How to chain VPN servers
VPN Chaining is a technique in which multiple virtual private network (VPN) servers are chained to improve online privacy while on the Internet.
Basically, what it means is that you are not connecting to a single VPN but to multiple ones in a layered system that looks like Your PC > 1st VPN > 2nd VPN > Internet.
Before we take a look at the how, we should discuss why you would want to do that. One argument is that you cannot trust any of the VPN providers out there.
While most claim these days that they don't log, there is virtually no way to prove that this is indeed the case.
And even if they don't log user activity, they may still be forced to cooperate and log activity of certain users connecting to the system, for instance when forced to do so by a court of law or when coerced.
VPN Chaining improves privacy by connecting to multiple VPN servers operated by different companies who -- preferably -- operate in different jurisdictions.
The advantage is that it becomes increasingly difficult to track users when they chain VPN servers.
There are disadvantages however, for instance that the setup is complicated, that maintaining multiple VPN accounts is more expensive than just one, and that there is still a possibility of being tracked.
| Advantages | Disadvantages |
| Improved privacy | complicated setup |
| more expensive (unless free services are used) | |
| slower speeds, higher latency | |
| Possibility of being tracked is still there |
How to chain VPN servers
Unless you operate all VPN servers that you want to chain, you cannot simply connect to the first VPN in the chain and be done with it.
Connecting to multiple VPNs simultaneously on the same device does not work as well which that leaves virtual machines as the best solution to get the ball rolling.
Basically, you connect to one VPN on the device you are using, and to others that you want as part of the chain in virtual machines.
A simple chain would look like this: PC > 1st VPN > Virtual Machine > 2nd VPN > Internet
You would have to perform all activity using the Virtual Machine to take advantage of the chaining.
How it works:
- Download VirtualBox from the official website and install the virtualization software.
- Download and install an operating system, Linux Mint for instance, in VirtualBox.
- Get accounts at two or more VPN services. You get big discounts at Ghacks Deals currently for select VPN providers.
- Connect to the first VPN on the device you are using.
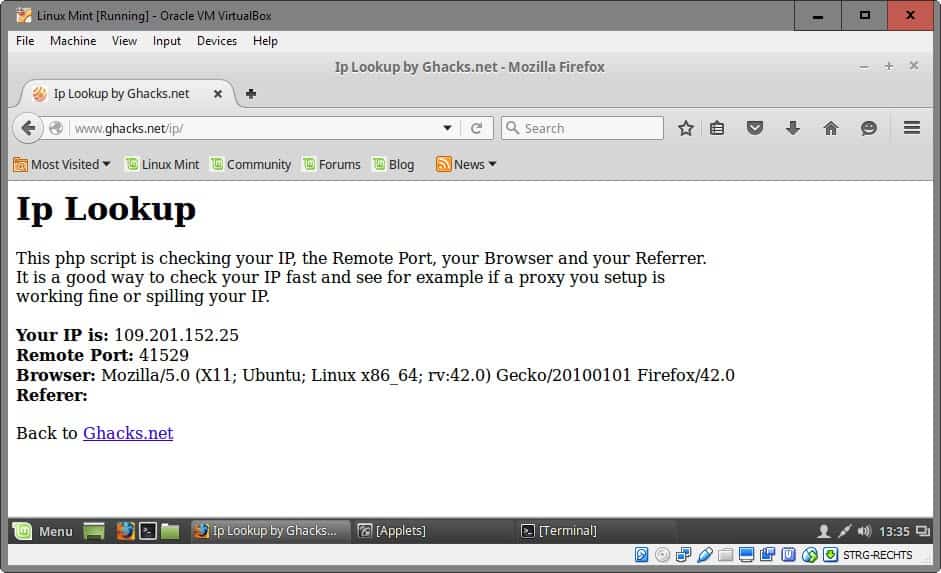
- Connect to the second VPN in the Virtual Machine. If you have followed the suggestion above, connect to the VPN using Linux Mint.
You can verify that the VPNs are chained by checking IP addresses. You will notice that the host device returns a different public IP than the virtual device.
Crazy chaining: you can add as many VPN services to the chain as you like, but you need to install a virtual machine inside the virtual machine for each of them.
