Netgear releases first final firmware updates for router security issue
Netgear has released the first batch of production firmware fixes for company routers affected by a serious security vulnerability.
Cert issued a warning on December 9, 2016 that several Netgear routers are vulnerable to arbitrary command injection. Cert listed only two router models but has since then added other models to the list.
Currently, the Netgear routers R6200, R6250, R6400, R6700, R6900, R7000, R7100LG, R7300, R7900, R8000, D6220, and D6400 are affected by the vulnerability.
The attacker needs to convince a user to follow a link to a specially crafted web page. An attacker on the same local area network may do the same by issuing a direct request using the syntax http://<router_IP>/cgi-bin/;COMMAND.
The attacker may in either way execute commands with root privileges on the affected router. The command http://RouterIP/;telnetd$IFS-p$IFS'45' will open Telnet on port 45 for instance.
Netgear router firmware updates

Netgear has released firmware updates for affected routers. The first firmware updates the company released were labeled beta. The first four production firmware (stable) were released for the models R6250, R6400, R7000 and R8000 now.
- R6250 Firmware Version 1.0.4.6
- R6400 Firmware Version 1.0.1.18
- R7000 Firmware Version 1.0.7.6
- R8000 Firmware Version 1.0.3.26
Additionally, beta firmware releases for the following Netgear routers are also still available:
- R6700 Firmware Version 1.0.1.14 (Beta)
- R6900 Firmware Version 1.0.1.14 (Beta)
- R7100LG Firmware Version 1.0.0.28 (Beta)
- R7300DST Firmware Version 1.0.0.46 (Beta)
- R7900 Firmware Version 1.0.1.8 (Beta)
Netgear notes that it continues to review its entire portfolio of routers to find out if other router models are affected by the vulnerability as well.
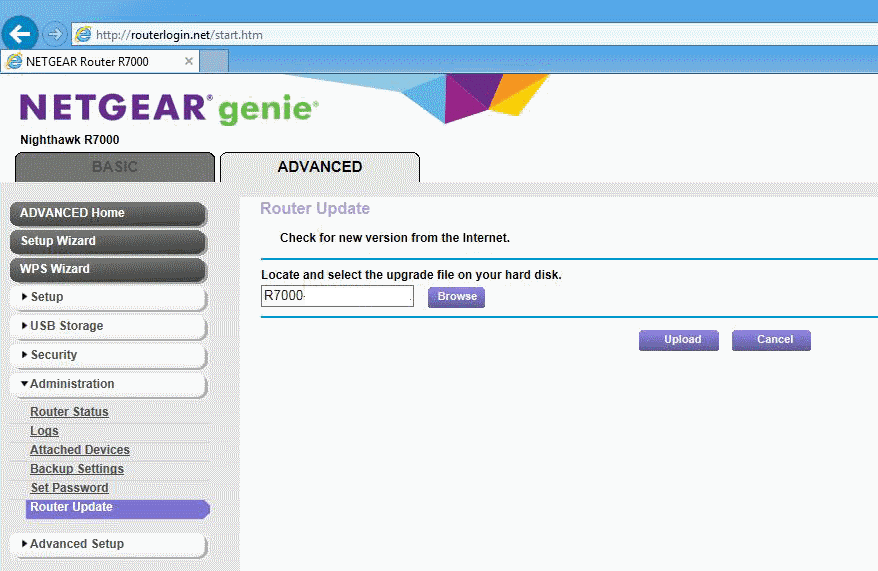
You find instructions on how to download and install these firmware updates on the router on the support pages.
The instructions are all very similar. Download the firmware (with a .chk extension), to the local computer system. Log in to the router via http://www.routerlogin.net afterwards, and select Advanced > Administration > Firmware Upgrade. Click on browse, and then on the firmware update file that you just downloaded. Select upload to upgrade the router, and wait for the process to complete, and make sure you don't power off the device or change its state during that process.
The main support page on the Netgear website that lists all affected routers and links to firmware updates is available here. Netgear will update the page when it releases production firmware for routers with beta firmware, and will also list any new router model affected by the vulnerability as well there on this page.



















I have a Netgear R6300v2 Router. I tried to find out if it is involved in this Router fiasco going on now,but i don’t see anything regarding my Router. Any help or Info please?
The lesson stays the same: never buy a router without DD/Open-WRT support.
Updated. Thanks Martin.
Too late Netgear! You pushed me to move to Tomato and I am loving it! Now that I know how easy it is, and how superior the functions are, I doubt I will be buying a new router again, just a used one I can install a custom OS. So, thanks!