Behavioral Keyboard Privacy add-on for Firefox
Behavioral Keyboard Privacy is an experimental add-on for Mozilla Firefox that prevents you from being profiled based on how you type.
Did you know that there are companies out there that track you based on how you type? They have developed methods that track your typing patterns; how fast you type, how long you dwell on keys, how long it takes for the next key to be pressed and so on.
Basically, all these companies need is enough data to identify you based on how you type regardless of whether you are using the computer for the first time or regularly.
There is no need for cookies, supercookies, or other tracking mechanisms anymore with behavioral keyboard analysis.
The main issue with this from a tracking company perspective is that data is needed to create profiles and identify users. If you visit sites that don't require input, or only minimal input, then there is little chance for those companies to create your tracking profile or track you.
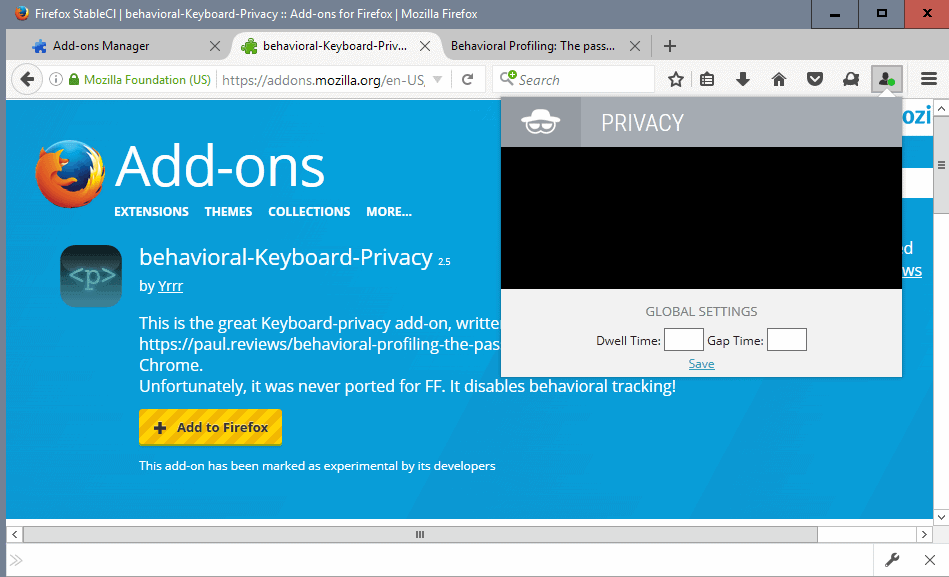
Behavioral Keyboard Privacy

We talked about this back in 2015 when Keyboard Privacy was released for Google Chrome that took care of that by changing dwell and gap times to constant values.
Behavioral Keyboard Privacy brings the functionality of the Chrome extension to Firefox. It has been created by another user, and it is not entirely clear if it is a port of the Chrome extension.
The functionality that it provides is identical to the Chrome version. It sets the dwell time and the gap time to 200ms by default to protect against tracking methods that try to create a profile on you based on how you type.
You can click on the icon that it adds to Firefox's main toolbar to change those intervals. You may run into issues if you pick too high or too low values for those intervals.
The add-on runs in the background and should not interfere with your typing in any way. This may be the case if you change the default interval, but it is easy enough to modify the intervals again if that happens.
Closing Words
It is unclear how widespread behavior keyboard tracking is, and by how many sites and companies it is used. Behavioral Keyboard Privacy provides you with an option to block these tracking attempts. If you believe or know that the tracking is widespread, you may install the add-on to stop it cold in its tracks.
Even if a company managed to create a profile using typing data already, it won't be able to link it to your typing once you install the extension.


























So which websites are using keyboard tracking tech? and what about using addons like Ghostery or NoScript? Are they enough to block keyboard tracking?
“further more, you can skip the search box entirely. all you need is
https://www.google.com/search?q=
with your search term following the =. use + for spaces”
You can even bookmark the following address and add a keyword to the bookmark data:
https://www.google.com/search?q=%s
If the keyword is “g”, you can search for hot grannies on Google by typing in the address bar:
g hot grannies
But Google will know your hobby. Better use Startpage…
ewwwww… g g string hot grannies xD
Paul Moore just abandoned the chrome add-on and never gave a reason.
1. Grab a list of NSA Keywords, as password, bomb, attack…
2. Use ascript to open a google search every other minute and search two of these words at random.
3. Let GOOGLE, INC. now ALPHABET track your scripted, random searches.
If one out of 100 users of GOOGLE products did so, GOOGLE now ALPHABET will get useless BIG DATA out of their customers.
