How to protect your Android device against Stagefright attacks
Stagefright is a media playback engine on Android that supports several media formats by default, features audio and video playback, session management, DRM and more.
It is also a name of a vulnerability, or a series of vulnerabilities that were recently discovered. Since Stagefright is a core Android technology, it is affecting (nearly) all devices running the operating system.
What makes the vulnerability particularly troublesome is that it can be executed passively. This means that devices can be attacked successfully without user input.
Basically, what it does is send a specially prepared MMS (Multimedia Message Service) to devices. Since Android devices are configured by default to download and process these messages automatically, attacks are executed in the background.
The vulnerabilities allow attackers to run code remotely on the device, for instance by executing code, using device sensors or snooping around.
Only devices running Android 2.2 or older are not affected by Stagefright at this point in time.
Since attacks require that MMS are automatically downloaded to the system, disabling that ability seems to be one of the better options to protect a device from attacks.
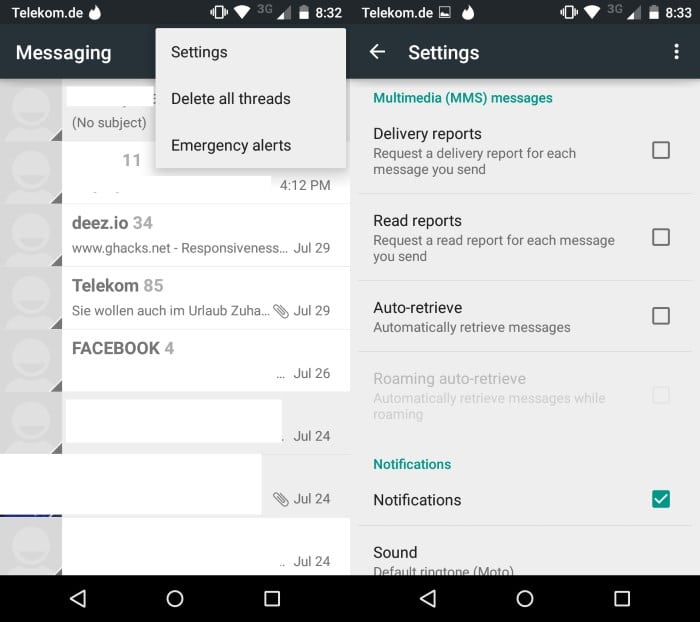
- Open the Messenger application you are using. I'm using the default Messenger app on a Moto G running Android 5.0.1.
- Open the preferences with a tap on the three dots in the upper right corner and selecting settings from the context menu.
- Scroll down until you find the Multimedia (MMS) messages section.
- Uncheck "auto retrieve".
If you are using a different messaging application, you will need to find out whether it supports the blocking of MMS messages by default as well.
Most should provide you with such an option but some may not. If your texting application does not support the disabling of the feature, you may want to consider switching it to a different one for the time being until the issue is resolved.
This is done in the Android settings under More > Default SMS app. Again, the location of the setting may vary depending on your version of the operating system
Most manufacturers are slow when it comes to delivering patches to end users and it may take a while before the vulnerability is patched on most devices. If you run CyanogenMod, you should receive updates this week as the issue has already been patched.





















Jeff – lol….
Tnx for your concern but we will not get an iPhone lolollol
Folks, get an iPhone. It’s time:
As security researcher Nicholas Weaver put it in a (now deleted) tweet, â€Imagine if Windows patches had to pass through Dell and your ISP before they came to you? And neither cared? That is called Android.â€
http://motherboard.vice.com/read/goodbye-android
That is very stressful right now for Android users. Security maybe is the most common problem into the android operating system. We shoud not download applications and games from unknown sources or unofficial sites.
This doesn’t quite get rid of the problem entirely. Only adds an additional step, if a hacker was dead seriously about taking over one’s phone, disabling MMS would be the least of his troubles.
That’s the same thing as saying “If a virus maker was serious about infecting your computer, an antivirus program would be the least of their concern”.
Of course there are other ways to infect/take over a phone, but none as easily/effective as sending an infected picture/video that would run as soon as you received the message.
The main problem is, this is a vulnerability that is built-in to the phone itself that allows code to be executed and gain access. Google has already made a patch for it, but it’s up to the cell phone providers to issue it, which is rarely done.
What i’m saying is that if the vulnerability lies in the stagefright engine that handles media files then an intruder could easily chosse to send the infected files via email, whatsapp and other messaging services. This hack is many times worse than whatever malware that’s on Windows
Great,
[to make sure]
Okay now that i’ve disabled it – does it [& if so: how] affect my ability to receive MMS and such?
Or if I do get one- it’ll simply ask me to tap in order to open it?
[Annnnd, it does not affect regular SMS nor any other messaging platform that isn’t built in & not used for SMS (such as Viber\whatsapp, etc) , correct?!?]
Thanks Martin :)
@Joel,
It’ll ask you to tap to open, then download the file and then you can play it. This is very helpful when it comes from a source you don’t know.
Whatapp and Snapchat type apps don’t fully download it until you swipe it or press and hold.
Thanks again,
Yea, I never installed FB messenger [though I do use Groups app] because of the bad reputation and exaggerated permissions it demands!
I do consider Tinfoil, but not yet making “the step”…
Cheers =]
@Joel,
The exploit is set around the MMS system in the phone and then allows code to be executed by Stagefright (the playback engine in Android) that can give access to virtually anything stored on the phone.
Whatapps, Snapchat don’t interact with the MMS system so they are protected. My first response was based upon a few websites’ details on it but researching it further shows that anything that doesn’t use the MMS system is protected from it (at least, currently).
In short, SMS or other messaging program that doesn’t use the MMS feature are safe. I’d be weary of Facebook Messenger tho, since it does interact with system.
Ok,
Hmmm… Is there any need to limit automatic downloads of pics or previews from other messaging apps [such as whatsapp, viber, etc] or this risk has nothing to do with those, and only refers to System[!!] SMS & MMS default apps…?
Thank you :)
Thanks for this useful information !!