Forensic tool to decrypt TrueCrypt, Bitlocker and PGP containers and disks released
One of the things that you can do to protect your data is to use encryption. You can either encrypt individual files, create a container to move files in to or encrypt a partition or disk. The main benefit of encryption is that a key, usually a password, is needed to access the data. A basic form of encryption is if you password protect a zip file, more advanced encryption can protect the whole system including the operating system partition from unauthorized users.
While it is important to pick a secure password during setup to prevent third parties from successfully guessing or brute forcing the password, it is important to note that there may be other means to gain access to the data.
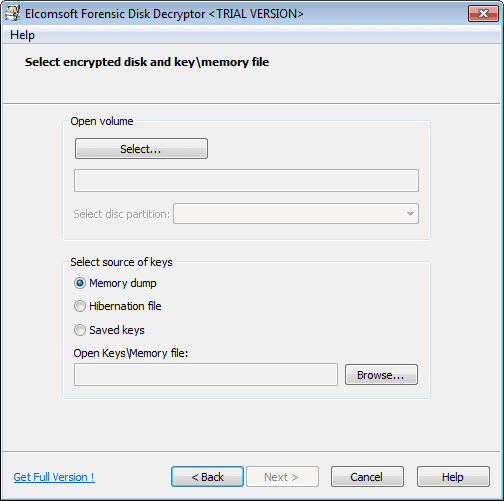
Elcomsoft has just released its Forensic Disk Decryptor tool. The company states that it can decrypt the information stored in PGP, Bitlocker and TrueCrypt disks and containers. It needs to be noted that local access to the system is required for one of the methods used by the program to work. Encryption keys can be acquired by three means:
- By analyzing the hibernation file
- By analyzing a memory dump file
- By performing a FireWire attack
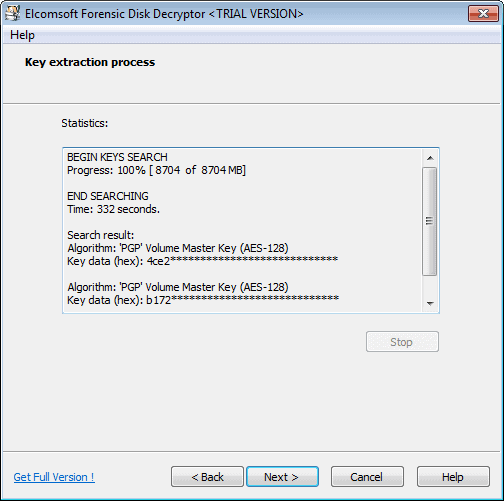
The encryption key can only be extracted from the hibernation file or memory dump if the container or disk has been mounted by the user. If you got the memory dump file or hibernation file, you can start the key search easily and at any time. Note that you need to select the right partition or encrypted container in the process.
If you do not have access to a hibernation file, you can create a memory dump easily with the Windows Memory Toolkit. Just download the free community edition and run the following commands:
- Open an elevated command prompt. Do so with a tap on the Windows key, typing cmd, right-clicking the result and selecting to run as administrator.
- Navigate to the directory you have extracted the memory dump tool to.
- Run the command win64dd /m 0 /r /f x:\dump\mem.bin
- If your OS is 32-bit, replace win64dd with win32dd. You may also need to change the path at the end. Keep in mind that the file will be as large as the memory installed in the computer.
Run the forensic tool afterwards and select the key extraction option. Point it to the created memory dump file and wait until it has been processed. You should see the keys being displays to you by the program afterwards.
Verdict
Elcomsoft's Forensic Disk Decryptor works well if you can get your hands on a memory dump or hibernation file. All attack forms require local access to the system. It can be a useful tool if you forgot the master key and desperately need access to your data. While it is quite expensive, it costs €299, it may be your best hope of retrieving the key, provided that you are using hibernation or have a memory dump file that you have created while the container or disk were mounted on the system. Before you make a purchase, run the trial version to see if it can detect the keys.
You can disable the creation of an hibernation file to protect your system from this kind of attack. While you still need to make sure that no one can create a memory dump file or attack the system using a Firewire attack, it ensures that no one can extract the information when the PC is not booted.



















Is it possible to figure out a encryption / decryption key if you have only 6 datapoints (inputs / outputs)?
Device ID (input) / (key)
Device ID Lease Code
MI110800017 0703-95be-73cb-416f-3155-14a8-e976-5750
MI110500013 8b97-1d6f-94cf-51f1-dd0c-7a0e-d7e2-b1d3
MI110600013 5956-4c11-f56c-1a53-f0be-3a92-9da8-72eb
MI110100001 acc2-8d17-16f9-20b0-4983-2bfb-fb37-f16e
MI110200002 1392-0efb-e0f3-8b8a-4b6c-71d1-394f-97e0
MI1120800026 5331-070c-453d-9156-7cae-143d-595b-8c23
MI110800012 ?
“I was hoping that F(MI110800017) = 0703-95be-73cb-416f-3155-14a8-e976-5750
and we can figure out how F, algorithm function worked. “
Seems to me the smart thing is to have TrueCrypt set to dismount at hibernation and not cache passwords. Which is exactly what I do. This is a non-story for me…
If your going to be doing something illegal, DO NOT use a physical system. use one of many Virtual Server/Workstation products (VMware/VirtualBox/KVM/MSVPC) create your OS of choice on it.