> Use ascript to open a google search every other minute
Good luck with that. Nowadays, googlesearch has a hair-trigger bot detection mechanism. Across recent months, with increasing frequency, even some of my manual search sessions trigger repeated interstitial captchas. Not only can you wind up with needing to passhtru a captcha challenge prior to viewing each search results page, by solving a captcha too quickly you can wind up having repeated captchas thrown at ya (apparently toward a goal of not serving you more than xx results pages per minute).
I’m hit with the captchas excessively often b/c I’m running GooglePrivacy browser extension? If googlesearch isn’t seeing clickthrus from me (via their embedded redirect links), understandably my repeated requests might seem bot-like. In the absence of clickthru data, and given the fact that I’ve disabled as-you-type search suggestions, I don’t login to google accounts, I block GoogAnalytics et al via RequetPolicy, I disallow WebSocket connections yadda yadda…
I suspect that, along with the nature of my search query(ies), “behavioral keyboard analysis” based on time-to-solve captchas (without per-keystroke timings) is probably STILL able to reliably fingerprint me. I am: a fast typist, hailing from a fixed IP with very few other users on the LAN. Although my typing is FAST, it ain’t always accurate ~~ a profile could be built based on my fat-fingered typos while solving captchas, my occasional dyslexic quirks, my apparent color-blindness (apparent, based on frequently getting tripped up by captchas displaying red text), my tendency to struggle with recognizing twisted SERIF characters displayed within captchas… and ESPECIALLY based on my kneejerk reaction to being presented with a captcha bearing yellow text on white background: fcukdat — submit it blank and get a fresh, more readable, captcha. All things considered, and especially because no smartphone/android devices exist within this household, I reckon my usage stands out as a potentially-interesting anomaly.
Haa haaa, that smacks of the good old days of your ISP and Carnivore (look it up young’ns) when every email you got always had a signature and a block of trigger keywords below it. Not sure it worked back then and not sure it would make a difference these days.
Computers are now so fast and parsing text to speech has come along long way so anything with blocks of keywords would be skipped in a heartbeat.
” get the sand out of your mouth, my dear Parker?! Like Champagne on the sea side after a sweet battle with the beloved … ”
And now I am spooked! Good job, we’ve gone through all possible translations and we can now expect to score above 900 on the TOEIC.
If I change my mind to say that it was indeed a mistake, one I tried to correct by letting my ego participate, will it get the sand out of your mouth, my dear Parker?! Like Champagne on the sea side after a sweet battle with the beloved …
I doubt it. Too late. Damned, not my day.
Drat! I thought it was a particularly tasty translation mistake. Now it feels like sand in my mouth :(
That’s where I got my inspiration from, Parker!
Same word for a spy and a ghost seemed relevant, then came in Casper, the friendly spook :)
Easy, too easy, almost childish. I’m not perfect, not far but that ain’t it, yet!
This said, “Casper” would be a great name for an secret agent. “Secret Agent Man” as sung by Austin Powers… “Secret Casper Spook”.
Hum…
Not THAT kind of spook xD
http://www.wordreference.com/enfr/spook
Casper, the friendly ghost,
The friendliest ghost you know.
Though grown-ups might
Look at him with fright,
The children all love him so.
He always says hello (Hello),
And he’s really glad to meetcha.
Wherever he may go,
He’s kind to every living creature.
Grown-ups don’t understand
Why children love him the most.
But kids all know
That he loves them so,
Casper the friendly ghost.
“a block of trigger keywords” … we called them “spook food”
MI6 or Am I not needs people like you :)
If anyone has any doubts about their self-worth, all they have to do is look at the effort being made to spy on them to believe otherwise.
Not sure. Companies are interested in a user’s wallet or in a user’s privacy as some men are interested in a woman’s morphology : that and that only.
How about changing randomly our own behavior with devices? Once I’ll type slowly, then fast, same with the mouse, modifying our vocabulary, syntax, rhetoric, trying to appear once as a male, then a female, induce divergent religious, societal and political opinions, appear here calm and there mad … a lot of work for anyone who isn’t naturally predisposed to schizophrenia :) Remains when applicable the IP… let’s just let them imagine a same computer is shared within a hippie community, or a veteran’s organization, if not by a Quaker family … let one’s imagination fly!
you can try to play a ‘type’ , but still that will be you who plays that type.
for now these methods might be fooled, and take you for another person.
but still you will have some unconscience behaviour that you’ll apply in all types, or they will grow to each other.
or you’ll forget who you supposed to be on this or that site.
Nobel thought and on I use in some degree. but typing and attention behaviour is hard to change.
