Report: Non-admin accounts mitigate 94% of critical Windows vulnerabilities
A new report suggests that Windows admins and users could mitigate 94% of all critical vulnerabilities automatically by running non-admin accounts.
It is common sense that using standard user accounts on Windows, opposed to accounts with elevated privileges, is a good security practice.
The main reason behind this practice is simple: if a user cannot perform certain operations due to limited rights, so can't malware that attacks the system.
The recently released Microsoft Vulnerabilities Report 2016 by Avecto highlights how much of an impact the switch from admin to non-admin accounts could make on Windows systems
According to the report, 36% of all Windows vulnerabilities that Microsoft released patches for in 2016 were rated with the highest severity rating of critical. A whooping 94% of those would be mitigated by removing admin rights and running Windows with standard user accounts.
The figure is even better for Microsoft Edge and Internet Explorer vulnerabilities. Avecto reports that all, that means 100%, of Internet Explorer or Edge vulnerabilities are mitigated in a non-admin user scenario.
For Microsoft's newest operating system Windows 10, it would mean that 93% of all reported vulnerabilities would be mitigated by removing admin rights.
Avecto notes that Windows 10, dubbed the most secure operating system ever by Microsoft, had the largest total number of reported vulnerabilities of all supported versions of Windows. Windows 10 was affected by 395 different vulnerabilities, compared to 265 for Windows 8.1 for instance.
A simple change, switching a user account from administrator to standard, or creating a second user account with standard rights and using it predominantly, has a huge impact on computer security.
While the mileage differs from year to year, last year saw a mitigation percentage of "just" 85% for instance, it is clear that standard user accounts will mitigate a large percentage of attacks.
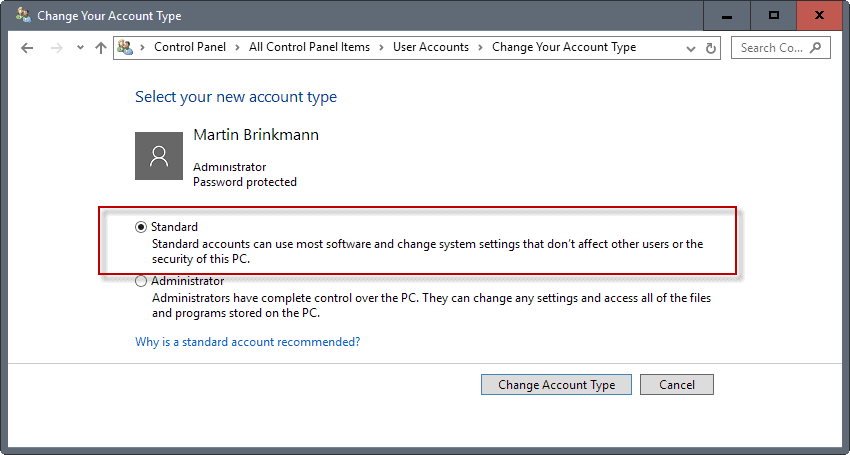
Configuring user accounts

You can switch any user account from administrator or standard in Windows, provided that you have access to an admin account.
I suggest you keep the admin account, and create a secondary user account that runs with standard privileges. You may also want to change the rights for any other user on the system from administrator to standard, if you have not done so already.
You can manage accounts in the following way:
- Use the Windows-Pause shortcut to open the System Control Panel applet.
- Select Control Panel Home, and on the next page User Accounts.
- Select "change your account type" if you want to change the account type of the signed in user, or "manage another account" if you want to change the account type of other user accounts on the PC.
- The second option lists all accounts on the next page. Select one, and then "change the account type" afterwards to switch from administrator to standard.
- You may create other user accounts as well. Either directly in the Control Panel, or by clicking on "add a new user in PC settings" if you run Windows 10 for instance.
Rule of thumb is that all user accounts that are used actively, e.g. by different family members or yourself, are standard accounts. You should keep an admin account around that you can use to make changes to the operating system that standard accounts cannot though.
You can download the 2016 report from the Avecto website. Note that you are asked to fill out a form before you can download the report.
Now You: Do you run a regular or administrative account on Windows?





















as I see it takes a lot of work to use a fucking standard user account, but I’ll try.
Users can’t make settings changes using a standard account such as a customized desktop. That’s my main gripe and the reason why I’ll stick with an admin account.
But the truth of the matter I think is that Microsoft would prefer users to run a standard account to reduce their own workload. They could subsequently reduce staff numbers (which would please the shareholders) and concentrate on analyzing all that lovely data they receive from Windows 10 users instead of having to concentrate on the next vulnerability just discovered in their leaky OS.
Don’t use administrator account on any OS, use non-admin. Also, if you have some valuable read-only data (music, movies, games, work etc…, you can put it in folders with restricted privs, that only admin can change, but everyone can read – this way that data will be safe from encryptors.
