KeeWeb: Self-hosted KeePass Web and Desktop client
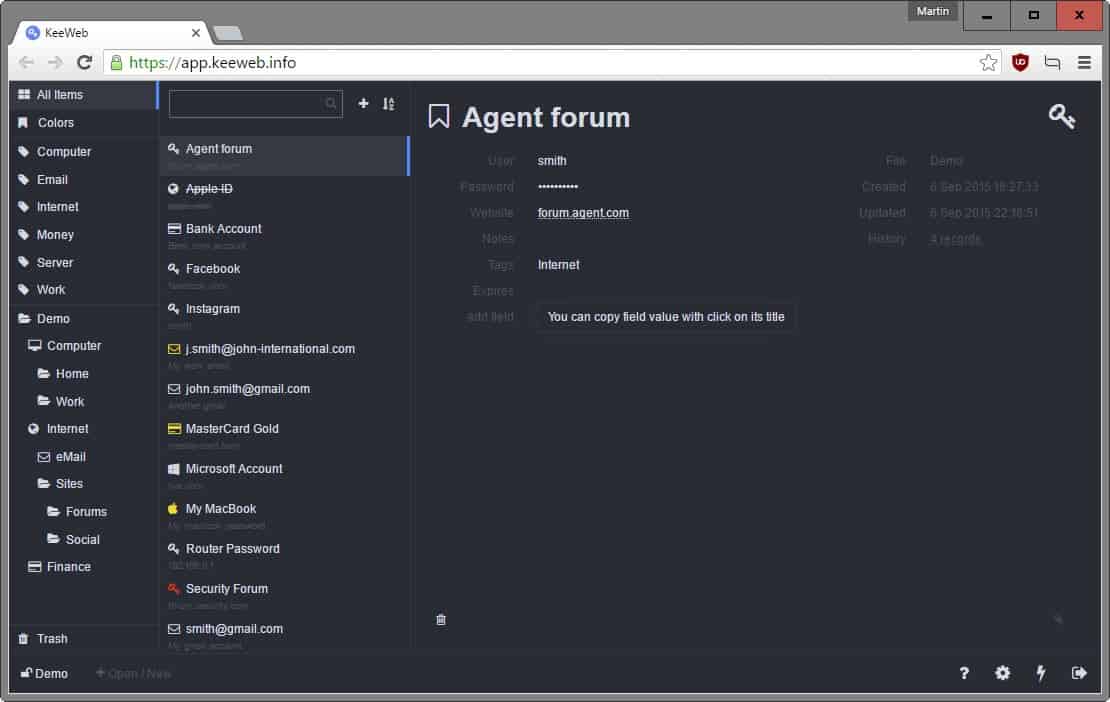
KeeWeb is a brand-new, open source program and web application that supports KeePass databases.
One of the shortcomings of KeePass, at least in the eyes of users who require the functionality, is that there is no web-based version available they can sign in to whenever they cannot run the software.
This makes it difficult to access the password database in situations where KeePass cannot be run, for instance because it is not allowed, not supported or simply not wise to run the program.
KeeWeb tries to address this issue by providing KeePass users with options to create a self-hosted version of KeePass on the Internet.
KeeWeb
Self-hosted usually means that some form of web space is required which in turn makes many users shy away from it due to the technical nature of setting things up.
While webmasters may set up KeeWeb on their own site, all users can set it up as a Dropbox application as well.
The instructions published on the project website are unfortunately not as easy to follow as they should be to self-hosted the application on Dropbox or another server on the Internet.
While it seems easy, as it includes only three steps to do so according to the instructions, you will notice that vital information are missing to get the app set up correctly on Dropbox.
Alternatively, you may use one of the desktop apps that have been released, or access your Dropbox database using the publicly available version of KeeWeb.
The desktop applications are cross-platform which may have some appeal to users of KeePass. I have no need for that, and won't use a service hosted by a third-party to open my KeePass database either.
A self-hosted web version of KeePass on the other hand, that is open source, and easy to set up, should have appeal to users of the application.
KeeWeb is something that I will keep an eye on definitely to see if creating your own self-hosted version of the application improves or is made clearer on the project website so that anyone with a Dropbox account but no knowledge of scripting or programming languages or Dropbox application creation can set it up on their own.