Another one I use is quite the opposite, account share across multiple people.
And that is where these tracking methods will tell us apart.
I forgot to mention this ; what I call “the guilty child syndrome”. At school the kid among his friends who is guilty when the teacher asks “who did that?” will belive unconsciously that he is recognizable; it’s not only a question of morality, he truly feels the teacher may and will identify him.
Same when we try to hide. We may believe others know more than they actually do. It is then required to try to know what the other(s) may know about you, hence what they ignore, but never change our behavior consequently. Change our behavior, but later on and in different schemes which, when added and summarized with previous ones, lead to inefficiency of previous profiling. One has to consider time and not an immediate barrier. Another thing is to incarnate an identity, like an actor, and never try to correspond to what you believe your role should look like.
Ann, this “unconscience behaviour” you mention, with which I totally agree, is perceptible by trained brains or by people who are extremely sensible even if, with lack of knowledge, the latter may perceive differences without being able to characterize, define them. I doubt this ability, when extreme, ever be in the area of AI possibilities.
The main “advantage” is that this kind of fingerprinting targets the user, not the machine. Whether you are at home, at your workplace, at a friend’s place, in hotels or whatever. It could figure out if you have guests at home and who they are, etc.
That type of fingerprinting requires JavaScript. Whenever you allow JS you can just consider yourself fingerprinted, but user fingerprinting is a class above machine fingerprinting. In that sense this add-on is useful, but only if several people are using it in your area. (Or with your VPN) You can only hide within a crowd, and if you’re the only person using this add-on, it’s not that much better than if you didn’t use it at all. The ideal add-on would provide random time intervals constrained to realistic values found in the wild. THEN it would fix the problem.
I think Firefox in its default configuration does a number of things to mitigate timing attacks like this one, such as reducing timestamp precision for events, but that is not enough. The Firefox fork Tor Browser does much more but I haven’t seen a study showing how efficient it is (there should be some though). Mozilla has a project where Tor Browser privacy improvements are brought back into mainstream Firefox. Hopefully this project will not lose steam.
So meanwhile, since with fixed time intervals and only 20 users (?) this add-on is not that much better than not having it, the only solutions are to disallow JS or write outside the browser and copy/paste when finished. (Especially on Facebook.) Also disable search suggestions.
I hope this add-on gets more users and improvements though. And I hope Firefox actually implements something like this in the future, if only as an opt-in. (e.g. Tor Browser’s privacy slider)
But, I think what Parker is getting at with the “hide in the crowd,” the fixed paced typing will be the only one at that IP address. Unless all or most others using that IP (shared wifi) are also using the add-on, it can only be that one person at that time and PC.
However,no fixed paced typing is going to convict anyone unless a Prosecutor can tie that particular person to that IP address at that time and that was the only fixed pace typing. Even then, a tough row to hoe I’d guess.
But for ad tracking it is fine, no harm if they show ads to someone who looks like that person because of their typing characteristics.
What we really need is a catch-all add-on between our PC and data being sent back to a site that fixes typing speed, normalizes all fonts to Times Roman, all images to a single format, 72dpi. and 4:3 ratio etc. It is what we send back they are using. Normalize that to the crowd as a default etc and we are getting somewhere.
@Parker Lewis – see the Tor Uplift Project ( https://wiki.mozilla.org/Security/Tor_Uplift/Tracking )
// [Assigned]: reduce precision of time exposed by javascript
// https://bugzilla.mozilla.org/show_bug.cgi?id=1217238
// user_pref(“javascript.options.privacy.reduce_time_precision”, true);
FF in it’s default does nothing
I believe I’ve seen a number of timing attack mitigations implemented in Firefox over the years. Here’s one: https://www.mozilla.org/en-US/security/advisories/mfsa2015-114/
” They have been addressed by reducing the resolution of the performance.now() API to 5 microseconds to remove the precision in resolution available to attackers. ”
There should be more. But yeah it’s nowhere near as good as what Tor Browser provides, and I’m almost certain none of the measures taken ever aimed to prevent keyboard typing fingerprinting. Unless realistic behaviours were to be implemented (not a chance IMO), mitigating timing attacks involves compromising with performance, smoothness and that kind of things. So it has to be opt-in for the browser to stay competitive. (But easy to opt-in. Tor Browser once again does it properly.)
“You can only hide within a crowd” … but if the values are always the same the hint can be that a crowd is always using the same value, hence that the user’s or the group’s data is made obsolete by an anti-fingerprinting device. I mean, with continuous identical data the issue is not the number of users but rather the presence of an anti-fingerprinting device. No?