And 50% of functionality. Why doesn’t Microsoft do a better job of protecting the admin account? I have no problems running as an admin all the time. I have security and firewalls and have not been hacked. I just think there has to be a better way.
As someone who regularly gets calls that are the wrong number – my number is one digit off the state dept of revenue unclaimed funds – and I tell them it’s the wrong number and they STILL give me their name, DOB, address, SSN and other sensitive data – I can tell you that ‘vulnerabilities’ are nonsense. They don’t matter.
User Account Control was supposed to mitigate these exact vulnerabilities without breaking all the apps like using a standard account does. Breaking as in the average user doesn’t have any idea why some program failed to register or install when run from a standard account. He doesn’t know he can use right click -> Run as to elevate to admin. UAC’s auto elevation with a simple prompt improved the usability over manually elevating and entering credentials every single time. UAC has installer detection built-in and elevation is supported via app manifests. Plus if some app fails to auto elevate, you can always right click -> Run as administrator. I don’t see why anyone would use Standard user accounts after Vista. They were OK in XP. Set UAC to the highest slider and don’t blindly approve UAC prompts, especially from unsigned executables/untrusted publishers.
It’s the old argument of convenience versus security which are often mutually incompatible. I’ve seen situations where IT are so slow at responding to users requests that often there is a case of “shh, don’t tell anyone, but the admin password is ____”. I’ve even seen IT accidentally on purpose revealing the password knowing full well that once the user has learned it that they can do it themselves – obviously the blame shifts to the user in that case if things go wrong.
Not to mention the choice of admin password is often poor. Ask yourself this: If you locked yourself out of an account what would you do to get back in? If the answer is run Ophcrack and brute force the password or do some fancy footwork with another boot up USB / DVD and gain access, then so can malware! Just because you’re running an admin and user account separately doesn’t make you safe. Drive encryption, long random admin passwords, up to date patches and disabling “alternative means” of logging in go a long way to protecting a system. i.e. If Cortana or some other disability software is running on the login screen then it can be “swapped” out with your version of software, such as Windows Explorer and bypass the login screen. Drive encryption would mitigate this attack by preventing alternative boot OS’s from modifying the main OS.
Remember: There’s always a way around the system. Your best chance of preventing problems is to educate your staff, be on guard for things that don’t sit right, make proper backups (hey you have tried a restore – right? Do your backups work?), and have a disaster plan well rehearsed as to what you would do if the worst situation occurs. Virtualisation technologies can help immensly because they are easily backed up and quick to restore.
Non-admin will not prevent any encryption malware from working. Since those are the only relevant malwares right now it’s not that helpful.
But I do it anyway.
Have a look at SuRun. It makes running as a non-admin comfortable (hence the name… like sudo in Linux).
Interesting. However : seems to be a really non-standard way of doing things (unsettling when user permissions are concerned) ; needs learning ; seems not actively developed anymore ; site in German only.
http://www.dedoimedo.com/computers/surun-windows-7.html
http://kay-bruns.de/wp/software/surun/
I have been using a non-admin account since Vista. On XP, standard account support was buggy, but Vista made them usable. I have rarely had a problem with using a standard account on Windows, and the UAC prompt happens so infrequently (I could go weeks without seeing one) that it is just a non-issue. Also, since I’ve started using Ubuntu prior to the release of Vista, I have been accustomed to entering the password when doing rooty stuff.
During Vista’s time, I’d hazard that 70% of apps can work with low privilege. Most games at the time, though, required admin privilege so it was a hassle to run them. It got better by Windows 7, and by Windows 10 (I skipped 8), all currently developed apps are developed with lowest privileges in mind.
Maybe if I moved directly from XP to Vista, I might’ve been more resistant to using a standard account. But due to the fact that I used Ubuntu after XP and before Vista, I had a taste of how to use a constrained account. So yeah, I will only use standard accounts from Vista onwards. It made me conscious to the fact that doing stupid shit on my computer required me to input my password. It also made me circumspect on what apps I install. The added security against malware is just the icing on the cake.
I have always run Windows as admin. Been doing this for years and have never been infected — except for a few PUP things like OpenCandy that got installed as part of a program. I keep generally strong firewall rules, use a real-time malware scanner and several alternate on-demand scanners, now always scan downloads with multiple scanners before opening, have my OS and browser locked down in multiple ways and am careful where I go on the internet. No one else uses my computer — a critical advantage that helps in approaching things this way. And, I keep backups of my backups (disk images)!
I know none of this guarantees total safety, but it’s worked well for me and I just do too many “admin” type of things with my computer to put up with having my hands tied using a standard account. I want to easily drive my system where and how I want. Why have a sports car with a governor on it?
The managed risk has been a fair trade-off so far, IMHO. (fingers crossed…)
To each his own. If you practice safe hex, then you are generally safe, but still open to more attacks. The problem is that the newer nasty stuff coming out don’t require user interaction anymore. Ten years ago, you were safe running as admin as long as you don’t go to shady sites, open shady files, or do shady behavior. But now attackers booby trap ordinary sites with hidden iframes and payloads. Malicious files don’t need to be opened because they found other ways to attack Windows (like the WMF exploit, which only needs you to open the folder where the file is found using File Manager). There are probably other 0-day exploits out there waiting to be used. And then we found out that one of the highly touted ways to mitigate attacks (address space layout randomization) was not working as we thought it was.