1. Full Disk Encryption on the VM
2. Configure the system the way you need it
3. Run the VM on an encrypted drive from the Host OS (Unless your using (XenServer or ESXi)
4. Write a script to delete the VM from its current location and rewrite blank hash files with the same name as the VM to the same location overwriting the signature cache on the disk (Execute via manual or remote app or device)
5. Set your VM to reset to zero state on power off (UNDOABLE state)
6. Make your VM host name work with LOCALHOST.
7. On your Host system have a DoD grade disk kill ready, via remote app by smart phone or enabling Bluetooth device to trigger a kill.
8. Never ever do illegal crap from your house a friends house or anyone you know, there are 100s of free WiFi’s out there.
You might even want to setup a one time password encryption.
For USA people plead the 5th and get amnesia about the pass phrase.
Now for the paranoid:
Wire up a light switch (Switch can be in different room) to a outlet in the same room as your PC that has a device connected to it, in some cases USB device. When your OS detect this device it will trigger a script or program that will destroy alter make your PC bark what ever you want it to do. This is a physical tripwire. You can also simply connect the device to a CLAPPER clap on clap off…
There are 1000s of ways to set your rig up in a spy craft fashion .
I encrypt in order to be sure nobody will extract data when I trash my harddrives or if they fail.
Academic here in the UK, where you can simply be required to hand over passwords. Refusing may be a serious criminal offence in itself, irrespective of the contents of the files. If you genuinely don’t know or can’t remember you can be in a catch-22 situation. In the eyes of much of the police and judiciary, the very act of encryption is deviant and suspicious.
In effect guilty unless and until you can prove innocence. But then as we’ve already lost double jeopardy, and the rights to silence and arrest without charge…
This is nothing new,
This was discussed many times in online security forums including Truecrypt forum,
If an attacker gains access to your machine while the volume is mounted/open, you’re done,
A tool which is able to crack/open offline container is yet to come (and I think that is not going to happen, unless somebody finds a vulnerability in the encryption algorithm itself)
Anyway thanks for the information Martin
is there any free tool?
OK, so it seems like this tool only works if the volume is mounted. My question is: why the heck wouldn’t you just copy the unecrypted files from the mounted volume. Why even care about the password if, by design, you can only use this tool when you call just access the files?
@Miles
“Why even care about the password”
I would imagine so law enforcement are able to re-access the data again if required. I’m not sure how the legal system works, but it would make sense for them to not only have a duplicate of the files for forensic analysis, but to also have access to the original data if need be, if for no other reason than to prove the evidence hasn’t been altered/tampered with.
Also, as Martin said, if a volume was previously mounted and the computer hibernated, the un-encrypted keys in the RAM would have been copied from RAM and written to the hard drive, thus being potentially recoverable.
Actually, it is about FORENSICS! You won’t need to recover files from an already mounted device, but a forensic investigator who needs to preserve the evidence for a case will need that. Of course, it can have other uses, but I suspect that this is it’s main purpose.
It also works on hibernation files. Sometimes, you may be able to create a memory dump and transfer it but not actively access the system.
If i get it correctly the hibernation file and the memory dump files are only good if the truecrypt container or partition are a) already mounded or b)have been previously mounted and the keys are cached, but seems irrelevant otherwise.
Not having access to the system a DMA attack could eventually find an external TC container header, but i have serious doubts hidden TC containers could be ever traced.
If the volume is the actual OS partition ,doesn’t it means that it was necessarily mounted?
Thelma that is correct. The memory dump only works if at the time of the dump the volume is mounted.
This is why I said that this is not an encryption cracking tool, but a forensic tool.
Expensive but OTOH if a coworker suddenly leaves and forgets to mention the password it may be a good tool to have and well worth the money.
Extracting passphrases and keys from memory, hibernation files, and so on is nothing new. This is just another tool that does it.
Also, for the people that are worried: the encryption used by PGP, TrueCrypt, etc. is as strong as it was before; this is not an encryption cracking tool.
What about this…?
http://en.wikipedia.org/wiki/TrueCrypt#Operation_Satyagraha
Operation Satyagraha
In July 2008, several TrueCrypt-secured hard drives were seized from a Brazilian banker Daniel Dantas, who was suspected of financial crimes. The Brazilian National Institute of Criminology (INC) tried unsuccessfully for five months to obtain access to his files on the TrueCrypt-protected disks. They enlisted the help of the FBI, who used dictionary attacks against Dantas’ disks for over 12 months, but were still unable to decrypt them. The case presented a noteworthy real-world test which proved the strength of TrueCrypt.
If you only got a fully encrypted hard drive, you can’t do anything else but to run a brute force attack to try and recover the key.
We are a long way from 2008 :-)
There no encryption system immune to hacks anymore.
Diego is correct.
Truecrypt or rather AES, Serpent and other algorithms are uncrackable.
What the news is talking here about is not cracking the code, but extracting the code from active memory in “live” system powered up and when a user has accessed Truecrypt and typed in a password.
So to be able to actually grab the code of an encrypted system, FBI would have to knock down your door, brake into your house and be lucky enough to find your computer turned on. End even in this case, they would have to be lucky once again to find you working with TrueCrypt on your PC that particular day, so that the password container would be loaded in RAM.
Lots of variables here….
And majority of computer enthusiast have hybernation disabled anyway. (powercfg -h off)
It creates useless I/O operations and PC-s are more and more equipped with SSD-s which “requires” hibernation to be turned off.
What I am trying to say is that TrueCrypt still remains safe. That particular programs does not offer cracking capabilities, but solely offering a plausible way to extract forgotten password. The encrypting algorithm itself used in TrueCrypt remains bullet-proof!
It is still possible to try and brute force True Crypt but that obviously only works if the password is not that secure. Disabling hibernation is definitely a way to protect the password from being extracted if the computer is not on.