Microsoft releases Enhanced Mitigation Experience Toolkit (EMET) 4.0 Beta
I have talked about Microsoft's Enhanced Mitigation Experience Toolkit (short EMET) before here on Ghacks and do not want to rehash everything that has already been said about it in the past. So what does it do? Think of it as an extra layer of security that steps in if someone tries to exploit a vulnerability on your operating system that has not been patched yet. EMET is not patching security vulnerabilities, but blocking access to known and unknown exploits that attackers may use to break in to the system.
The last EMET update dates back to 2012Â that was released in form of a technology preview that added four additional Return Orientated Programming (ROP) attack mitigations to the security program.
Microsoft released the first public beta of the upcoming Enhanced Mitigation Experience Toolkit 4.0 two days ago. The program is available for download at Microsoft's Download Center and compatible with all client and server based versions of the Windows operating system that are still supported by Microsoft (so Windows XP SP3 and Windows Server 2003 Service Pack 2 onwards).
So what is new in the new EMET version?
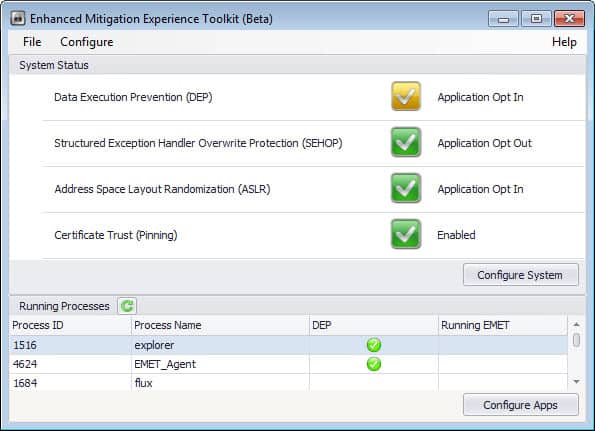
The interface has not changed much on first glance. You find one new option listed under System Status when you open the program interface. Certificate Trust (Pinning) is the new feature that is enabled by default. What it does?
It makes available a set of rules to validate digitally signed certificates while using Internet Explorer. The rules match domains with the Root Certificate Authority, and variations discovered during the check are indicators of a potential man-in-the-middle attack that is carried out. Exceptions can be configured so that certificates may be accepted even if some rules do not match.
EMET 4.0 features additional improvements and feature additions:
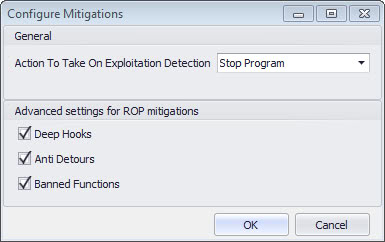
Advanced settings for ROP mitigations block techniques that try to bypass the mitigations. You find those new features under Configure > Applications > Options > Advanced Configuration. Deep Hooks, Anti Detours and Banned Functions are all enabled by default. Here you can also define the action that you want taken when exploits are detected. The default action is to stop the program, and you can change that to audit only instead.
Several compatibility issues that users encountered in previous EMET versions have been resolved. This includes fixes for Internet 8's Managed Add-ons dialog, Internet Explorer 9 and the Snipping Tool, Internet Explorer 10 on Windows 8, Office software through SharePoint and Access 2010 when certain mitigations were enabled. Microsoft furthermore added several opt-in rules for select applications that are known to interact poorly in regards to certain mitigations. The list of support applications includes Google Chrome, Adobe Photoshop, Google Talk or Lync.
EMET 4.0 has reporting capabilities through a new component called EMET Agent which you will find running on the system after installation of the new version. It replaces the EMET Notifier component that shipped with EMET 3. It is set to start automatically with Windows and handles tasks such as writing events to the Windows Event log, show events via tooltips in the notification area of the operating system, perform certificate trust validation tasks, and send reports for the Early Warning Program feature.
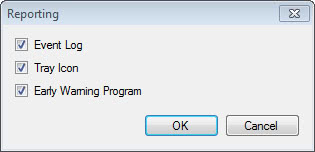
You can configure the Reporting under Configure > Reporting in the application window. Here you can opt out of the Early Warning Program, disable the tray icon and writing to the event log.
Emet 4.0 comes with Group Policy support. EMET.admx and EMET.adml files are automatically installed alongside the program and added to the Deployment/Group Policy Files folder of the installation directory. These files can be copied to the \Windows\PolicyDefinitions and \Windows\PolicyDefinitions\en-US folders. Once done, EMET configurations become available in Group Policy.
