Enable Retpoline on Windows 10 1809 and Server right now
Microsoft has tested Retpoline, a new mitigation method against Spectre variant 2 by Google, on Windows 10 Insider Builds for some time now. The company brought Retpoline to Windows 10 version 1809 by including it in the March 1 cumulative update KB4482887 for the version of Windows 10.
Tip: use the free InSpectre program for Windows check the vulnerability status.
Retpoline promises improved performance compared to the previous mitigation method used by Microsoft in its operating systems. Microsoft monitored the performance of Windows 10 systems and determined that Retpoline improved the launch time of Office applications by about 25% among other benefits.
When all relevant kernel-mode binaries are compiled with retpoline, we’ve measured ~25% speedup in Office app launch times and up to 1.5-2x improved throughput in the Diskspd (storage) and NTttcp (networking) benchmarks on Broadwell CPUs in our lab.
Retpoline is not enabled by default on production devices even though it is included in the March 1 update. Microsoft plans to roll out the mitigation over the course of the coming months.
Administrators who don't want to wait can enable Retpoline right away provided that the devices run Windows 10 version 1809 and have the latest cumulative update installed.
Microsoft employee Mehmet Iyigun describes the process on the Tech Community site. Note that it is recommended that you back up the system and data before you apply the change.
Windows 10 Clients

Note: Microsoft did not enclose the Registry key path with "". If you copy paste Microsoft's command you will receive an error.
- Open an elevated command prompt, e.g. by opening Start, typing cmd.exe, right-clicking on the result, and selecting run as administrator.
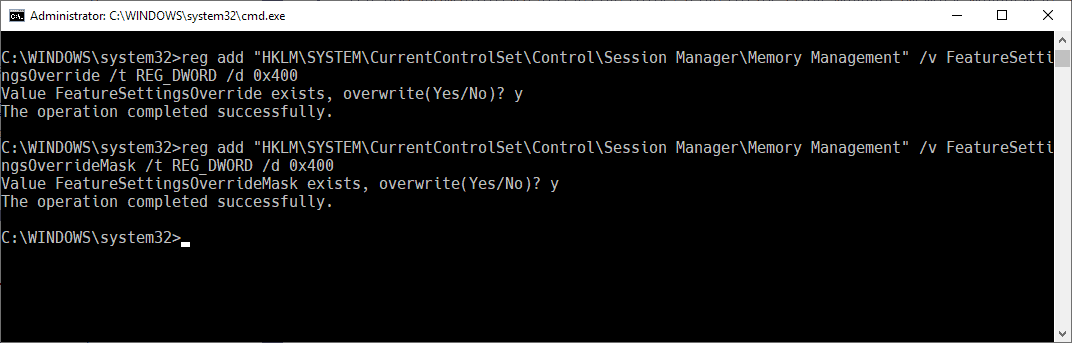
- Run the following two commands:
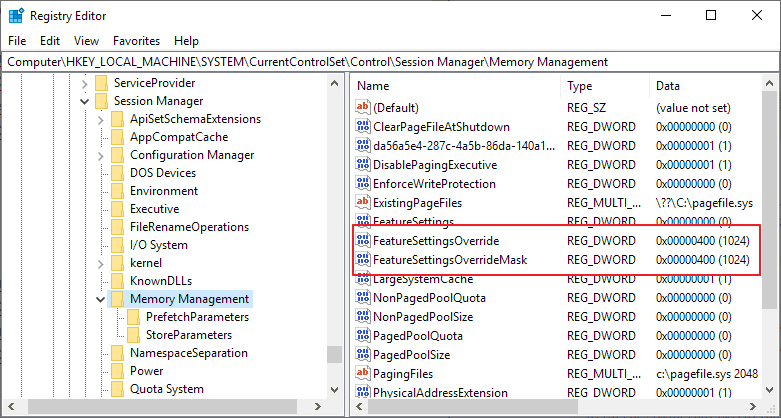
- reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0x400
- When prompted to overwrite the existing value, select Y for yes.
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 0x400- When prompted to overwrite the existing value, select Y for yes.
- reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0x400
- Restart the PC.
Alternative: use the following Registry file to make the change with a double-click on it: (Download Removed)
Windows 10 Server
- Open an elevated command prompt.
- Run the following two commands:
- reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0x400
- reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 0x401
- Restart the PC.
And here is the Registry file for Windows 10 Server versions: (Download Removed)
Note that you can make the changes in the Registry editor directly as well if you prefer to do so.
