Microsoft Security Bulletins For September 2014
Welcome to the September 2014 Microsoft update overview. It provides you with information about all security and non-security updates that Microsoft has released since August's patch day.
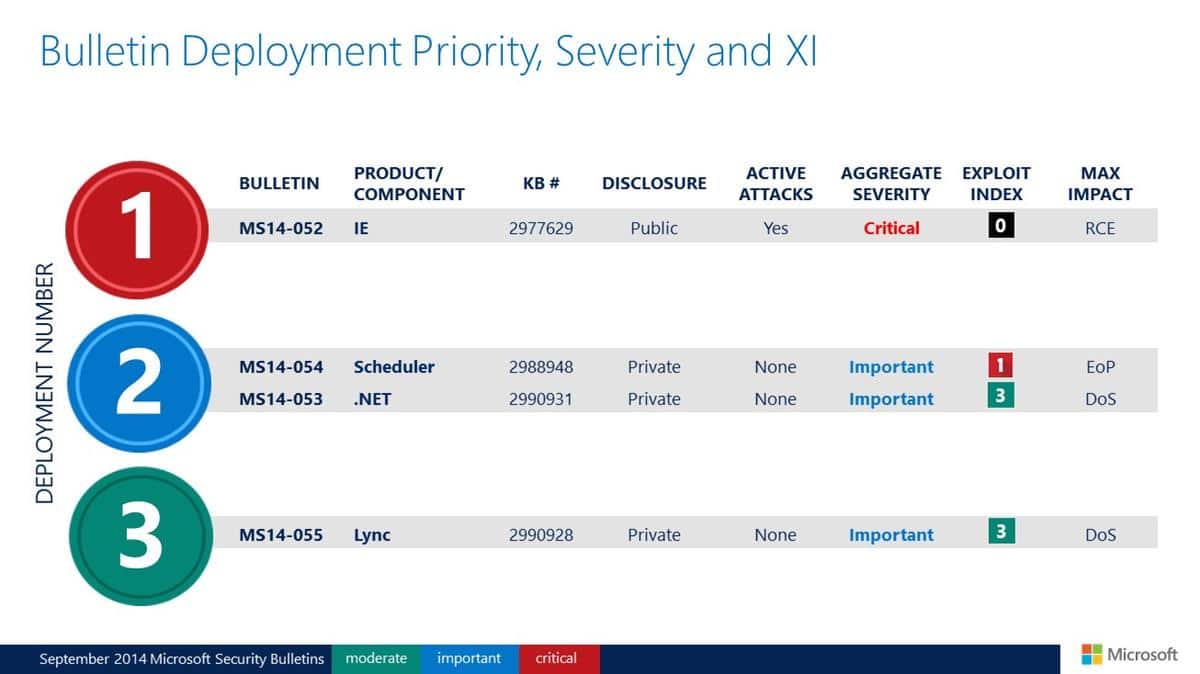
Microsoft released a total of four security bulletins this month fixing a total of 42 vulnerabilities in Microsoft Windows, Microsoft .NET Framework, Internet Explorer and Microsoft Lync Server.
One of the bulletins has the highest security rating critical while the remaining three the second highest rating of important.
You find detailed information about all four bulletins and other patches that Microsoft released this month below.
If you are in a hurry, check out the executive summary and the deployment guide to get started.
Executive Summary
- A total of four security bulletins addressing 42 vulnerabilities have been released this month.
- Affected by vulnerabilities are Microsoft Windows operating systems. Internet Explorer. the .NET Framework and Lync Server.
- One bulletin received the highest severity rating of critical.
- Top deployment this month is MS14-052, a critical bulletin that addresses issues in Internet Explorer.
Video Summary
Operating System Distribution
Client and server operating systems may be affected by security vulnerabilities in different ways. Windows Vista and Windows 7 are only affected by two of the three bulletins affecting the client side of things while all Windows 8 and Windows RT versions are affected by three.
