SSL 3.0 vulnerability discovered. Find out how to protect yourself
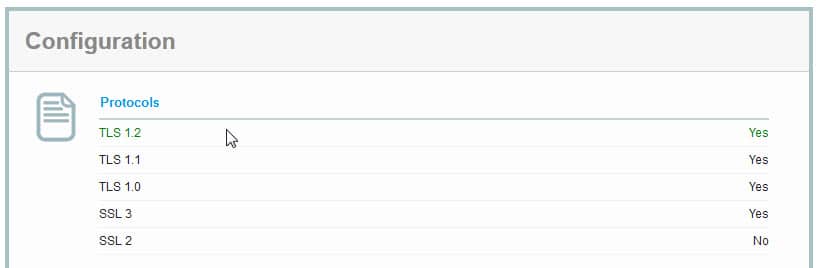
A security vulnerability in SSL 3.0 has been uncovered by Bodo Möller and two other Google employees that attackers can exploit to calculate the plaintext of secure connections.
SSL 3.0 is an old protocol and most Internet servers use the newer TLS 1.0, TLS 1.1 or TLS 1.2 protocols instead. Client and server usually agree to use the latest protocol version during connections during protocol handshake but since TLS is backwards compatible with SSL 3.0, it can happen that SSL 3.0 is being used instead.
During the first handshake attempt the highest supported protocol version is offered but if this handshake fails, earlier protocol versions are offered instead.
An attacker controlling the network between the client and server could interfere with the handshake attempt so that SSL 3.0 is used instead of TLS.
Details about the attack are available in the security advisory "This POODLE Bites: Exploiting The SSL 3.0 Fallback" which you can download with a click on this link.
Protection against the attack
Since SSL 3.0 is being used by the attacker, disabling SSL 3.0 will block the attack completely. There is one problem however: if the server or client support only SSL 3.0 and not TLS, then it is no longer possible to establish a connection.
You can run SSL Tests on domain names to find out which versions of SSL and TLS they support.
To protect your web browser do the following:
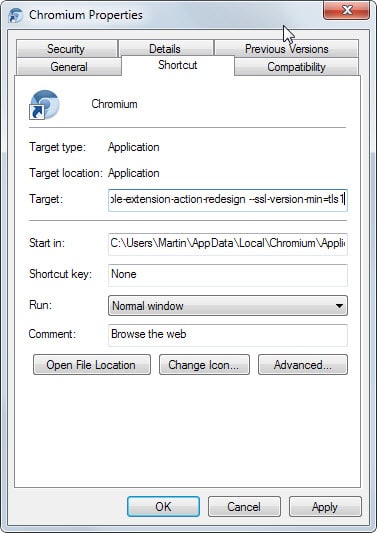
Chrome: Google Chrome and Chromium-based browsers don't list a preference that you can change to edit the minimum and maximum protocol versions that you want the browser to use. You can launch the browser with the parameter --ssl-version-min=tls1 to enforce usage of TLS1 or higher protocols only.
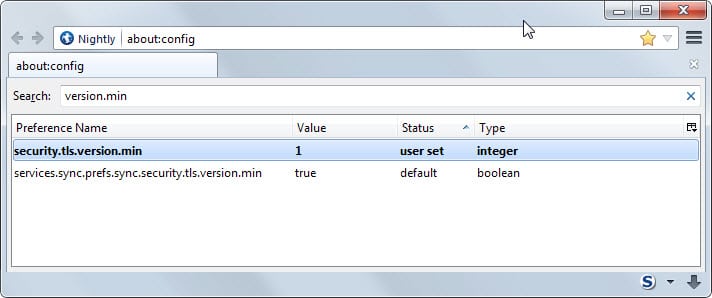
Firefox: Open the about:config page and confirm that you will be careful if this is the first time you open it. Search for security.tls.version.min, double-click it and set its value to 1. This makes TLS 1.0 the minimum required protocol version.
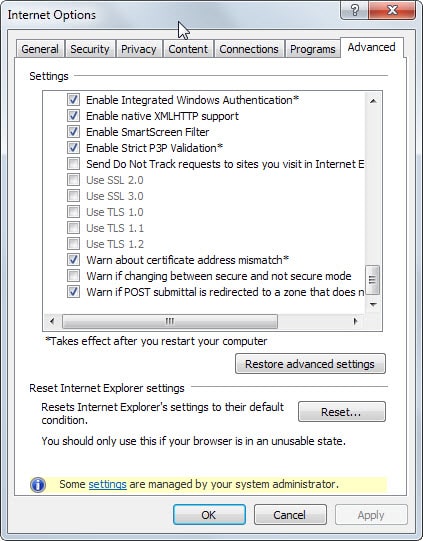
Internet Explorer: Open the Internet Options with a click on the menu button and the selection of Internet Options from the menu. Switch to Advanced there and scroll down until you find Use SSL 2.0 and Use SSL 3.0 listed there (near the bottom). Uncheck the two options and click ok to apply the change.