Verification
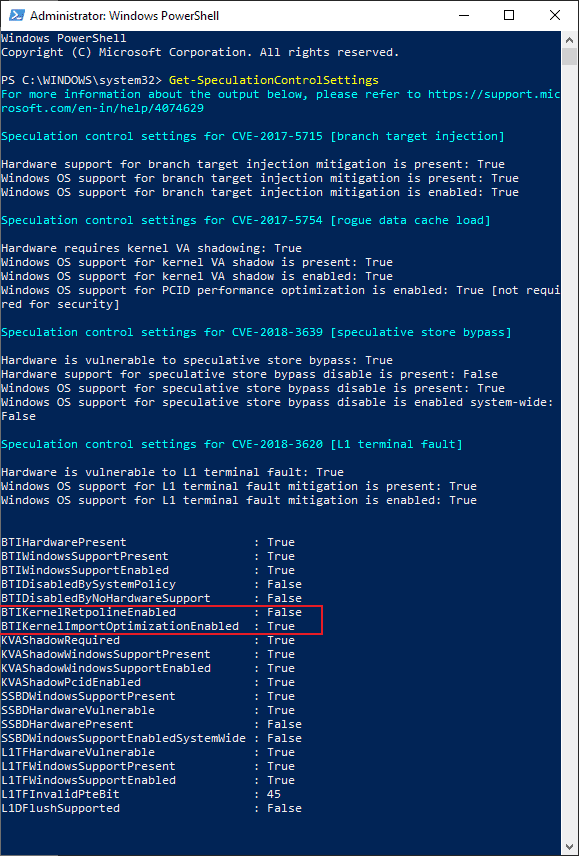
You may use the Get-SpeculationControlSettings PowerShell cmdlet to verify the status of Retpoline. BTIKernelRetpolineEnabled and BTIKernelImportOptimizationEnabled should be returned as True in the output.
Microsoft notes that Skylake and newer generations of Intel processors are not compatible with Retpoline; these will only return BTIKernelImportOptimizationEnabled as enabled when the command is run.



















If you download the registry file (for the windows client) and click on it it seems to work. However if you check if the additions have been added (according to the given registry picture) you will find it did not happen.
I think in the registry file the first accolade is wrong.
If you execute the cmd.exe explanations the change in the registry is done.
Thanks, I think it was caused by the use of the wrong “” in the reg file. Corrected.
I completely disabled the Spectre and Meltdown mitigations on my Windows 7 PC. They’re yet to be exploited, and even if they are, what’s the point of having them in the first place? Your main concern should be having such a malware in your PC in the first place.
I am being so tired about regedit. Always touching regedit, for God’s sak. Please enable other options or just release an update with all these settings by default or something!
Just for the info – the SpeculationControl cmdlet from MS site (version 1.0.11) is outdated and doesn’t have those two lines…i wasted ~2h before finding it out.
You can get the up-to-date version 1.0.12 on https://github.com/Microsoft/SpeculationControl (click “Clone or download” and then “Download ZIP”).
The whole procedure is the same:
1. extract the zip to some folder (for example C:\)
2. run Powershell as admin and go to that folder (“C:\SpeculationControl-master” if you extracted to C:\)
3. run each of those commands and put Y when it asks you to
$SaveExecutionPolicy = Get-ExecutionPolicy
Set-ExecutionPolicy RemoteSigned -Scope Currentuser
Import-Module .\SpeculationControl.psd1
Get-SpeculationControlSettings
Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuser
My God Linux is so Simple compared to this….
Im so gald I dont have to treat my OS like Im walking on eggs.
Maybe you all should start spoofing Linux as your OS online
to scare M$ so they will stop treating you like dirt.
Right.
So double clicking a registry file and rebooting is more complicated than:
1. Editing grub config file /etc/default/grub (or other bootloader).
2. Add nospectre_v2 or whatever to GRUB_CMDLINE_LINUX=””
3. Run whatever command distribution uses to generate main config file /boot/grub/grub.cfg. (arch: grub-mkconfig, ubuntu:updateâ€grub)
4. Reboot.
@ BloPa
So double clicking a registry file and rebooting is more complicated than:
1. Editing grub config file /etc/default/grub (or other bootloader).
2. Add nospectre_v2 or whatever to GRUB_CMDLINE_LINUX=â€â€
3. Run whatever command distribution uses to generate main config file /boot/grub/grub.cfg. (arch: grub-mkconfig, ubuntu:updateâ€grub)
4. Reboot.
FUD FUDd FUDD Elmer …. or BloPa or whateva…..
Spectre patches are in the Kernal not in GRUB, which I have Never even looked at because its not necessary.
Not even on some tired old has been Linux, like Mint…or *Pew*-buntu.LoL
Arch is for experienced folk not n00bs like me.
I dunno @ spectre2 but as someone wiser than I said:
“I’m NOT gonna worry about a vulnerability thats never been used in the wild”
I got the earlier Spectre/Meltdown patches in a new Kernal….ummm Where I’d guess they belong.Also point& click.
I also just wiped a w7 HD to install my Fave MX-18.1 on SFF HP 600 G1 it went on with 1 hiccup & then picked up 202 updates flawlessly.
I opened up my MX package installer picked 5 Browsers clicked install…
clicked the next tab over & installed FFx ESR & ‘brightness controller’ 1 at a time.
Didnt even need to go to Synaptic which isnt too difficult but is not Intuitive for a n00b. took maybe 3 hours total.
IIRC i.s was all point & click except my name & password. Try THAT from DVD with ANY windows available presently.
I do have 1 problem in my 2+ Years of using MX 16 thru 18, after an update, my Opera browser wont open on 1 machine,
not that I care particularly…..but thats it in 2 Y E A R s of using Linux MX!!!
Ok now where is the retpoline for windows 7 and 8?
I have doubts that Microsoft will backport it.
Sadly you seem to be right. It concerns all the users still using those two operating systems though.