Find out if your computer supports TPM
Microsoft announced recently that all new devices that ship with Windows 10 once the operating system's Anniversary Update comes out need to support the Trusted Platform Module 2.0 (TPM) and have it enabled by default.
While this won't affect existing devices or devices that you build yourself, the majority of devices that OEMs produce, including all client PCs and Windows mobile devices, need to ship with TPM 2.0 enabled.
This makes PM 2.0 a hardware requirement for new devices that ship with the Windows 10 Anniversary Update.
Microsoft made the decision to exempt some devices from that
- Windows Desktop: all desktop PCs need to ship with Trusted Platform Module 2.0 and have it enabled.
- Windows Server: TPM 2.0 is optional unless certain criteria are met.
- Windows Mobile: all Windows Phones and tablets require TPM 2.0.
- Windows IoT: TPM 2.0 remains an optional component.
The main reason why Microsoft enforces TPM 2.0 is that several features of the operating system depend on it.
| Windows 10 Feature | TPM 1.2 | TPM 2.0 | Details |
| UEFI Secure Boot | |||
| Conditional Access | |||
| Enterprise Data Protection | |||
| Windows Defender - Advanced Threat Detection | |||
| Device Guard / Configurable Code Integrity | |||
| Windows Hello | |||
| Credential Guard | Yes | Yes | More secure with TPM 2.0 |
| Measured Boot | Yes | Yes | More secure with TPM 2.0 |
| Device Health Attestation | Yes | Yes | Requires TPM |
| Virtual Smart Card | Yes | Yes | Requires TPM |
| Passport: Domain AADJ Join | Yes | Yes | Supports both versions, but requires TPM with HMAC and EK certificate for key attestation support. |
| Passport: MSA / Local Account | Yes | Yes | Requires TPM 2.0 for HMAC and EK certificate for key attestation support |
| BitLocker | Yes | Yes | TPM 1.2 or later required or a removable USB memory device such as a flash drive |
| Device Encryption | Yes | For Modern Standby devices, all require TPM 2.0 |
Several of the features are for business / Enterprise devices only.
Find out if TPM is supported on Windows
Current devices won't be able to make use of some of the security features listed above if they don't support TPM.
To find out if TPM 1.2 or 2.0 is available and enabled on your Windows device (desktop), do the following:
- Use Windows-R to open the run box.
- Type tpm.msc and hit enter.
- Confirm the UAC prompt that appears.
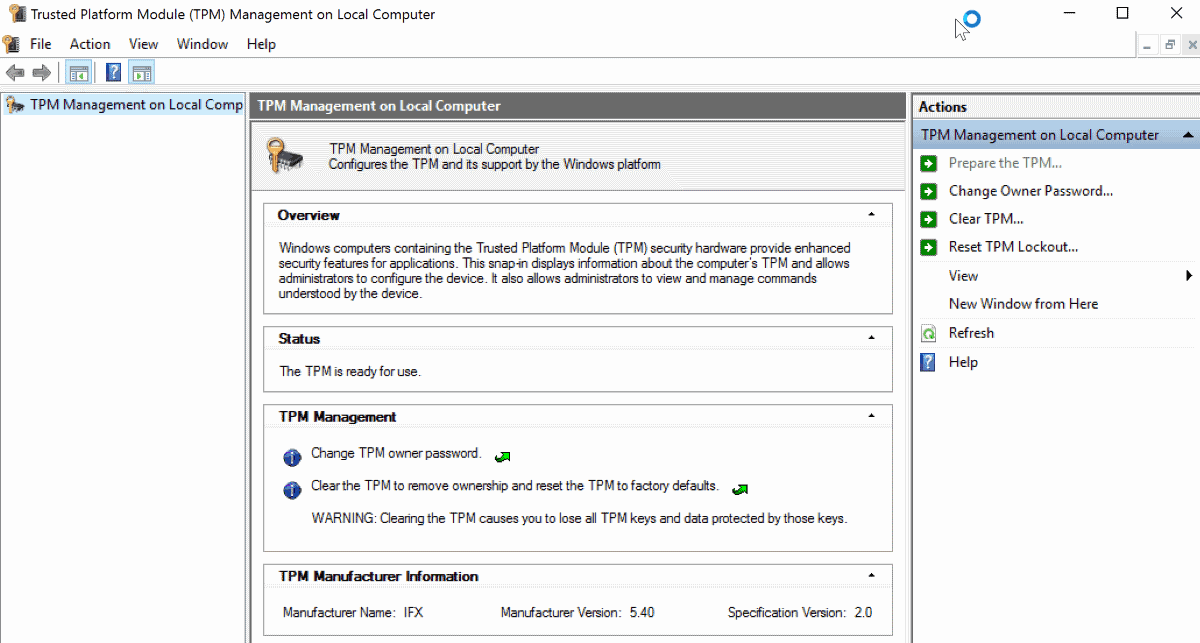
This opens the Trusted Platform Module (TPM) management on the local computer.
If TPM is supported, you may get options to turn on the TPM Security Hardware, create the TPM owner password, clear the TPM, block or allow TPM commands, or turn off TPM by selecting the option in the actions pane. Please note that you need to enter the owner password to do so.
Information about TPM is also available in the Device Manager but only if the feature is enabled and supported on the device.
You find information there under Security devices.
If TPM is not supported, you get the message compatible TPM cannot be found.