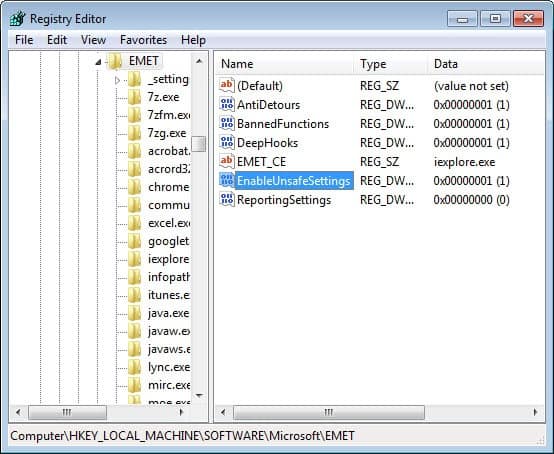
Advanced users can enable so called unsafe settings via the Windows Registry. Do the following to enable it:
- Tap on the Windows-key, type regedit and tap on the Enter-key.
- Accept the UAC prompt if it is displayed.
- Navigate to the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EMET
- Locate the parameter EnableUnsafeSettings
- Double-click on the name and change its value to 1 to enable it.
You need to restart the graphical user interface before the new option becomes available. The only unsafe option that is currently available is to set ASLR to always on. Microsoft notes that setting it to always on may throw a blue screen on some systems during boot. If that is the case, the company recommends booting into Safe Mode and setting the ASLR setting to Opt In or disabled instead.
Other features and changes include:
- Switch to the Microsoft .NET Framework 4.0.
- Protection for processes that do not have .exe extensions.
- New default profiles for migitations and Certificate Trust (you find those under Deployment > Protection Files in the program folder).
- Wildcard support when adding applications to the protected programs list.
You can read the official announcement over at Microsoft's Security Research & Defense blog and consult the user guide that is put into the program folder for additional information.
Advertisement




















Thanks a lot, Martin :)
That seems quite strange, but I’m waiting for the 4.0 stable version :)
Sorry for commenting one more time, but I didn’t understand. Microsoft will release in just a few weeks EMET 4.0 without releasing 3.5 stable? Am I right? Thank you :)
Yes that seems correct.
Hallo Martin, I appreciate it ferry much that you again where so good to make time for your like always clear and swift answer. I could not find a (auto) update feature to.
I forgot to also ask that when the final version comes out do I first have to uninstall the Beta version and than install the final version or can I install the final version over the Beta version?
Could you inform me/us about that when it is convenience to you.
Maybe you could mention the solution with your update post.
Paulus no problem. I will post a new article as soon as the new version comes out.
Thanks Martin, For you earlier explanation and your Cristal clear article.
I have now installed the Net. 4.5 and the EMET program. I only left with have one worry.
Does this program auto update or do I have go regularly to the Microsoft EMET website, from the comment here above I have learned that in one mount there will be a steady update?
I’m not sure Paulus. We will see when the final version comes out. I could not find any update check options in the program, and it is likely that you need to download and install manually. I’ll post an update once the final version comes out.
Fantastic. I didn’t want to install the 3.5 Tech Preview as I was hoping a stable release would be released shortly after. Little did I know it’s take almost a year for that to occur.
According to the blog post, looks like this Beta will only last 4 weeks, so expect a stable release sometime in the next month or so.
I’ve had version 3.5 installed for some time now. This is really a cool tool to use in addition to my virus software. I look forward to updating to the newest version.
Thanks for the heads up Martin. Great tool!
I don’t understand. 3.5 version is still in Tech Preview status and now 4.0 beta is released. Am I missing something? What’s the point in not having a stable release before releasing a new beta?
I’m using it on Windows XP. (even though it doesn’t achieve it’s full power on XP) and it works pretty well. The tray notifier starts way faster than the one in v3, which was the main reason I stayed with v2.0 until now.
@Paulus: EMET is just an additional security layer, that lowers the chance for the exploits to succeed. It is not intended as a replacement for other security measures like antivirus, firewall, HIPS etc.
Martin, Are you personally using EMIT on your Windows 7/8 computer?
And are you convinced that it gives the user just that extra edge that he needs on top of his payed virus program (like ESET endpoint antivirus) and his ferry well guarded browser with add-one’s like no-script, ad-block plus, perspectives, etc. etc. ?
Paulus, it is an additional layer of security that steps in if 0-day exploits and other unpatched vulnerabilities are exploited. I’m running it on all of my versions of Windows.
Wow, this was too technical for me. Should this be handed off to my computer guy for installation. Not sure if I need this.
Steven, think of it as a buffer that comes into play when unknown vulnerabilities (0-day) are used to get in to your system. If you do not run EMET, your only hope of defense is your antivirus software if it uses heuristics. With EMET, you block common exploit types from being executed on your system thus mitigating some of the attacks that would have otherwise succeeded.
“EMET is not patching security vulnerabilities, but blocking access to known exploits that attackers may use to break in to the system.”…
Known exploits aren’t the problem, 0-day exploits are the biggest problem.
ASLR, DEP and Protected Mode are a joke easily bypassed.
I wanted to say unknown but somehow did not. It will block some known and unknown exploits.