Installation of VirtualBox and the host operating system should not pose problems to most users. The installation of the VPN service on the other hand may, but most VPN providers offer instructions on their web pages that detail the installation process on various operating systems including Linux.
Closing Words
VPN Chaining improves online privacy and while it does not offer 100% protection, it offers far better protection than a single VPN (which in turn offers better protection than connecting directly to the Internet).
Now You: Do you use a VPN?



















Buy 2 or as many 10$ routers you want . Configure each for a vpn service. Chain them. End of story….
Hello Martin, i am your italian fan!
Great guide, it runs perfectly.
If i can leave a link, i made this guide in Italian Language one year ago, happy to know that it’s the same.
http://www.drogbaster.it/fornitori-servizi-vpn.htm
By using a Chromebook and a router with a VPN client I am using 3 VPNs simultaneously for all internet traffic. The router (Asus DSL-AC68U) provide the first VPN and this is the only traffic my ISP sees. The Chromebook has a built-in VPN client too and by using an encrypting proxy Chrome extension (Zenmate) all traffic is encrypted since the Chromebook’s only connection to the Internet is via the Chrome browser.
Without any VPN running my Internet connection is a stable 37 Meg. With all 3 VPNs running speed is somewhat variable (2-35 Meg) When speed is slow I may disable the VPN which is slowing down the connection or by disconnecting and reconnecting it often returns to an acceptable speed.
So, this 3 hop VPN is much faster than Tor (also 3 hop) but may not offer the same level of privacy.
That’s interesting. SoftwareVPN –> OS-VPN–> NetworkVPN. Are you sure that they’re really chained? I only ask because I don’t know. I assume you can easily test (some of) it by checking your ip from 1. chrome browser (zenmate), 2. from chrome browser with zenmate disabled and 3. from another device on your network. How can you test that Zenmate doesn’t bypass your OS VPN? The router I’m not worried about – btw, have you DD-WRT’ed it?
check out lahana cabbage router for a way to use amazon ec2 free tier and vpn access (http://lahana.dreamcats.org/) looks interesting but yet to try myself
Vpn is great for an added layer of privacy at your home. For being anon,don’t use your computer, registered with the manufacture in your home. Single point of failure in Pants example, the lazy human. Don’t do crap at home kids.
Or you could just use Tor.
For now I have no interest for a VPN because as I see it on one hand you have no true certitude of privacy (original IP doesn’t vanish, it is always in a database) while on another hand speed is always the price to pay.
As I see it, if VPN chaining is interesting by the induced ‘onion’ scheme (Ã la TOR) it must have a consequent effect on speed. Moreover, as well as good wines are served first followed by the lesser, the first VPN in the chain must be the one we trust the most. “The one we trust the most”… do we ever trust a VPN totally? I cannot imagine paying 50-100$/year for “quality VPN” to discover later on my IP was logged and maybe shared…
Finally, if I struggle for privacy I dislike secrecy, this is here a leitmotiv. I do not dislike to be recognized but I do hate to be followed. I dislike recognizing a user whom presents himself under a different identity on chats and forums (I even know French forums where it’s sort of a game). Funny and relevant of a user’s profiling skills but globally irritating as so childish, not to mention the lack of respect for guests.
I don’t really care of data built on my IP to be frank, as long as it is not associated with my civil identity and physical home address, these two being reserved exclusively for administration and commercial transactions (still with extreme caution). I receive no spam as I use disposable email addresses and I am not bothered with tracking ads as I avoid both trackers and ads with good applications, at least which have proven to be efficient up to now. After that I won’t break my head to surf anonymously and therefor will avoid as well remarks such as “How can you be in New York when your system shows the time of Paris?” : if you want to play it excellently you have to consider far more than a moving IP. Too much work for me, I’m no James :)
“Good wines are served first followed by the lesser.”
Ha ! We could start an epic flame war over that. I personally believe it to be just the opposite. Unless you plan to get so drunk with mouton-rothschild in the first place that you could not make the difference between château Yquem and Listerine afterwards, but then you wouldn’t deserve a sip of mouton-rothschild (or anything worth drinking) anyway.
Yeah, Ghacks is a place where not only Firefox and Linux get discussed to death, but also fascism, communism and the proper way to absorb great wines. Get used to it.