This does not necessarily mean that TPM is not supported on the device as its state is controlled by the BIOS/UEFI.
If you get that message, you need to boot your computer and load the BIOS/UEFI management screen to find out about that.
Where you find that depends largely on the BIOS or UEFI of the computer. If you run a recent Surface device for instance, you find reference to TPM under Security. There you can enable or disable TPM.





















I’m not sure I understand some of the comments regarding TPM.
TPM 2.0 is one of the hardware requirements needed to use Device Encryption on Windows 10 Home right? So an average person buys a new computer without some ‘TPM 2.0’ thingy they’ve never heard of, therefore the storage on that new computer is never going to be encrypted by default because it doesn’t meet the specific hardware requirements required to properly enable Device Encryption in a robust way.
And so people are saying that it’s a bad thing that big bad Microsoft are now requiring TPM 2.0 for OEM certification, because the average consumer is obviously going to be much more safe and secure by having an unencrypted drive that anyone can access, right? Much better having an unencrypted drive than having to worry about some fictional DRM issue that *could* maybe possibly happen to them right?
Anything that goes towards meaning every average Joe who buys a Windows device has Device Encryption on by default is a good thing in my book. Or am I odd for wanting that?
If you want to use bitlocker with Windows 10 Pro, a TPM is not required. You can use a USB key, which being removable may be more secure if you want to take it with you. With TPM all someone needs is your password to get into your encrypted files. With a USB key they need to have the key installed and know your password.
That’s pretty cool until the USB key inevitably breaks.
That’s the main use being marketed at users but device encryption is just one of the many uses that integrating cryptographic keys into hardware can be put to, when you consider the encryption of storage such as that use by Windows 10 is based on nothing more than software it’s easy to see how other software could also make use of the same cryptographic hardware.
No one is saying encryption is a bad thing, far from it, but what makes TPM bad (IMO) is that it integrates the cryptographic system into hardware, hardware that’s inaccessible, hardware that may soon, if big business gets their way, come pre-installed on all new hardware (CPU, Motherboards) sold.
I’ll give you an example of how, in a dystopian future, such a system could be used/abused, i guess most people know that some expensive software comes with a USB dongle, a software protection dongle.
https://en.wikipedia.org/wiki/Software_protection_dongle
Now imagine in this dystopian future that everyone can depend on such a cryptographic mechanism, it’s not much of a stretch to imagine that content provides will make use of such a system to protect their content, to only allow it to be played on the device that provides the correct key.
It’s also not a stretch of the imagination to envisage your boss sending you an email asking you to bend or maybe break the law, presently if such a thing happened you’d have proof, you’d have the email, but imagine for a moment that everyone could depend on there being a cryptographic mechanism built into every device, your boss could now restrict the reading of that email to only your device, not only that but he could also automatically prevent your access to it after a certain amount of time, in effect he, or anyone else could depend on that cryptographic mechanism being present and with it set the rules on how, when, and where you access content.
Happily enough, most comments are on the same side with my opinion on this thing.
Adding the Intel “APPS” to these “FEATURES” let the Big-Corporations, Military-Agencies and Petrol-Advertisements join your trusted Operative System to the bunch of the Botnet. Avoid.
TPM sure hasn’t stopped our customers, with name brand PC’s purchased from retailers, from getting their computers infected. I haven’t seen any benefits to TPM, only hassles where the UEFI setting must be changed to allow booting from a USB attached device, when servicing these machines. Booting to a Linux distro lets us manually clean out virus batch files and planted malware that isn’t always visible from Windows and impossible to clean from Windows when there is no safe mode boot at start up and Windows fails to boot normally. Over half of the PC’s we have recently serviced had issues with Windows 10 not booting, black screens, un-cleanable infections. All have TPM and secure boot. While the concept is sound, I believe that the current implementation of both is smoke and mirrors as it seems to stop little to nothing bad from happening.
TPM is one of the most pernicious things ever conceived, sure it has good intentions but they say the road to hell is paved with those, i don’t want a system in my PC that *could* be perverted in the future to prevent me from playing media files on unauthorized devices, that could be used to prevent me from running unauthorized software or files, that hands control of my device over to a third party.
I think you’re getting TPM and DRM mixed up. TPM holds encryption keys and prevent any kind of malware from altering the system.
I think you don’t know how DRM works, maybe this wiki will enlighten you.
https://en.wikipedia.org/wiki/Trusted_Platform_Module#Other_uses_and_concerns
Fact is when you integrate cryptographic keys into a hardware module that’s controlled by a third-party you’re handing over control of your device to that third-party.
Right. Fortunately motherboard manufacturers often omit the TPM chips from boards they make for system builders. Build your own desktop is the answer. For laptops things aren’t so easy.
Does anyone have good links to pages that detail why TPM is bad?
@Max
Yes, but then there’s this: http://www.zdnet.com/article/german-government-refutes-windows-backdoor-claims/
Look @ the Intel services that are currently running on your OS. They allow Intel and 3rd parties to lurk, report and modify the OS, data and programs.
Well here’s one link for starters: http://www.liveleak.com/view?i=e44_1377252731
I agree that building your own PC (or having it built for you) – and obviously avoiding Windows 10 – is the way to go.
Exactly. It gives power to companies like Microsoft which can abuse it under the pretext of “security” to do a number of things users don’t want – lock them out DRM style from anything. Everyone knows how very trustworthy Microsoft is.