Detect DLL Hijacks on Windows
DLL hijacking is an attack that makes applications load malicious dynamic link libraries instead of the intended -- clean and legit -- library on a Windows system.
Programs that don't specify paths to libraries are vulnerable to DLL hijacking as Windows uses a priority based search order in this case to load libraries.
If attackers manage to place malicious libraries in a location with a high priority, then it will be loaded by the application.
Users cannot really do anything about this as it is not clear if paths are set properly or not in applications that they run on the system. It is up to programmers to make sure paths are set properly in the programs before they are released to the public.
As an end user, you can use a program like Dll Hijack Detect to scan the computer system for potential hijacks.
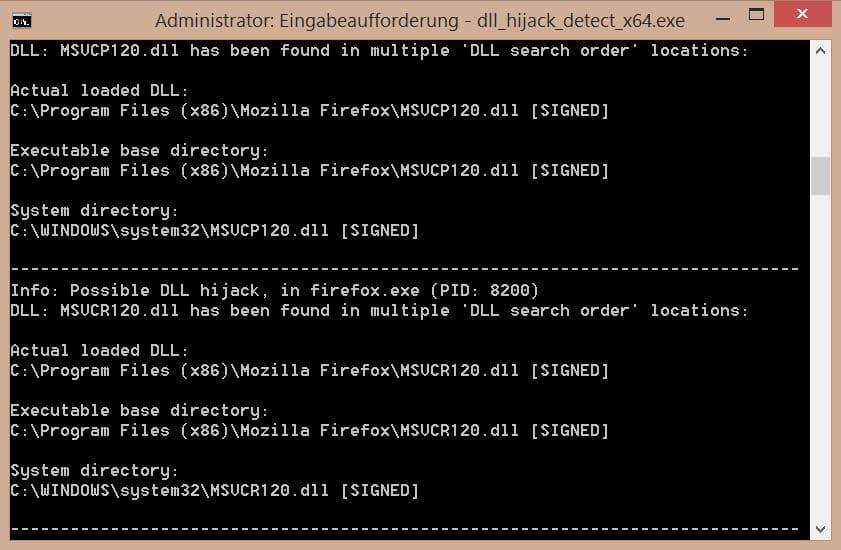
The program identifies all DLLs loaded by running processes on the system. It inspects all library locations where malicious files could be placed and checks in addition if a loaded library appears multiple times in the search order, determines which library is currently loaded and warns you if hijacks are possible.
Not every find indicates that something is wrong. The examples above for example are clean even though libraries have been found in multiple locations on the system.
The program supports a flag to ignore signed DLLs which reduces the output significantly.
DLL Hijack Detect is a command line tool.
- Download the 32-bit or 64-bit version of the program from the linked resource above.
- Extract it to a location on your system.
- Tap on the Windows-key, type cmd.exe, right-click the result and select run as administrator to open an elevated command prompt.
- Navigate to the location that you have placed the program in.
- Run dll_hijack_detect_x64.exe or dll_hijack_detect_x32.exe without parameters to scan the system.
- If you want, add /unsigned to it to only flag DLLs if at least one of them is unsigned.
All that is left to do is go through the report one by one to determine whether DLLs are hijacked on your system.
Tip: Append > c:\output.txt to the command to save the information to the file output.txt on your system. It may be easier to go through a text file than the command line window.
Note: You may need to install the Visual C++ Redistributable Packages for Visual Studio 2013 to run the program.
Additional information about the program are available on the Sans website.
























Well just tried looking for the download link from the main page and can not fine my way back to the release, very poor navigating, sure you can download the Zip file but there’s no exe. Weird website and it becomes annoying very fast. Honestly the place is a mess and it needs better navigation, in my opinion.
Thanks for the Tutorial Martin
Found it, completely unbelievable, the smallest font on the webpage above the pink line, I was like what the hell is going on here, could it be Ad-Block no it’s the small font on the entire website lol, it looked like Tags at first.
I actually rely on the search order to use some older game controllers with newer games.
Smart Screen stopped it from running in Windows 10 build 10041. Anyway around it?
Sorry found it. :)
C++ Redistributable 2013 won’t work in Win 10. I’ll run it in Win 8.1.
Please add a button to delete posts we wish we hadn’t submitted.
It is a WordPress limitation and I cannot do anything about that right now unfortunately.
Ran it twice, with and without the unsigned switch, and got absolutely nothing both times. Is that possible, or does it sound like somethinng was done wrong?
Interesting to see this article today: right after the last Patch Tuesday the HIPS in my Online Armor was going crazy, telling me that every program I opened was “trying to set a global hook.” I don’t know much at all about all this, but I think that that could be one sign of a DLL attack. If so, couldn’t a HIPS or behavior blocker such as the one built into Online Armor recognize and prevent such things? Or do DLL hijacks not set global hooks, or not always set global hooks?
Should not Anti-virus do this job?