How to prevent WebRTC spying in Chrome
New technologies are more often than not a double-edged sword. While they add or improve functionality on the one hand, they may also introduce undesirable features.
This is for instance the case when it comes to WebRTC. It brings real-time communication capabilities to web browsers via JavaScript apis. Think Skype but without plugins or third-party software installation.
While that is great for Internet users who use new services making use of WebRTC, others are left with privacy issues because of it.
Mozilla has integrated WebRTC in Firefox 22 and Google in Chrome 23. While Firefox users can toggle a preference to disable WebRTC in the browser, Chrome users cannot disable it natively.
It is interesting to note at this point that Chrome Android users can disable WebRTC, while desktop users cannot. To do so, the following link needs to be loaded and set to enable: chrome://flags/#disable-webrtc (Update: no longer possible).
WebRTC can be used to spy on users

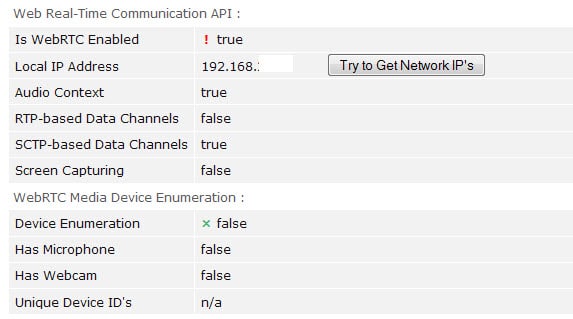
Privacy advocates have two issues in regards to WebRTC. The first is that it is possible to detect the local IP address of the device used to load the WebRTC service, the second that device fingerprinting may be used in some browsers, Chromium-based for example, to fingerprint the system.
Fingerprinting refers to creating unique identifiers for devices so that they can be recognized even if some variables change (like the browser version or IP address).
How to protect yourself in Chrome
There are several solutions to the privacy issue. The most straightforward option is to install the Chrome extension WebRTC Block WebRTC Leak Prevent which blocks the WebRTC feature in Chromium-based browsers.
This option is only viable for users who don't use WebRTC. While it may be possible to turn the extension on or off based on your communication needs, it is not something that is really comfortable to do.
In regards to fingerprinting, previous versions of Chrome had an option to disable device enumeration on the chrome://flags page. This feature has been removed from Chrome recently and is no longer available.
Chrome provides websites with media device hashes and there is little that you can do about it as there are no options anymore to disable this from happening.
One way to deal with it is to clear "cookies and other site and plug-in data" regularly in the browser. Doing so will generate a new hash so that spying sites cannot identify you anymore based on that.
Besides that, starting Chrome in Incognito Mode will also render the fingerprint useless for that session.
How to test
In case you are wondering, here are links to scripts that reveal information about your system when WebRTC is enabled.
- WebRTC IPs - Displays local and public IP addresses if WebRTC is enabled.
- Browserleaks - Detects if WebRTC is enabled, your local IP address, and other related information.
- Detection on JSFiddle - Uses WebRTC to look up and display the local IP address.
- JSFiddle script with with live host probing
- What Is My Browser - Displays fingerprinting information such as the local and remote IP address, browser, plugins, location, screen resolution and more.
These test websites should work in all modern web browsers. Success depends on the implementation of WebRTC mostly though.
Now Read: Protect Chrome against fingerprinting with Chameleon




















I guess chrome hasn’t any manual setup to disable WebRTC so you need to follow some extensions for disabling webRTC, if you have a VPN extension or an ad blocker they can do the same.
For firefox, you can diable webRTC manually bby following below steps;
1) Type about:config in the address bar of Firefox.
2) Click on “I’ll be careful, I promise!†(or some security message similar to that) [the message depends on the version of Firefox you have]. For instance, the new version of Firefox displays a warning message, “This might void your warranty!†followed by an explanation of advance settings security and such. If you see such a message, click “I accept the risk!â€
3) A list will open with a search bar above. In that search bar, please type: media.peerconnection.enabled and hit enter.
4) When the result comes up, double-click on it to turn its value to false.
5) Close the tab to finish the procedure.
Ref: https://goo.gl/kF11sL
Follow report @ https://code.google.com/p/chromium/issues/detail?id=457492
I suggest you can use Hide ALL IP http://www.hideallip.com to block WebRTC in Chrome, Hide ALL IP support auto block WebRTC in Firefox/Chrome/Opera etc, I already test it, it really works.
the extension for chrome doesn’t work. There is nothing chrome users do about this for now: https://code.google.com/p/chromium/issues/detail?id=457492
You guys can try Chromium-based Slimjet browser from http://www.slimjet.com which provides a built-in option to disable webrtc.
Thanks for the informative and timely article.
Mathieu, I see no FUD here, and on the contrary, I test Chrome desktop on the above sites and it seems as the article claims: Chrome divulges device information including absence of devices.
Apparently, this can be blocked with an extension: https://chrome.google.com/webstore/detail/webrtc-block/nphkkbaidamjmhfanlpblblcadhfbkdm
“a few bits for uniquely identifying someone” can be very significant bits – and this site doesn’t even use WebRTC:
https://panopticlick.eff.org
The chrome extension works partially. What other options do i have?
The information presented here is borderline spreading FUD.
Devices cannot be accessed at all unless the user explicitly approves it for that website. That includes the ability of the website to enumerate devices or get the device name. Thanks to this, random websites won’t be able to fingerprint the user based on devices. If the user consents to give device access to a website, there is a few worse things the website can do, including taking a picture of the user, record its voice or ambient noise, etc. Talk about fingerprinting capability then ;)
Also, technically, device access (getUserMedia) is not part of WebRTC spec but part of the Media spec.
The only information that could be used for fingerprinting is the local IP address. Yes it probably adds a few bits for uniquely identifying someone, but really we’re just talking about differentiating different users behind the same public IP.
Also this is really a problem with an expiration date linked to IPv4. Once we’re all transitioned to IPv6, there won’t be a notion of private IPv4 addresses anymore.
Of all the test links provided, none were accurate, or were only partially accurate. As for the last link (What is my browser), if the info it found is what my browser is broadcasting, then go right ahead because after it detected java script was on, everything below that was dead wrong.
You can block WebRTC IP leak by installing this Chrome extention,
https://chrome.google.com/webstore/detail/whats-my-ip-whournet/lohmchjkjjlpghmhjemcjdgbaghpgacm
and check the result before and after installing it on http://www.whour.net/
There are more ways than one to garner information. “What is my browser” doesn’t look very robust or detailed
Try >>
http://ip-check.info/?lang=en << JonDonym
https://panopticlick.eff.org/
http://browserspy.dk/
I actually allow javascript on these pages so I can see the results