The same is true for server operating systems but with the difference that server systems are not affected in a critical way while all client operating systems are.
- Windows Vista: 1 critical, 1 important
- Windows 7:Â Â 1 critical, 1 important
- Windows 8:Â 1 critical, 2 important
- Windows 8.1: 1 critical, 2 important
- Windows RT: 1 critical, 2 important
- Windows RT 8.1:Â 1 critical, 2 important
- Windows Server 2003: 1 important, 1 moderate
- Windows Server 2008: 1 important, 1 moderate
- Windows Server 2008 R2: 1 important, 1 moderate
- Windows Server 2012: 2 important, 1 moderate
- Windows Server 2012 R2: 2 important, 1 moderate
- Server Core installation: 2 important
Other Microsoft Product Distribution
- Microsoft Lync Server: 1 important
Deployment Guide
- Tier 1: MS14-052 Internet Explorer (critical)
- Tier 2: MS14-054 Task Scheduler and MS14-053 Microsoft .NET Framework (both important)
- Tier 3: MS14-055 Lync Server (important)
Security Bulletins
- MS14-052 - Cumulative Security Update for Internet Explorer (2977629) - Critical - Remote Code Execution
- MS14-053 - Vulnerability in .NET Framework Could Allow Denial of Service (2990931) - Important - Denial of Service
- MS14-054 - Vulnerability in Windows Task Scheduler Could Allow Elevation of Privilege (2988948) - Important - Elevation of Privilege
- MS14-055 - Vulnerabilities in Microsoft Lync Server Could Allow Denial of Service (2990928) - Important - Denial of Service
Security related updates
MS14-045: Security Update for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, Windows Server 2012, Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB2993651)
Security Advisories
Non-security related updates
- Update for Windows 7 and Windows Server 2008 R2 (KB2977728)
- Update for Windows 7 and Windows Server 2008 R2 (KB2978092) - Graphics software or applications crash when they use WARP for software rendering in Windows
- Update for Windows 8 and Windows RT (KB2979501)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2981685)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2984005)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2984006)
- Update for Windows 7 and Windows Server 2008 R2 (KB2985461)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2989540)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2989647)
- Update for Windows Server 2012, Windows 7, Windows Server 2008 R2, and Windows Server 2008 (KB2989956)
- Update for Windows 8.1 (KB2990967)
- Windows Malicious Software Removal Tool - September 2014 (KB890830)
- Update for Windows 7 and Windows Server 2008 R2 (KB2970228) - Update to support the new currency symbol for the Russian ruble in Windows
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2975331) - August 2014 update rollup for Windows RT, Windows 8, and Windows Server 2012
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2975719) - August 2014 update rollup for Windows RT 8.1, Windows 8.1, and Windows Server 2012 R2
- Update for Windows 8 and Windows RT (KB2973544) - An update to enable an automatic update from Windows 8 to Windows 8.1
How to download and install the August 2014 security updates
The security updates are downloaded and installed automatically on most client systems. While that is the case it is still recommended to check for the updates manually as some time may pass before the system itself picks them up.
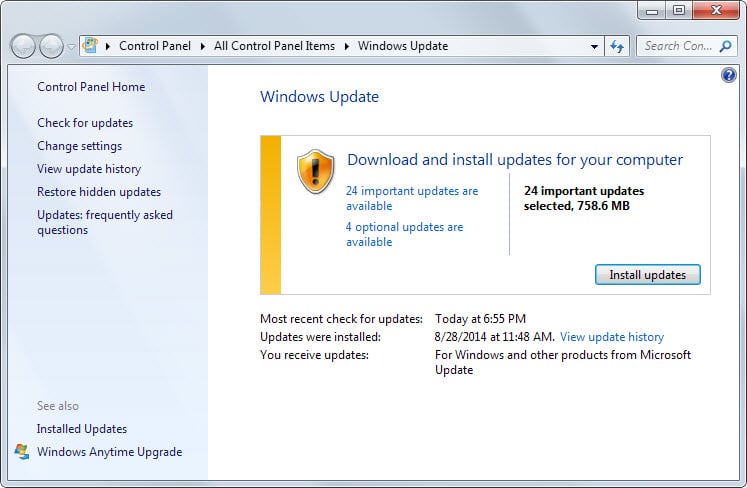
You can do so with a tap on the Windows-key, typing Windows Update and selecting the result of the same name. A click on check for updates on the new page runs a manual check for updates.
