Firefox 25 gets OCSP Stapling which improves privacy
The Online Certificate Status Protocol (OSCP) is being used by Firefox to retrieve certificate information. This happens when you connect to a https website in the browser. What it does basically is ask a Certificate Authority (CA) whether the certificate of the server is genuine or if there are any problems associated with it.
Certificates can be revoked for example, for instance when a private key has been lost, the domain was transferred to a new owner, or if there has been a hiccup when it was issued.
Firefox currently handles this by doing the following:
- Connects to a https website and receives the certificate of that site.
- Communicates with the CA to find out whether the certificate is valid.
- Connects to the site if it is, or not if it is not.
This works considerably well but has two distinct disadvantages. First, it is necessary to connect to the CA whenever a certificate needs to be verified. This not only adds another connection to the process, but also leaks to the CA which website you are visiting.
Second, if a connection to a CA cannot be established by the browser, it must either select to terminate the connection because it cannot verify the authenticity of the certificate, or connect to the site anyway even if there is a chance that the certificate has been retracted.
Firefox by default allows the connection to go through in this case. This is not ideal as noted, and you can modify that setting to change it to termination instead.
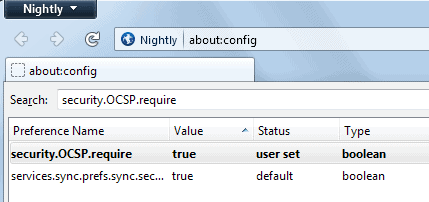
- Type about:config into the browser's address bar and hit enter.
- Search for security.OCSP.require.
- Double-click the entry to set it to true. The default value is false.
OCSP Stapling
The new OCSP Stapling feature that has just landed in Firefox Nightly resolves both issues. It moves the certification verification step to the website. A https server checks with a CA regularly if the certificate is ok, and will receive the information that it is or isn't from it.
When you connect to the site in question, you not only get the certificate in the transfer, but also the signed assertion of the CA. Firefox verifies the data and will connect to the site if everything looks alright, or won't if it does not.
If a site does not support OCSP Stapling, Firefox will fall back to OCSP instead. According to Mozilla, OSCP Stapling has been implemented into web servers such as Apache or nginx. It still needs to be enabled before it becomes available.
Advertisement


