Privacy and Security
The remote version of KeeWeb makes no external requests, uses only locally stored data and makes only one network connection to check for updates which users can disable in the app settings.
Since it is open source, you can audit the code to make sure of that. The author promises that the app contains no statistics or analytics scripts or advertisement.
Now You: Would you use a service like KeeWeb?



















KeeWeb->JavaScript+Electron=heavy bloat=NO!
The good thing about keepass is that you can sync your passwords across devices through some cloud service like dropbox or owncloud without the need to trust the cloud service. You can secure your keepass file with a key-file that you don’t put into the cloud, making it really really hard for someone to brute-force if he gets access to your cloud storage. This means you only need to trust your end devices, not the server. You need to trust your end devices anyway, as they are the place were you decrypt you keepass database.
If you use keeweb, you additionally need to trust:
– the server that keeweb is stored on (an attacker might replace keeweb with some infected version on the server). If keeweb is on dropbox, then you need to trust them.
– the network connection between your system and the server (man-in-the-middle might replace keeweb with an infected version), or properly setup SSL (i.e. you need to trust the CA-system… or use cert-pinning)
– the browser you use (especially, keeweb is made for the use case when you are not at your own pc, so this is the browser of someone else, with a bunch of extensions installed and probably outdated).
– the system you use (for example keyloggers can sniff your master password. This is similar with keepass, but again, keeweb is for the use case where this is not your system! Moreover, keepass for windows offers a “secure desktop” where you enter your master password which cannot be accessed by (off-the-shelf) keyloggers, keeweb doesn’t).
When on the go, better sync your keepass file to your smartphone and use e.g. keepass4android. This means you need to trust your phone. At least then it is your device, not someone else’s, so you have an idea of which crappy software is installed, which updates are missing etc.
I would not use KeyWeb because I already have the KeePass file that I access on the PC synced via BitTorrent Sync to a location on the smartphone that I use from which I can access the file using KeePass4Andorid and the Android version of Firefox, I could also access the file on the desktop that I am currently on if it allows me to install Firefox and the KeePass add-on, then again I could just install a portable version of Firefox along with the add-on onto the smartphone and access it that way or I could store the KeePass file on a usb drive and access that via a portable version of Firefox.
I would rather do the aforementioned methods that to setup a KeeWeb client, however, if the computer that I am on employs any sort of white-listing software protection then that would make much of what I mentioned above undo-able.
I use “Syncthing” to sync/update my KeePass database across my personal devices. It’s open-source, supported on multiple OS platforms, self-hosted on one’s own devices, and data is encrypted while in-transit.
How can this be qualified of “self hosted” since the kdbx database have to be either stored on a dropbox account or uploaded via the browser?
Another solution: https://clipperz.is/
Imho this creates just another kind of security risk. It’s very simple, really. Saving (downloading, uploading) your encrypted passwords data to any non-local location (i.e. any kind of location that is accessible online) still decreases your safety level instead of improving it. Even if this is some shielded web location that you think only you know about.
This whole thing illustrates how we keep wanting the best of both worlds. We do want complete passwords security, but at the same time we also want to be able to access our passwords from any device, anywhere. On a fundamental level, these are two conflicting desires that will never be fully reconcilable.
The unpleasant truth is that we will always have to make a choice between either better passwords accessibility, or better passwords security. This KeeWeb initiative just illustrates this same basic conflict once again, without really solving it.
But it seems to work with passwords right in your browser, without uploading the database. I tried it and yes, I confirm that it works completely offline.
Yes! I have been searching for something like this for a while, because I can’t use dropbox at work to transfer my KeePass DB back and fourth, and using it on my phone at work has been a pain.
Keepass 2 itself can open database files through standard protocols like webdav. You can put your keepass file on some cloud provider that supports webdav (e.g. hubic offers 25GB for free) and then you can open it from there in keepass. No need to install additional software. If you need to use dropbox, you can use the KeeCloud plugin for keepass which makes keepass files stored on a dropbox accessible in keepass without the need to install the dropbox software.
Thanks Chris, not sure why I didn’t see that originally.
Send it to yourself as an email attachment.
Seems like a good idea at first, but the issue of application security becomes paramount:
1. The whole idea of “open source is safe because you can inspect it” is flawed – how many people actually have skills, time and enough knowledge to analyze source code and find potential/actual bugs and malicious code? Exactly – very few in the world.
