What you can do if others want to access your computer
Privacy is probably the number one reason why you may not want others to access your computer. It does not really matter if you want to protect your browsing history, financial documents, photos that you have taken or a book you are writing on.
Sometimes, others may want to access your computer, for instance to look something up, do something of importance (that eBay auction is running for just a couple more minutes), or simply show you something.
If you hand over the keyboard or device as is, chance is that part of your browsing history or files on your computer are exposed to that user.
Browsers suggest sites based on the browsing history and bookmarks for example and it can happen that sites are revealed to the other person that you don't want revealed.
If you value your privacy, you may find the following suggestions useful instead:
1. Different account on the computer
Probably the best option of them all is to have a different user profile ready for these cases. This can be a guest profile that you have created in the past that others can use if they need to use your computer. While it means that you have to switch to the profile whenever that happens, it is the only option that blocks full access to your own profile.
If you are using Windows do the following to add a new account:
- Tap in the Windows-key, type user account and select the matching result.
- Select Manage Another Account.
- Click on Create a new account.
- Type an account name, make sure it is set as a standard user and click on create account.
- Select the account after it has been created and select create a password to set a password for it.
2. Different web browser
Most of the time, it is a web browser that others want to use. You have a couple of options in this regard as well and one of the options is to use a different browser that you don't use normally.
If you have a browser available for situations like these, you can easily run it side by side with your main browser and let the guest use that browser for all Internet activities.
You can download a portable browser and use it side by side with the one you use by default. Most browsers, with the exception of Internet Explorer, are available as a portable versions as well. Pale Moon is available as a portable version for example.
3. Use the same browser
If you don't have another browser that others can use, you may still be able to provide them with a browser that cannot access your browsing data.
It is possible to start a private browsing window for example in all modern browsers. The window runs independent from the core browser which means that it does not have access to bookmarks or the browsing history.
Guests benefit from this as well as most data gets deleted automatically on exit.
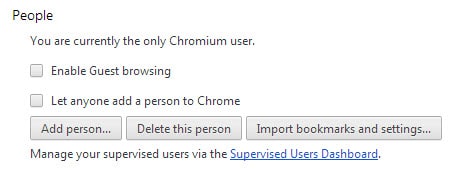
Another possibility is to create a second browser profile for this situation. Chrome and Firefox support the functionality with Chrome even shipping with a guest browsing mode designed for situations like this.
4. Say No
You may not win a popularity contest but you could always say no instead of allowing another user access to your computer.
Now You: How do you handle this?





















Protecting your Computer from Hackers is so much important. Special when you are surf on net on a Public Wifi. One of a great way to do it is to use a VPN software that can give you a complete solution. I have it for my PC and there was no need of installation. You can get it from here http://eshieldvpn.com/
no is completely acceptable and not a 4-letter word.
The “standard account” is for me to use, in everyday activities not requiring an admin account.
For guests, there is the (more restricted than standard) “guest account”.
One of my friends had purchased an extra computer just because he was fed up of sharing his main laptop with others :D.
I would personally not allow my business computer to be handed over to someone else. But if required, I would just enable the guest account on the computer. On my Windows Phone, I have the liberty of having a child mode in which I can control which apps can be used by the users using that account. And opening it is as easy as swiping horizontally instead of vertically.
People have asked to use my cell. I always decline. If they need to make a call I will dial it for them and make sure it connects before giving the phone to them.
Along the same lines, I was wondering if there was software that could run on a router and which which would allow me to allocate guest or permanent logon ID’s? I sometimes have people over that need to connect their computers but I don’t want to allow them into my main system (Windows isn’t a true multi-user system and guests all share the same OS core files).
I know that Comcast and AT&T allow for guest logon’s from their modems/routers but they only allow for ONE global ID for guests. I want two or more ID capability.
Quests get an old laptop which is well-configured
but absent any personal files or information.
No one gets to fly my starship but me.
Another option, though maybe not for the average person, is to use a virtual machine. I have a couple of VMs that I use for testing older IE versions — Microsoft makes these available for free, too — and it’s pretty easy to just spin one of those up and let the person have at it. The nice thing is that no matter what damage they cause, you can just trash it and restore an old copy or even recreate/redownload the VM.
I also have a Linux VM (for work). Having one of those around can earn you some serious nerd cred for that Linux zealot that never carries around a laptop or tablet and wants to borrow your computer, but hates Windows. :)
Next up: How to stop Windows displaying thumbnails for selected videos.
7+ Taskbar Tweaker can stop displaying video thumbnails on the taskbar.
Hi Martin, Someone like that ask you lend him/her recently ? :D
No not recently but it happened in the past and I always disliked that.