The operating system will display all found updates with options to download and install them right away.
All updates are also available for download on Microsoft's Download Center. Here you will also find security ISO images for the month which include all patches so that they don't have to be downloaded individually.
Additional information
- Microsoft Security Response Center blog on the 2014 Bulletin Release
- Microsoft Security Bulletin Summary for September 2014
- List of software updates for Microsoft products 2014
- Our in-depth update guide for Windows





















Yesterday night, when switching off my PC, the Windows September Updates were automatically installed. Installation completed just fine, my PC rebooted and I haven’t performed any operation after that, but just switched it off again. This morning, after switching it on, it asked me to ACTIVATE Windows! I say it again, I haven’t performed any operation after successfully installing the Windows September Updates, so I am afraid the culprit were those updates… Thank goodness, I was able to activate it via the automatic activation telephone system, but I am now very scared that such a thing could even happen! I know that this could be the case if you make any hardware change, but this was not the cause.
Since some times, Windows Updates are one of the most harmful things that can happen to our our systems, and you can easily check this by searching online and on the Microsoft Community forums. I’m seriously thinking to block future Windows updates on my systems. Andy thoughts would be appreciated.
Marco, I understand your frustration and while I cannot agree completely with the idea of blocking Windows updates all-together, I agree that you have cause for concern. The recent trouble created by last months updates are an obvious example.
For Detailed Information, please check out the following articles:
http://www.infoworld.com/t/microsoft-windows/microsoft-ships-replacement-patch-kb-2993651-two-known-bugs-249342?page=0,1
http://windowsitpro.com/security/what-you-should-know-about-kb2993651-installing-it
http://myonlinesecurity.co.uk/microsoft-releases-kb2993651-update-fix-botched-update-ms14-045/
I don’t know if you already have these updates but if so, don’t worry, you can still remove them through the control panel to avoid any future issues at this point.
The updates you’ll want to stay away from are as follows:
KB 2982791
KB 2975719
KB 2975331
KB 2970228
KB 2982791
The following update below was issued by Microsoft to address the issues caused by (KB 2982791), but as the initial article above so candidly points out, even this update has caused problems for users and that even if you haven’t noticed anything yet, doesn’t matter, this update also still puts users at risk.
KB 2993651
I would strongly advise you to not allow Windows Update to install any of these updates. If you have them, then uninstall them through the control panel.
If you’re unsure whether they’ve been installed, simply open the [ Control Panel ] and go to Windows Update.
Then in the search box at the upper right-hand corner type the aforementioned KB updates in this box one at a time. If you have any of them installed, then you definitely should uninstall them by simply right-clicking on them and selecting uninstall.
This is important because of the widely recognized problems with these particular updates but that should not be interpreted to mean that users should just avoid updates from Microsoft from this point forward. Microsoft has acknowledged these botched fixes and says they are working on the problem that caused this.
If you are still concerned (and I would be too), you can simply scrutinize each new update that is issued by Microsoft until you can be sure it isn’t causing any new problems for users and by that, I simply mean allowing Windows update to alert you of new updates but not automatically install them. That way you get to decide when and if you would like these new updates installed. You can adjust the settings for how Windows handles updates from Microsoft by simply going to Control Panel, then Windows Update, then Change Settings.
As a general rule of thumb, security updates are extremely important and should not be avoided for too long, especially if you use the internet, so as I mentioned, look up any new updates that come to your machine on Google by simply typing in the KB number. Whether there is bad or more information about the updates, you will usually find it no problem with a Google search, especially too since Google prioritizes its results. You may not always find info right away if the Update is very new, but wait a few days and then search again. It usually doesn’t take long for word of mouth to travel, especially in the IT community.