Mozilla will remove SSL 3.0 in Firefox 34, the next stable version of the web browser that will be released in six weeks. Google plans to remove SSL 3.0 support in Chrome as well in the next months.
Windows: If you want to disable SSL 3.0 in Windows, you can do so in the Windows Registry.
- Tap on Windows-r, type regedit and hit enter.
- Confirm the UAC prompt it if appears.
- Navigate to the key: HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server
- If the path does not exist create it with a right-click on the last key that exists and select New > Key from the context menu.
- Right-click on Server afterwards and select New > Dword (32-bit value).
- Name it Enabled.
- Double-click it afterwards and set it to 0.
- Navigate to the key: HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client
- If the path does not exist create it using the method above.
- Right-click on Client and select New > Dword (32-bit value).
- Name it Enabled.
- Double-click it and change its value to 0.
- Restart the PC.
More information available on this help page.

















There is a revision 2.0 today from Microsoft re SSL 3.0.
https://technet.microsoft.com/library/security/3009008
Thanks
Thanks chesscanoe. That resumes to Client and Server sub-keys to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0 with DWORD Enabled set to 0.
And reboot, once again (I just had to 10′ ago for an application install requirement!)
Be happy.
Want to know if YOU (your browser, rather!) are vulnerable to SSL 3.0 vulnerability? -> https://www.poodletest.com/
Want to know if a given URL is vulnerable to SSL 3.0 vulnerability? -> https://www.poodlescan.com/
ilev’s link above to Microsoft’s security advisory leads to information reminding that protection against this SSL 3.0 (as well as all protections) concerns not only the browsers but the system in itself (see on Microsoft’s page above mentioned what to do on the Registry level) as we sometimes forget that far more applications than the browsers only access the Web from our computer.
On my Windows 7 SP1 x64 is a key called
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders \SCHANNEL\Protocols\SSL 2.0\Client
with the value DisabledByDefault=1
Why is suggested to create a key called ‘SSL 3.0\Server’ but none like ‘SSL 3.0\Client’? Without any knowledge of networks it’d sound logical to me.
I’m having the same situation as Steve. I’ve made the registry tweak, but Chrome is still failing the test at SSL labs. Like Steve said, is this to be expected? Is there another method to test that the machine is, in fact, *not* vulnerable?
Is not the Registry only for Windows? For Chrome, you need to start it with a startup parameter as mentioned in the article.
Actually, if you check the Microsoft instructions again, there are two sections on disabling SSL 3.0: “For Server Software” and “For Client Software”. One uses the Sever key and one uses the Client key. (Perhaps they have updated the article since the above discussion).
What I’m unsure of is whether disabling with this key should be causing browser checks for the vulnerability (https://zmap.io/sslv3/browsers.html) to fail. That site still says I’m vulnerable. Though I’m wondering if the check is based on whether the browser is advertising SSL 3.0, which would then fail if it actually tried to use it because the client is disabled.
@Seban : indeed, and it is what appears to be a semantic confusion for some users as myself which comforted me to mistake on the basis of the Registry’s SSL 2.0 / Client key. If I knew the difference in the implications of a server compared to a client when it comes to a SSL Registry key i’d be fortunate to less mistake :)
If a techie whose dream would have been to teach basics of computing to a few under-graduates, it’s now or never! … thanks :)
@Tom Hawack: That was kind of my question ;)
Why does Microsoft advise disabling SSL 3.0\Server, but not SSL 3.0\Client while there is already SSL 2.0\Client disabled?
My fault, Martin – You are right, together with Microsoft,
Indeed :
5. Right-click on SSL 3.0 and select New > Key and name it Server.
I shall have mistaken with the installed Registry key SSL 2.0 / Client right above.
Good thing for me (only) that I pointed out a (non) mistake.
Thanks for your extra-quick replly.
You are welcome.
Martin,
You wrote (Martin Brinkmann October 23, 2014 at 5:03 pm #)
5. Right-click on SSL 3.0 and select New > Key and name it Server.
Is it not rather Client?