“I don’t really care of data built on my IP to be frank, as long as it is not associated with my civil identity and physical home address”
If you ever have ever let google on your wifi (eg from your smart phone, and it’s pretty hard not to!), then they already pretty much know your address. Your phone (android) will detect/collect wifi names of all your neighbors as well (and when you move around town). Google has extensive wifi name databases, and they use them. It’s even worse of course if you allow GPS, and of course if you tie your real ID to any google services.
I use ncr (no country) google searches. A few months ago a friend visited and jumped on my wifi. I didn’t think much of it at the time, and the 24 hour nudie beer session with loud music and shaved goats didn’t help, but now all my google searches know my city, which is pretty obscure (before they could only guess my country and pinpoint me to one of three main centers, 100’s of miles away) – at the end of each google page is a “city” refined search link – that was never there before. And the ncr no longer works, I am forced to use my regional/country’s google search. Pisses me off. I have no google accounts and have never allowed any google analytics or tracking of any kind, or cookies, or click tracking and so on. As I said before, all it takes is one mistake and they can join two dots and its game over.
in my country IPs are dynamic except for corporate ISP, just restart the modem to get new IP. most ISPs even don’t give public IP. so no worry about Google tracking my IP, the IP will keep changing :)
With the PC (free of a wifi card) I use Ethernet and for the phone I use only an old mobile, no smartphone, which surprises my friends but which is my choice. At home I love the tool, the computer and the networks, but once outdoors I dislike forgetting reality, that of people, sounds, city lights, nature, colors and sounds, not those of a tiny screen with horrible sounds but those of my environment. Mobile phone here only for phoning, no Web, no cam, no micro, no data (except phone numbers). So I guess my relationship to the networks is more quiet.
As for Google, when I use its search features it is with encrypted dot. My home town always appeared on its pages because of my IP and I really don’t mind.
But I understand your point, Pants, and should I shift to wifi that i’d certainly reconsider the relative easiness of my approach which remains efficient but minimalist. For now sticking to a sticky wifi device is not at all scheduled. Not interested.
“Encrypted.google.com is going away
Important: Google will turn off encrypted.google.com on April 30, 2018. When you visit encrypted.google.com, you’ll be directed to http://www.google.com”
ref: https://support.google.com/websearch/answer/7631341?hl=en
Wouldn’t speed be a major issue here?
You can connect to TOR then connect to your chosen VPN, then your VPN provider won’t know who you are and also your connection to TOR is made safer by the vpn. You can pay with bitcoin and use a vpn only email for signup also.
I’m pretty sure it’s the other way around. Info below pasted from the internet ( https://www.wilderssecurity.com/threads/what-happens-if-you-use-a-vpn-in-conjunction-with-tor-plus-a-few-basic-queries.280983/ )
[quote]
Me —> VPN —> Entry node —> Relay Node —> Exit Node —-> Internet
My VPN provider will see me using Tor, but it won’t be able to read my requests through the Tor network or the responses I receive. My ISP sees I have a connection to my VPN’s IP address but that’s it.
[/quote]
@Remmington
That’s interesting, thanks. “Please note that it is not TOR over VPN, it’s VPN over TOR.” I’m still not 100% sure how the hell that would work. How the hell can you tunnel to an unknown exit node and the exit node uses your VPN? I’m totally confused how this is even possible. But as I read it, and a few google searches later, it is totally dependent on the VPN provider (see https://www.deepdotweb.com/jolly-rogers-security-guide-for-beginners/combining-tor-with-a-vpn/ ). I get it now. Thanks
[quote]
The order in which you start Tor and a VPN does not really matter. You will always wind up using Tor over VPN unless you are using a VPN that supports connection by the proper SOCKS proxy. Tor over VPN does conceal your Tor usage from your ISP however.
If you want to use a VPN over Tor to hide your IP from the VPN you need to use a VPN like AirVPN which provides the option from user control panel to connect to the VPN by SOCKS proxy.
[/quote]
@Pants,
I definitely would not recommend anyone to signup to AirVPN! I have just experienced first hand how immature that company is. I signed up to it for a month last Monday to test it after experiencing overheating problems with the new x64 Mullvad client.
