be formatted.
Windows Explorer does not list any files on the drive after the full format completes.
It is now up to Recuva to find out if files can be restored from the drive after a full format. Recuva is easy to use. All it takes is to select the solid state drive letter and click the scan button. A deep scan is proposed and should be accepted. This scan might take a while depending on the size and speed of the SSD.
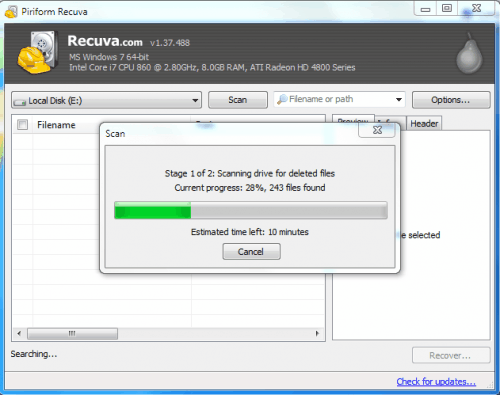
The scan did find a total of 243 files of which were all ignored and not shown in Recuva. Ignored files are mainly zero byte files, in our case all files that were found were 0-byte files.
The full format did delete all files on the drive with the exception of unrecoverable files. The ignored files that were shown as recoverable had no filename, were all 0 byte files and note recoverable.
Alternative Format Software:
Darik's Boot and Nuke is an option for users who only have the SSD connected to their computer or use another operating system.
Encrypting the Solid State Drive
Encrypting the whole SSD should in theory be enough to make the files unrecoverable. We have decided to use the encryption software True Crypt to encrypt the Solid State Drive. True Crypt if available for Windows, Linux and Mac.
Here are the steps to encrypt a drive with True Crypt. Click the Create Volume button in the main True Crypt interface. This opens the TrueCrypt volume creation wizard.
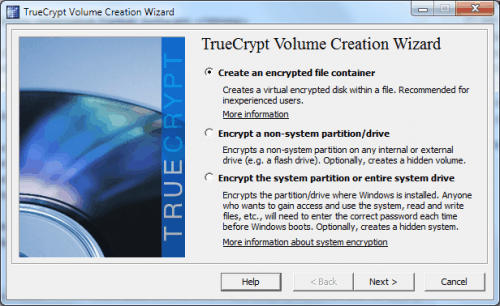
Encrypt a non-system partition/drive is the option to encrypt a drive other than the system drive. Select standard TrueCrypt volume in the next window and the select device button in the next. Pick the Solid State Drive partition from the list of connected hard drives.
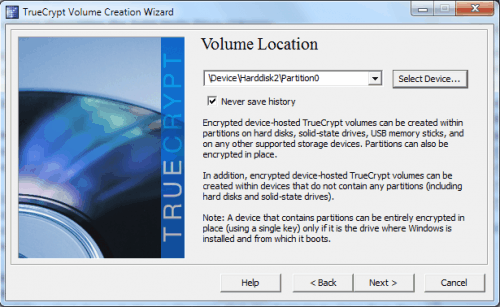
Selected Create encrypted volume and format it on the next screen, keep the default values in the encryption options on the next screen, click next on the volume size screen and pick a password thereafter. Keep the default settings from that point on by clicking Next whenever available.
A click on the Format button in the end will spawn a warning window in True Crypt stating that all data on the drive will be deleted when the True Crypt volume is created. Continue by selecting "Erase any files stored on the partition by creating a TrueCrypt volume within it".
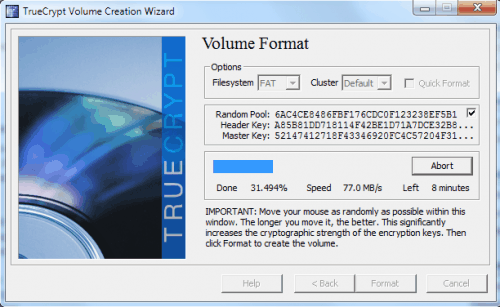
True Crypt will then format the drive and display a notification window afterwards stating that the encrypted volume has been created successfully.
Recuva was not able to scan the drive stating that the boot sector of the SSD could not be read. Additional recovery programs were not able to recover files as well. Cautious users could format the drive after it has been encrypted and run the file recovery software afterwards to test the effects. This yielded the same results as the plain drive format did.
Issuing a secure erase command with HDDErase
The secure erase command resets all NAND locations to an erased state which effectively removes all data from the drive. The command is mainly used to restore factory settings of drives that see reduced performance levels over time.
This method is for advanced users only, largely because it requires BIOS configuration and the creation of a boot disk.
HDDErase is one of the tools supporting the secure erase command. The latest version is HDDErase 4 which is not compatible anymore with Intel SSDs. Intel users need to download HDDErase 33 instead.
A bootable disk needs to be created. HDDErase will only work if AHCI is disabled in the computer BIOS.
Secure Erase scans the drive to verify that it supports the command.
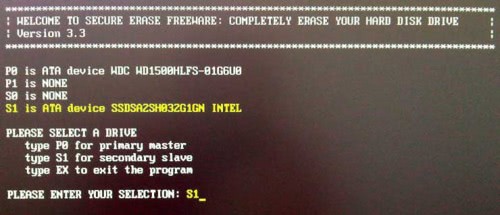
A full walkthrough of the steps required to use HDDErase to securely erase the SSD is available at IISHacks.
No data was recoverable after the secure erase command was issued in DOS.
Recommended method to erase data on solid state drives
Format, encryption and the secure erase command have made the data on the drives unrecoverable. A lot speaks for formatting the Solid State Drive as it is the easiest method of the three. It is usually not necessary to encrypt the data on the drive before formatting it as it yielded the same results as a standard format.
It is highly recommended to test the result with file recovery software to make sure that no data left-overs can be recovered.
Do you know of other methods to delete data on solid state drives permanently? Let us know in the comments.
Advertisement




















i can’t delete the partition or wipe off my ssd drive in acer aspire one. suddenly i’d tried almost all harddisk tools & partition tools but nothing’s happen. by the way it’s linux os. can someone can help me to delete the ssd drive partition?
FYI, see http://www.intelliadmin.com/index.php/2010/06/secure-hard-drive-erase/#comments
You are aware that encrypting a SSD with Truecrypt, is “overwriting space with data”, random data in this case. So is formatting it and “secure erasing”.
SSDs don’t differ from HDDs in this case.
These procedures also have to be done with a HDD if you want to be sure that no readable data is left on the disk. And you have to do it with the whole HDD.
Anyways.
It’s good to raise awareness for the need of theses procedures.
Many people, including companys and officilas don#t know this ;)
Sebastian, I mainly wanted to raise awareness that users had to take care of their storage devices before selling, trashing or giving them away. I always read that that format, encryption and secure erase were enough but I never tested it myself. This was for me a confirmation that these methods work and are sufficient to make sure the data is not recoverable afterwards.