According to Microsoft’s instructions, no. https://technet.microsoft.com/library/security/3009008
Is it also strongly advised to disable SSL 3.0 in Windows? Could someone spell out clearly step-by-step how to do this? Following the steps given in the Microsoft security advisory linked to above did not work. I don’t have “Add Value” on the Edit menu in my registry editor. Thanks
1. Open the Registry Editor with a tap on Windows-r, typing regedit and hitting enter.
2. Confirm UAC if it appears.
3. Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
4. Right-click on protocols and select New > Key and name it SSL 3.0.
5. Right-click on SSL 3.0 and select New > Key and name it Server.
6. Right-click on Server and select New > Dword (32-bit Value).
7. Name it Enabled.
8. Restart Windows. SSL 3.0 should be disabled now.
Because SSL 2.0 is even older than SSL 3.0 and disabled by default I guess everywhere …
I think that creating the SSL 3.0/Client key (if applicable) and setting its Enabled DWORD value to 0 as advised by Microsoft is the right thing to do. This is what I did, and I am far, very far from being a techie :)
… Hope I didn’t goof!
Google is already using tls1.2 (as per their recommendation because of an issue with TLS 1.0 and 1.1,so if you are using Firefox ?the value you want to enter is 3 (for tls1.2)
So for maximum security we should set both the security.tls.version min and max values to “3”? Martin, do you or does anyone else know for sure if this is correct? And I imagine that if this is done, sites using TLS 1.0 or 1.1 but not 1.2 will not work, right?
Setting both to 3 may render some sites unusable. Setting min to 1 and max to 3 is fine. You can experiment with setting both to 3 to see if you run into any site that is not compatible with that.
Microsoft has issued a security advisory 3009008
Vulnerability in SSL 3.0 Could Allow Information Disclosure :
https://technet.microsoft.com/library/security/3009008
Thanks for the link!
Hey, here’s an idea for an article, Martin: Useful Chrome parameters. I bet there’s all sorts of interesting stuff you can do.
I think I did that some time ago. Here is the master list: http://peter.sh/experiments/chromium-command-line-switches/
Ah, indeed you did! Here it is: https://www.ghacks.net/2013/10/06/list-useful-google-chrome-command-line-switches/
Martin: thanks for the article. *security.tls.version.min*, double-click it and set its value to 1
I did the above as per your instructions in Firefox and Pale Moon but forgot the default value. Therefore I ask you that you please let me know what the default value was.
Thank you!
you can sort the column “Status” to find all your “user set” parameters (but it will of course show items from added from extensions), and as Martin says, you can right click and reset (to default) .. personally, the number of tweaks etc over the years, I no longer have any real idea of what I’ve done – just glad I’m using portable versions (of thunderbird, FF, chrome, opera etc etc etc)
You find all modified parameters (or the most important ones at the very least) on about:support.
You can right-click at all times and reset it to the default value (it is 0).
Thank you very much Martin. Normally I write down every change done in about:config but this time I forgot.
How about android, What can i do?
I discovered this new SSL 3 vulnerability this morning… “Oh what a beautiful morning, oh what a beautiful day […]”
Great you pointing this out, Martin.
Here I installed for Firefox a quick tiny add-on (SSL Version Control, https://addons.mozilla.org/en-US/firefox/addon/ssl-version-control/ ) which does the job and has the advantage of having a quick switch in its option board in case a site requires it (a site we are sure of, as it happened to me once this morning).
But I had not considered Internet Explorer, barely used. Thanks to this article IE SSL 3.0 banished as well.
Thanks, Martin
In addition I found this:
Thunderbird (and Seamonkey) have the same key as Firefox (security.tls.version.min), change this to 1 as well.
I don’t know if it is relevant if you don’t use the plugin but Java has options to disable SSL 3.0, too. Open Java Control Panel -> Advanced (I guess, I’m using a German version of Win 7) -> Scroll down and look for SSL 3.0 entry
Good point, thanks for mentioning that!
An alternative to your valid Firefox solution is to install a plugin.
https://blog.mozilla.org/security/2014/10/14/the-poodle-attack-and-the-end-of-ssl-3-0/
Sure that is an option but I don’t think it does anything besides changing the parameter itself.
You are correct. But it’s perfect to recommend to mainstream users. Like my cousin Billy Bob. As well, for the rest of us, it’s easy to temporarily revert if absolutely necessary simply by hitting the Disable button in Add-Ons Extensions. And even easier to walk Billy Bob through when he calls and says he can’t open his online hunting game.