Initially, it seemed OK, but then Malwarebytes flagged a trojan on one of their servers which I’d tried to connect to. I promptly posted it on their forum expecting some kind of response along the lines that they would investigate. Instead, they simply said that Malwarebytes is “junk software” and I was an idiot for using it and then locked the thread!
I subsequently looked at a few other threads where users were experiencing the same issue and the advice to them was to whitelist the IP thereby ignoring the trojan warning.
In another thread a staff member stated that Malwarebytes was deliberately targetting their company to knock them offline! How ludicrous is that?!!
This is just unbelievable! What they should be doing is to investigate the issue not put users at risk by convincing them to whitelist what could well be an infected server. I subsequently decided to put those points across in their General forum which invites users to “get something off their chest”. What happened next is that they blocked my access to their forum and suspended my account! This meant that the vpnclient was no longer able to connect to their servers. Here’s a screenshot of what I saw when I attempted to connect: http://imgbox.com/yKKFZRNE never mind that I’d paid €7,00 for a month’s connection!
Furthermore, they deleted my post presumably to limit bad publicity, but hardly a way a bona fide company would behave.
In addition, I received an email last night that they were refunding my subscription even though I hadn’t requested one at that juncture on the premise that payment had been refused by my bank even though they’d previously confirmed that it had been received. When I checked my bank account online today I could clearly see that payment had been approved and the sum deducted from my balance.
AirVPN appears to be user-friendly on the surface, but criticize them in any way and they act like Donald Trump and fly off the handle. Do a search of their troubleshooting forum for “Trojan” and you’ll see what I mean. Definitely a VPN to be avoided at all costs!
Also point 2 in rhis link probably explains it better than me : https://airvpn.org/index.php?option=com_kunena&Itemid=55&func=view&catid=3&id=892
The article is about VPN trust. So connect to tor then to the vpn and the vpn provider won’t know your real IP is my point.The way you state is the best way to use tor/vpn but not if you are paranoid of the vpn provider. A useful link for what i mean: https://airvpn.org/index.php?option=com_kunena&func=view&catid=3&id=54&limit=6&limitstart=6&Itemid=142#1745
Just throwing some OpSec into the mix. You should research your VPNs, set them up anonymously (disposable/temp emails – a different one for each VPN, bitcoin payment (assuming your bitcoin account is anonymous as well) and use a different payment provider/method for each VPN (debit card bought with cash from the bank, maybe bribe some hobo to go in and get it for you!! heh), don’t use your own IP when setting these up etc). And then the other usual stuff, like not logging into HTTP sites with any accounts that can identify you (in fact don’t cross contaminate any online IDs/personas – i.e don’t use VPN chaining via VM1 to get your gmail or facebook etc, don’t use the same email accounts in each VM, etc – don’t cross contaminate). There’s way more (books worth), but it really depends on your objective. If it’s to defeat state actors, then you need to do more. If it’s to stop your ISP monetizing you or to thwart copyfraud trolling, then not so much.
You can also use TOR/TAILS (or Linux Mint etc): eg TOR—TAILS(VM)+VPN2—PC—ROUTER+VPN1-TOR Exit Node—
Note: I’m not entirely sure if tails and vpn and tor play nicely together.
I’m not an expert on this, but it from all the OpSec failures (think DPR, Lulzsec etc) it all came down to a single failure, and all *they* have to do is join two dots. For those wondering: The Lulzsec member first identified (sabu?) who then turned evidence/helped was detected when his VPN fell over for a few seconds and he leaked his real IP (and he kept IRC logs). DPR was targeted due to his real online ID and DPR being pretty much exclusive in their posts about Austrian economic theories, and then he was monitored in real time jumping in and out of TOR while DPR’s activities on Silk Road matched. Another case was a bomb hoax at a university, and they traced it to the only campus account that had used TOR. Another example, of cross contamination, is pirate release groups where the members reuse handles they have attached to their real IDs. I myself have tracked people this way. In fact, one way I joined someone’s multiple online accounts together, was to reverse image search their unique avatar – it was enough for me to learn some new handles, multiple accounts and then their real ID. Like I said, all it takes is to join two dots. OpSec is hard, but like I said, I’m not an expert.
It seems like there should be some clever method of setting up network routing so that the VMs are not necessary.
Not in Windows.
In Linux you can use routing tables with multiple tap/tun interfaces. You can also bind specific applications to specific VPNs all from the same install.