Incertitude. What are we sure of? What do we require to be sure of? Evidence? Unfortunately more data there is more stats are aimed to replace evidence by high probability. People have been sentenced to death with high probabilities of their guilt, those who perpetrated the 9/11 attacks have been unconsidered on the basis that a CIA agent’s alert in Arizona did not feed the probabilities by a reasonable amount of… probability. You may know my true love for America but one has to admit that there is in American culture this trend to mistake certitude with probabilities, and this is relevant of a deep dislike of this culture for doubt, uncertainty : everything must be known and if not must ba considered as known on the basis of high, extremely high probabilities. This is a cultural failure, IMO. America needs to read and learn Spinoza, to resume with a smile :)
Parker, that’s why I wrote “[tracking] spend their time combining fingerprinting data to reduce that lack, to enhance the probability of certitude.”
You write “[…]only one more bit of information is needed to separate the two.” Yes if that bit is not applicable to both be it at different times only. Susan and Tom cannot be differentiated with the keyboard pattern but they can be, say with the mouse pattern. And so on. OK. Of what I’ve heard patterns don’t identify formally they only squeeze down the stats when added one to another : break one pattern and you’ll reduce the probability, break two and you’ll reduce more. Break with fluctuating values and you’ll switch from hiding to misinforming. We’re in the “guilty child syndrome” I mentioned hereafter. It is the addition of patterns which narrow down to an identity, not a pattern by itself, or the pattern should be conceived in such a way that it would be able to analyze what Ann calls hereafter “”unconscience behaviour”, which is not for tomorrow.
Ah! I see what you mean by evidence vs statistics. Well this is forgetting that typing pattern is just ONE information. When it doesn’t uniquely identify you and there are say, 2 people with the same pattern, only one more bit of information is needed to separate the two.
So for 2 different people on 2 different computers it’s pretty easy to get “evidence” with a group of 2. For people using the same computer, browser and profile it’s probably harder, but I haven’t given it much thought.
Indeed you can try to hide several persons who use the same machine with this add-on, good point :)
I’d say this is the main point of interest of the tool as it is right now, unless we’re missing another one.
OK, Parker, of course a limited number of a same pattern reduces the crowd, but as I see it the main point is less statistical than that of an identity’s evidence : be the group consisting of 2, 2,000 or 20,000 the fact is you are not identifiable once you may be another. Statistically within 2 you are identifiable with a 50% chance of success or… failure. If my wife and I, or my sister and I use the same computer our use of the keyboard could differentiate us, with the above add-on it would be impossible. I’m focusing on evidence not on stats. And tracking hates lack of formal evidence, even if they spend their time combining fingerprinting data to reduce that lack, to enhance the probability of certitude. That’s how I see it.
you can only hide in the crowd , but for each user that use this the crowd gets bigger.
if the crowd uses the default 200ms, then you are allready in a crowd.
if you want a personal delay of 173ms, then yes you’ll be still fingerprinted ;-)
Start the crowd, so start with yourself.
If the values are always the same for all users that does make a crowd to hide in, that’s what Tor Browser tries to do.
But the group that uses this add-on is so small at the moment that using it is almost the same as not using it. You are unique in both cases, i.e. you have two distinct unique typing patterns instead of one. It doesn’t matter that one of them is not your real pattern. (If you’re the only person wearing a red coat in a park, seeing your face isn’t required to find you)
On the other hand if the add-on mimics reality, it doesn’t constrain you within a group any longer, you have infinite unique typing patterns, and so you can’t be fingerprinted through keyboard timing attacks.
The add-on would have to make sure it only provides timing patterns that could belong to a real human, but also understand when to reset “identity”. (On user demand ? at session end ? On IP change ?)
It sure is easier and less error prone to create your own crowd with fixed values, but that is a luxury only widely used products can afford. (Or complete solutions like Tor)
That said it’s very hard to provide realistic identities when many factors are involved, but if it’s “just” keyboard typing it should be manageable.
Interesting article. It’s quite possible that in the future more websites could use this type of tracking to identify people who use ad-blockers and avoid storing cookies. Once the tech giants jump on board it shouldn’t take long until this type of tracking is widely implemented on sites with keyboard input.
There are also other “User Behavior” tracking methods – eg mouse movements (think of speed, direction of mouse, indicators of screen size and button locations etc – high entropy but not an exact science yet) – can’t remember exactly where I read up on it all. Not to mention click speeds. Besides basic vectors, there also more advanced issues of writing styles (and frequent typos/corrections). [Note: not to be confused with keyboard hardware fingerprinting]
You can see that on facebook if I’m correct; some posts you see got this fb address upon hover and original source at the end, on second mouse move it disappears and shows just original address.