As I see it, (to use your analogy) using a standard account is using a sports car with a manual transmission. It needs more user interaction to get the job done.
I made the switch to non-admin in my last reinstall one year and a half ago. I’m glad you published this, since I just complained at AskWoody’s a few days ago that I did not know of any study comparing infection rates for both types of accounts. (Although this study does not exactly do that either.)
Reading this, obviously I don’t regret the move. However, my experience is that Microsoft, and generally speaking the Microsoft expert community, do a very bad job of explaining the implications of running under non-admin for the single PC user. Neither Windows, nor Windows application software, are really tailored to such a situation.
If anything, the experience is easier than what I expected, and I blame Microsoft and Microsofties for not making this clear enough. In fact, you seldom have to log into your admin account. I was very surprised to realise that you can install software from within your ordinary account, just by clearing an UAC alert. The general Microsoft literature keeps saying that one of the admin account main uses is for installing software, so you tend to assume that you must log into admin each time you want to install an utility. That, in itself, can scare people away from living under non-admin.
However, living under non-admin has unexpected consequences. For instance, I lost visibility of what Macrium Reflect does. I have daily backups scheduled with it. When I worked under admin, I had an alert show up everytime the backup was about to start (and I could delay or suspend the operation). Now, not only do I not see that alert, but I don’t get the window showing the backup progress either.
Fortunately, I still have access to Macrium, and can launch it to read the logs and manually start backups if necessary. Not so with Sync Back, which I use for other, file and folder style scheduled backups. Sync Back activity is totally hidden from me in the non-admin account, and if I want to check that process or modify it, I need to switch accounts.
The way programs handle user accounts is not standard. User data configuration is particularly tricky. One common quirk is you install from non-admin, obviously you need to elevate rights, the installer asks if you want a desktop shortcut, you say yes, and it’s nowhere to be seen after install. That’s because the installer put it on the desktop of the admin account.
I’ve been slowly clearing up a mess in my company that previous “admins” left. 50+ coworkers, everyone has account in Active Directory and every account has Domain Admin privilages! This was probably done because we use a software that need write access to it’s own folder and it installs by default to Program Files, so you need admin account for this. First thing I did was to remove domain admin right and add accounts to Administrators group on computers, then I slowly remove admin right and check every software if it is affected and fix it (reinstall to user fodler, change privileges etc.
That’s also been my experience. I only have one (old, personal) application that requires admin privileges to run, and it runs just fine in a Windows 2000 VM.
I’m appalled at the whining about UAC prompts when installing software – that’s a security sensitive admin role. The proper response is G.T.F.U. !!
When you login to Windows 10 on your PC at home, for the first time, by the default it is an Administrator account.
Also, Windows 10 comes with a hidden built-in admin account.
You don’t need to use the Admin account to do everyday tasks such as checking email, social networking or playing videos/music online. Therefore, it is recommended that you switch the account to a standard account
What will happen in reality.
Step 1: User reads this and runs non-admin account
Step 2: User enables admin account to install ‘patched’ version of Photoshop or keygen
Step 3: User goes back to non-admin account
Step 4: “Man, how did I get infected this time! Windows sucks!”
Many people assume that computer users are stupid (except themselves). They also broadcast their point of view. One of the unintended consequences is that those “stupid” users tend to stay under admin, since the implied suggestion is that admin is for the alpha geeks dishing out that sort of statements, while the great unwashed masses should stay under non-admin where they belong.
Incidentally, Windows sucks.
I’ve been running with a standard account for a decade or more. If I want to make system changes (something seldom needed), then I pop over to an admin account–no problems at all. (But I don’t run Windows much anymore.)
It’s such a bother to have to enter the password every time there’s an admin rights prompt though. I’m keeping admin account.
Just use this portable tool to avoid to enter the password every time
http://www.sordum.org/8727/runastool-v1-0/
Too bad the password can easily be sniffed when the passwords are picked up by the API.
Wow ! Thanks ! That’s exactly what I had been looking for. But is it safe ? Does it lower the PC’s resistance to malware, compared to what the unmodified non admin account does ?
Im with ya on this,feel the same way,having to login period is a pain in the A,the less the better for me,keeping admin account aswell,my feelings toward MS in genral is already pretty nasty,ill do what i want with what i can,all the security bs,if one is savy,responsible and knows how to surf and download things and be safe with risks sure dont need some bigwig MS telling me wtf to do! its all about the NSA pushing all this in the first place,nothing is free,though a dam good OS after stripping the hell out of it and keeping up with the slipins and updates,changes is literly tireing and a job in itself.
PS.keep up the great work martin,your the best along with woody,much regards keeping us informed,thank you for all your hard work.