Add CryptKeeper for on-the-fly encrypted folders in Linux

You've more than likely read Martins' piece about the outstanding encryption tool Truecrypt "TrueCrypt 6.1 Released" and have used it to create easy to use, encrypted file systems on Windows machines. Of course TrueCrypt is also available for Linux as well. But what if I told you there was an even easier system to use for on the fly folder encryption for the Linux operating system? There is, and it's a snap to use.
CryptKeeper is available for the GNOME desktop (requires Nautilus) and is a system try applet that easily manages EncFS encrypted folders without the user having to touch the command line. And CryptKeeper works very similarly to TrueCrypt but makes the whole process even easier. In this article, you will learn how to install CryptKeeper and then create and use an encrypted folder on an Ubuntu machine.
Installation
Installing CryptKeeper is as simple as installing any other software on an Ubuntu machine. Of course, this software should be just as easy to install on your favorite distribution - just modify the process as needed. The steps for installation are:
- Open up your Add/Remove Software tool.
- Search for "cryptkeeper" (No quotes).
- Select the resulting software for installation.
- Click Apply to install.
That's it. Once installed you will find the menu entry under the Applications menu, in the System Tools sub-menu.
How CryptKeeper works
The way this application works is simple: Creating encrypted, mountable file systems. You create an encrypted folder that can only be accessible if that folder is mounted, and the only way to mount that folder is to know the authentication password.
Starting and using CryptKeeper

When you start CryptKeeper, you will be surprised to see that no windows or dialogs open. As stated earlier this is a system tray applet, so the application resides in your system tray (or Notification Area). So when you start CyrptKeeper, the only thing you will see is the system tray icon appears (see Figure 1). The icon you are looking for is the keys icon. From this icon there are two actions:
Right click: Preferences, About, Quit
Left click: Mount previously created encrypted folders, Import EncFS folders, Create encrypted folders.
From the Preferences window, there isn't really much to do. There is, however, one important option you can set. If you want to make sure your encrypted folders are unmounted after being idle for a user-configured amount of time.
Now, let's create an encrypted folder. Left click CryptKeeper icon and select "New Encrypted Folder". This action will open up a Wizard that will walk you through the process of creating your folder. The steps are:
Give your folder a name and location.
Enter (twice) a password for the encrypted folder.
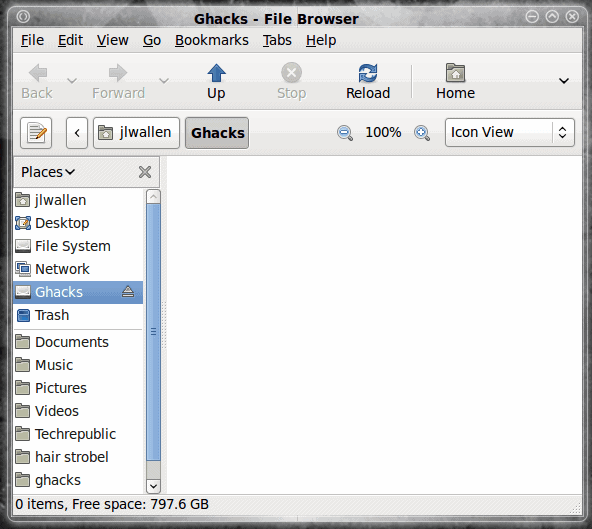
That's it. As soon as you have verified your password, and hit Forward, your new encrypted folder will open in the Nautilus file browser (see Figure 2).
With your folder open you can then place whatever you like inside. Once you are done working with the folder, you only need to unmount it to keep the contents from prying eyes. There is only one way to unmount your folder:
Left click the CryptKeeper icon and uncheck the mounted folder.
If you try to unmount the folder from within Nautilus you will be unsuccessful.
When the folder is unmounted it will seem to no longer exist on your machine. The only way you will see the file is to open up a terminal and search for the folder in your home directory using the ls -a command. Using the example I created above (encrypted folder "Ghacks") I will see the entry .Ghacks_encfs in the ~/ folder. If I try to search the contents of that folder I will see something like:
kgv8qdE4Y,8kNqkREP7cQGvz-fk9bUujZTSXd8ijrelqi0
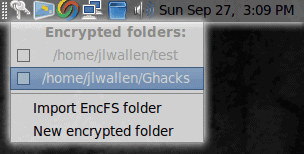
No dice. There is only one way to see the contents of this folder. To do this left click the CryptKeeper icon and select the encrypted folder you want to mount (see Figure 3). Once selected you will be prompted for the password for the folder. When you successfully enter the password the folder will mount and be opened in a new Nautilus window.
Final thoughts
Without a doubt, CryptKeeper is one of the easiest means to create on-the-fly encrypted folders to use on the Linux desktop. If you need solid encryption for personal folders, CryptKeeper is the way to go.

























> Add CryptKeeper for on-the-fly encrypted folders in Linux
I think you mean GNOME; Linux is larger than one DE. I’ve not found much for the KDE desktop, there seems to be some older apps at KDE-apps.org but nothing from 2009 even.
Interesting to know more about EncFS however (which is what CryptKeeper uses), too bad there isn’t a KryptKeeper yet :)