LastPass Remote Compromise vulnerability
LastPass has a bunch of critical problems of which at least one allows attackers to compromise the password manager remotely according to Google researcher Tavis Ormandy.
LastPass is one of the most popular online password management services on today's Internet. The service offers extensions for various browsers, mobile apps, and dedicated solutions for various operating systems and devices.
A full report was sent to LastPass by Tavis Ormandy and it appears that the company is working on analyzing and fixing the issues at the time of writing.
The issues have not been disclosed publicly yet. While that is the right thing to do until they are fixed, it means that LastPass users don't really know if the issue can be mitigated until a fix is provided.
Update: LastPass released a security update for the Firefox add-on. According to a blog post on the official site, an attacker could lure a LastPass user to a malicious site to execute LastPass actions in the background without the user knowing about them. This has been fixed in LastPass 4.0 for Firefox.
Additional information about the reported issue are available on the Project Zero forum over at Chromium.org.
LastPass Remote Compromise vulnerability
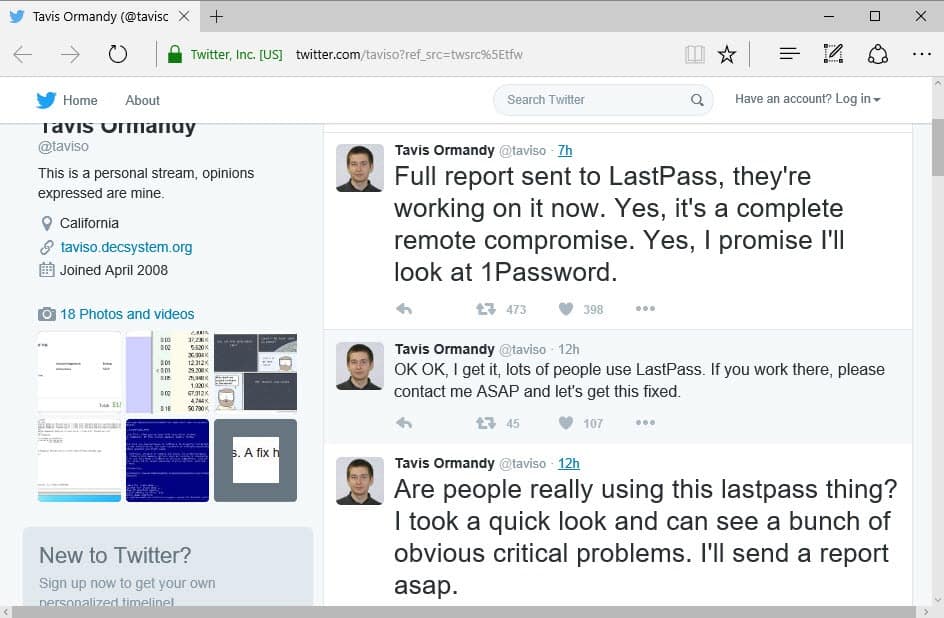
The only information provided are the following two tweets:
Are people really using this lastpass thing? I took a quick look and can see a bunch of obvious critical problems. I'll send a report asap.
Full report sent to LastPass, they're working on it now. Yes, it's a complete remote compromise. Yes, I promise I'll look at 1Password.
Considering that, it is unclear if features such as two-factor authentication or use of other security add-ons protect users and data from attacks. In fact, it is not even clear if LastPass' network and infrastructure, the browser extension, mobile apps or other products are affected by the vulnerability.
It can very well be that only the browser extension is affected, considering that it is the most likely that Tavis took a look at due to its availability for the Chrome browser.
The security researcher set his sight on the next password manager, 1Password which is up next according to a Twitter message.
Password managers store critical data. This makes them one of the most important programs for a user, and a lucrative target for attackers.
The disclosed security issue is not the first incident in LastPass' history. In 2015, LastPass confirmed that it detected suspicious activity on the company network. Only recently, another issue was reported and fixed that allowed attackers to extract passwords using the extension's autofill functionality.
LastPass is usually very responsive and fast when it comes to the patching of security issues affecting company products. We will update the article when new information come to light.



















Well, it involved phishing and Firefox. So, if you got hacked, then you had no one to blame but yourself? (“this lastpass thingy”, huh–calls into question his awareness of security to begin with)
Firefox extension just updated to 4.1.21a so I’m guessing the issue has been resolved.
Mine is still showing 3.1.1. That’s the same if you go to the Add-on page. It shows last updated March 4, 2016.
Right, LastPass issued a statement that the reported issue in the Firefox add-on has been resolved. I have updated the article to reflect that.
The recent report only affects Firefox users. If you are a Firefox user running LastPass 4.0 or later, an update will be pushed via your browser with the fix in version 4.1.21a. If you would like to update your client proactively, you can update with our download link here: https://lastpass.com/lastpassffx. You can check which version you are running in your LastPass browser addon, under the More Options menu in About LastPass. If you are running LastPass 3.0, you are not impacted and do not need to update.
Maybe update the article please?
palemoon users are at risk they not able to use newer version of lp
I’d suggest Pale Moon users to use a password manager that fully supports them (unlike LastPass). One example is the excellent Sticky Password (full support for Pale Moon x86, but not the 64bit version – at least for now).
LastPass already posted a message on this topic. It only affects Firefox and a fix has been issued
https://blog.lastpass.com/2016/07/lastpass-security-updates.html/
Say what you want, they are quick to fix issues that are reported to them.
This is a key example for why SQRL should be adopted. https://www.grc.com/sqrl/sqrl.htm
nah, another “smartphone app”-based login “solution” can not be good. And using QR codes for logging in is even worse.
Depending on how complex the code is the audit can take 1 or 2 years (if it’s an good one). That was the reason I not switched to VeraCrypt immediately, because every forked it and cloned it with some changes here and there .. The audit takes time and just because there is a fork not means anything until there is proof.
I’m a friend of offline databases, but we hadn’t that much troubles if they would encrypt there databases, so no matter what even if something is compromised no one would get access to it.
I use keepassx and i think its insane to use an online password manager and this clearly shows why.I much prefer all my passwords stored locally in an encrypted database.
good for you, but who really cares what you do.
I just love these “white” hacker that tells a company to “contact them ASAP”. So high of themselves that they won’t even bother writing to support it seems.
I don’t doubt he found something, but the way he discloses them is highly egotistical.
Hello Everyone:
This latest incident makes me even MORE skittish about using these Password Managers . . . I’ll keep using my passwords the Old fashioned way – – Thank You Very Much!
i
I don’t think this article should be released just because of a tweet of a Google reasearcher. It should be when the Google searcher released a detailed report. Twitter account could be hacked or something else. Just my opinion
I use KeePass in Dropbox. I wonder he will take a look at it.
that’s already had a few issues.
https://news.ycombinator.com/item?id=9727297
https://www.engadget.com/2016/06/04/keepass-wont-fix-security-hole-due-to-ads/
http://arstechnica.co.uk/security/2015/11/hacking-tool-swipes-encrypted-credentials-from-password-manager/
Would love him to do so, but I doubt it. KeePass is of no interest to Google and its products.
I think I read recently that the EU is to audit KeePass code ?
Yes they will, but no word yet on when this will be done.
I have little sympathy for people who put all their passwords in a known online location with millions of other users, and who think the system will never fall to an attack. It’s a huge target. Of course security will be breached from time to time. Idiots.
we don’t give a fuck about your sympathy or anything else really.
Jack, your the idiot callig everybody else idiot’s. You think we give a shit about your opinion, we don’t.!!!