2. Being online this app is that much more prone to be hacked and considering how all of your passwords are there such a possibility comes with huge risks.
I have hard time trusting KeePassX on my Android and don’t really want to open my DB file there. So, at least for now, I will stick to my usb flash drive and plan ahead for cases when I need my password(s) in environments where it’s hard to run the desktop app. Or, if I really need to – VPN/RDP into one of my machines and then run it there.
Alex
This application is simply a kdbx file viewer. It doesn’t store or serve your actual kdbx files so I don’t see how it could possibly be hacked. Nothing is sent to the sever and the only thing on the server is the logic for viewing the kdbx files not the actual kdbx files themselves.
It could be “hacked” by being replaced with something malicious that uploads your secret data to some other server. Your browser won’t complain or warn you as long as no SSL check fails. Let’s say you “self-host” keeweb on your 5$ webspace without SSL. Then a man-in-the-middle could replace it. Even if you have checked the keeweb code that you uploaded, you would need to check every time again when you run it, because it is transferred over a connection that is not secure.
If you use SSL with pinned certs and all, an attacker could have brute-forced your ftp-password and replace keeweb with something malicious.
Let’s say you use the web-app hosted by keeweb. In 5 years, the keeweb developers lose interest and don’t continue the service. Someone else buys the domain keeweb.info and puts a malicious version on app.keeweb.info that transfers all the secrets to the server. Your browser will not complain.
You would need to check the keeweb code every time you use it..
Christopher K says
[ Let’s say you “self-host” keeweb on your 5$ webspace without SSL. Then a man-in-the-middle could replace it. ]
It goes without saying that self-hosting anything, ESPECIALLY something like this, without SSL, is a very bad idea, especially since a lot of hosts (myself included) offer Let’s Encrypt SSL certs at no charge.
It is very easy to craft an ssl certificate (and redirect http to https).
I don’t know why you could think of an ssl connection for http but not for ftp (see ftps).
Also, you could easily replace ftp with something more secure like scp or sftp (passwordless authentication).
Once you installed your keeweb instance, you don’t need to keep polling from the main source.
I literally can’t understand why you are demonizing web applications.
It is more exposed? yes.
It is less secure? It depends on how you protect it.
If you use fair passwords (ftp, keeweb, basic autentication on the web server/reverse proxy, etc.) it will be very difficult for anyone to bruteforce it.
Plus, you could always rely on tools like netfilter (see iptables and/or nftables), fail2ban, etc.
Furthermore, a lot of reverse proxy could mitigate some attacks like bruteforce/dictionary and sometimes even dos (not ddos).
Alex,
You may benefit of some perspective on these ideas you express.
For #1, the idea is not always that YOU or I could inspect the work, it is that ANYONE can inspect or audit the work. This means people that may be expert coders or basic enthusiasts with an interest. Anyone. Contrast that with the challenges of software that NOBODY but the developer can inspect or audit the security of an app. In this scenario Open Source affords more to the software-using general public (if we want it).
For #2, this CAN be secure if you chose to make it so. Being online does make it more insecure, but no solutions are 100% secure, yet most modern solutions can be made reasonably secure.
For the uber-paranoid, there is always an air-gapped laptop live-booting something like Tails – https://tails.boum.org/
I believe the open source argument only holds if oneself build the code and use the resulting binary, any other scenario seems rather risky.
I like the idea but I am too paranoid to use it.
Alex, I agree up to a point. I think that open source is still better than closed source when it comes to that. At least, you can theoretically go through the source to be sure that it is not phoning home or whatever.
As far as 2 is concerned, I guess you will have to be careful not to leak the url of the page, and if you self-host, you can also add more protection to it as you see fit.
Anyway, I think it is a neat idea, but not something that I plan on using. Still, I can see others liking it.
Martin,
I believe that false sense of security is dangerous. On the point of “someone can inspect it”. This is a fair statement, however you always need to take a probability of that happening into account. In case of a large project with high exposure this is more likely to happen than with a niche, small product like this app. And even large, world-wide used products are prone to either malicious intent or wrongdoing (think all the fun stuff NSA has done with no-one realizing).
Next time I’ll try to explain myself better, I guess :)