Manage cipher suites in Firefox
Web browsers like Firefox ship with sets of cipher suites that the browser uses to protect data that is transferred between the web browser and secure websites.
When a browser connects to a secure website negotiations take place in which the client provides the server with a list of supported cipher suites, and information about the preferred cipher suite and SSL/TLS protocol version.
The server may then accept the client's preferences if supported, or ignore them to deliver a cipher suite of its own which it prioritizes.
In the end, client and server either agree on the use of a cipher suite or the connection attempt fails.
Managing cipher suites in Firefox
Browsers like Firefox support several cipher suites to ensure compatibility with secure servers and sites on the Internet.
While that is a good thing, it may sometimes mean that insecure or vulnerable cipher suites are being used or are still supported.
A recent example is the RC4 Cipher which many browsers have deprecated recently because it is not secure anymore. While many companies who produce browsers have reacted to this threat, you could have blocked RC4 manually before those changes took affect.
You can check SSL on sites like How's My SSL or QUALY's SSL Labs which highlight what the browser supports, and whether anything is problematic from a security point of view.
Using about:config

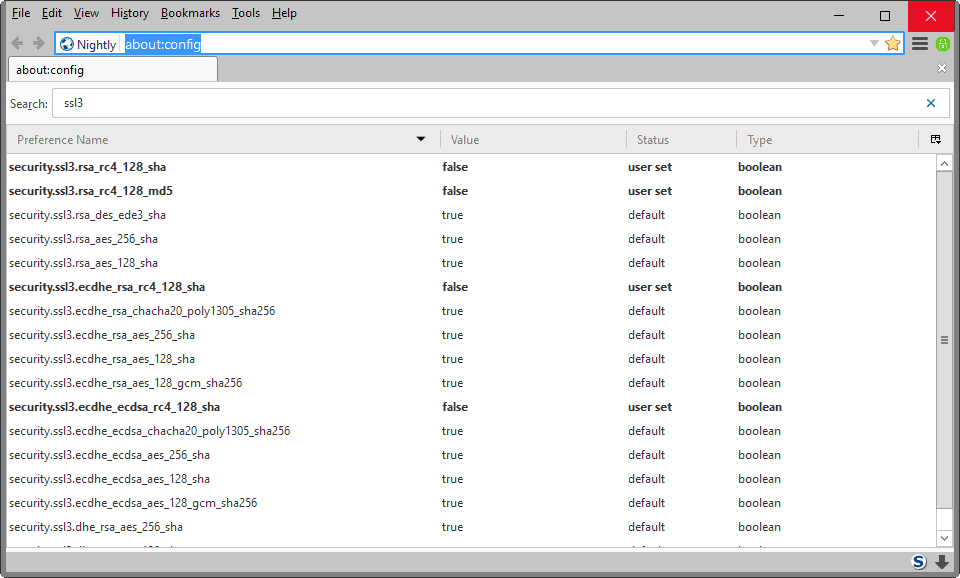
Firefox users can control the cipher suites in the browser on about:config.
- Type about:config in the browser's address bar and hit enter.
- You may receive a prompt that warns you about the dangers of using this in the browser if this is your first time opening the page. Click continue to proceed.
- Search for ssl3 using the search field at the top.
Firefox lists all cipher suites as a result, and you may enable or disable any of those by toggling the value with a double-click on the preference name.
A value of true means the cipher suite is enabled, one of false that it is not available.
Firefox Add-ons
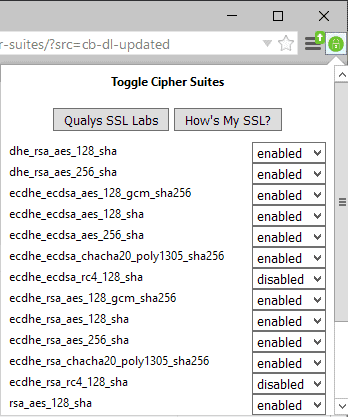
Toggle Cipher Suites is a new browser extension for the Firefox web browser that enables you to manage cipher suites in the browser.
Basically, what it does is provide you with an interface to enable or disable individual cipher suites so that you don't need to open about:config to do so.
The extension adds an icon to the main toolbar of Firefox, and a click on it reveals all supported cipher suites and their state.
You can click on the menu next to any cipher suite to toggle it, for instance from enabled to disabled.
The add-on links furthermore to the two SSL tests linked above so that you can run a check of the new configuration right after you make modifications.
Closing Words
Webmasters may use the add-on or the manual method to disable certain cipher suites to test web servers, and users to block cipher suites that are no longer secure.






















FWIW, SSleuth appears to offer a similar facility. Load this URL for easiest access:
chrome://ssleuth/content/preferences.xul
then see the “Cipher suites” tab.
Reference my earlier comment on ‘security.ssl3.rsa_aes_256_sha’ see section on “Perfect forward secrecy” here https://gist.github.com/haasn/69e19fc2fe0e25f3cff5
Quote from that page not from me:
If you (additionally) want to force the usage of PFS, the only enabled ciphers should be of the ecdhe/dhe variants. Might break lots of stuff.
security.ssl3.rsa_aes_256_sha=false
To prevent man in the middle (MITM) attacks does anybody have an opinion on setting these configurations in ‘about:config’?:
security.ssl.require_safe_negotiation = true
security.ssl.treat_unsafe_negotiation_as_broken= true
See:
https://www.mulle-kybernetik.com/weblog/2013/why_do_i_get_ssl_error_unsafe.html
Very helpful, Alan Robertson. I have been looking for this type of advice for a while.
Incidentally, I read somewhere ( but I can’t find the link to that advice at the moment) that “security.ssl3.rsa_aes_256_sha” had been broken and it is recommended to disable that also.
Hi Freddy – no problem. Yes, that’s a fly in the ointment but some sites won’t connect with https otherwise. It’s a bit of a compromise but you should be immune to Logjam, Freak and Poodle (where do they get these names from?)
You could try switching it off and see how you get on – if the TLS connection fails then just re-enable it. You don’t need to restart Firefox.
Yes, let’s all blindly trust random comments on the internet. That will lead to the best outcome.
Use these and disable the rest (about:config in Firefox):
security.ssl3.ecdhe_ecdsa_aes_128_gcm_sha256
security.ssl3.ecdhe_ecdsa_aes_256_sha
security.ssl3.ecdhe_rsa_aes_128_gcm_sha256
security.ssl3.ecdhe_rsa_aes_256_sha
security.ssl3.rsa_aes_256_sha
You can test them at SSL Labs:
https://www.ssllabs.com/ssltest/viewMyClient.html
and at Fortify:
https://www.fortify.net/sslcheck.html
The idea of such an add-on seems pertinent. In my case I have to rely on what I learn here and there when it comes to ciphers (and not only them!) and set accordingly advised parameters in about:config : I have no idea as to when and why I should enable or disable a cipher in a given situation, which is I guess the purpose of this add-on.
This is the stuff that makes Firefox cool
Way to late for such addons, since FF removed all insecure ones + it get now more monitored.
Yes, too late. Mozilla’s decision to remove (vs just set false by default) some of the older ciphers has left many corporate deployments clinging to firefox ESR.