If you intend to wait an extended period of time before installing any new updates, I would urge you to beef up your security software settings, at least for the time being but remember, security updates are important, so don’t stave that off for too long.
Hope that helps.
@zeroday1
Thank you VERY much for your detailed reply and extensive information! This is much appreciated, and I’m sure this will prove useful to all the readers of this blog.
What I don’t understand is why Microsoft forces its users to do research unnecessarily! — I mean, yes, the choice should be ours but at the same time, why would Microsoft bother automatically pulsing Windows 8 updates to a Windows 7 machine?! — That makes absolutely no sense and is obviously a big waste of time and resources for both users and Microsoft.
If Microsoft can send special analyzing feeds to its users to figure out if they are using genuine Microsoft software versions, then it should be no problem for Microsoft to sift through the unnecessary updates for its user-base so that, for example, only those with a Windows 8 machine will get updates for Windows 8.
It’s understandable that some updates are required because the issue at hand effects multiple OS versions, however, it’s the unnecessary ones that should not be sent to a users computer if it is not required for his version of Windows.
Like the old saying goes, “If the shoe fits, then of course, wear it,” but don’t waste everyone’s valuable time by sending us these supererogatory updates that may not need to be applied to our version of Windows.
A classic example of this is the fact that Windows automatically sends new versions of the Malicious Software Removal Tool to users machines, regardless of whether or not we need them. Most of us have a security suite and supplemental Anti-malware software already installed on our systems and because most of us are smart enough to know that Microsoft’s security measures are incredibly insufficient, including Windows Defender, there really is no need to keep pestering users with this update. It’s superfluous and an annoyance because it only goes away after hiding it a bunch of times first. Users should have that option instead of just automatically being subjected to it.
Hey, there’s an idea Microsoft——-Why not have Windows Defender & Windows Malicious Software Removal Tool listed as an option that users can choose from within the Windows Update control panel settings (you know, like all those other options listed which can be checked and unchecked per user desire). It would certainly cut down on the unnecessary resources used to disseminate these updates automatically, only for users to then un-check and hide them as an unwanted update. If Microsoft makes it a part of the original OS set up and a permanent option (as mentioned above) to choose from within the control panel settings, then that would just make everyone’s life a whole lot simpler if you ask me.
I should think that Microsoft would have learned something from this latest update fiasco they just caused by pulsing updates that were egregiously flawed and which caused so many headaches and system errors for so many users—way to go Microsoft!
This latest debacle should impress upon Microsoft the need to listen more intently and with greater openness with its customer base and pay more attention to what really matters to us.
We pay through the nose for this software——-and in my opinion, it isn’t getting any better but instead seems to breed the same old antics time and again from a company that seems more interested in profiting from customers than it does in making real and lasting improvements to the platforms they create.
There’s a saying: “You get what you pay for,” but when it comes to Microsoft Software, it seems to me that what you really get is a whole lot of headaches & heartaches for a whole lot of you own money & time wasted trying to deal with these preventable inadequacies perpetrated by this monstrosity we call Microsoft.
Out of 12 updates for my Windows 7 64bit, 7 have crashed. running them 1 by 1 I was left with 3 crashed updates including IE10 update.
758 MB? Is it possible to clean some space from older updates or we are continuously losing space on our hard drives by updates? I wonder how big is my OS by now 1 TB?
The latest try at fixing MS14-045, namely KB2993651, actually came out a couple of weeks ago. It has been the subject of much conflicting discussion, which is worth reading up on. The fix was issued with two known errors in it. See “Update FAQ” in https://technet.microsoft.com/library/security/MS14-045. Also see “Known issues of this security update” in http://support.microsoft.com/kb/2993651. A general web search for KB2993651 turns up plenty of reason to wait before installing this one at least.