Java 7 Update 10 introduces new security features
Are you still using Java on your computer? Some of you may need it to run programs such as JDownloader or RSSOwl (there is Java Portable for that which does not integrate itself into web browsers), others because an Internet site they visit frequently makes use of it - heard that a lot of banks still use Java for their Internet banking offers. The chance is high on the other hand that the majority of users who read the article do not really need Java but have it still installed on their system.
Chance is also relatively high that the Java version on some systems is outdated and therefore vulnerable to Internet-based and local attacks targeting those security issues.
Oracle's latest Java 7 Update 10 brings along new security features that can make a Java installation more secure on the computer system.
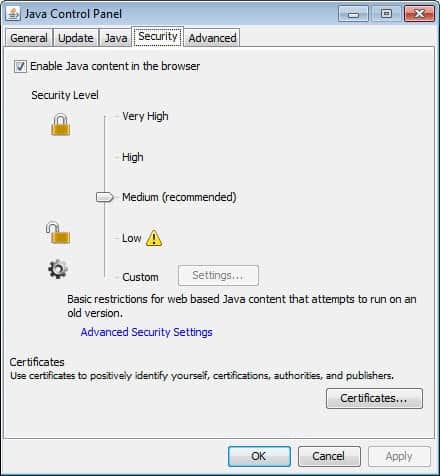
When you open the Java Control Panel on Windows, for instance by clicking on the start button, then Control Panel, selecting View by small icons on the top right and then Java, you will notice quite a few changes in the control panel applet. One of the first is the option to disable Java content in web browsers. Just uncheck "Enable Java content in the web browser" under Security and Java won't be integrated into browsers anymore. That's great if you only need Java for local applications but not for web apps.
Doing so will render all web-based attacks targeting Java useless on the system where you have made that chance.
Here you also find the new security level listing. The default level is set to medium which allows signed applications to run even if Java is not up to date, and unsigned apps only if Java is up to date on the system. Here is an overview of all security levels available:
- Very High - High restrictions for all web based Java content.
- High - High restrictions for web based Java content that attempts to run on an old version.
- Medium (recommended) - Basic restrictions for web based Jave content that attempts to run on an old version.
- Low - All web based content runs with only limited restrictions
There is also a custom level that gives you more options in regards to how Java apps are handed on the system:
- Action for untrusted apps on a secure JRE version: run without prompt, prompt user, don't run
- Action for untrusted apps on an expired or insecure JRE version: Run without prompt (not recommended), single-click confirmation prompt, multi-click confirmation prompt, don't run.
- Action for local applets: Run without prompt, Prompt user, don't run.
Two additional checkboxes are made available under the Advanced tab:
- Show sandbox warning banner - disables the warning icon on windows opened from unsigned apps
- Allow user to accept JNLP security requests - Allow unsigned apps via JNLP to ask the user for additional access to computer resources such as the printer or hard drive.
Java 7 Update 10 introduces furthermore new warning dialogs when the JRE is insecure and needs to be updated.
Please note that you can also modify the security levels and web Java access from the command line on Microsoft Windows:
- WEB_JAVA=1Â enables Java in the browser
- WEB_JAVA=0Â disables Java in the browser
- WEB_JAVA_SECURITY_LEVEL=VHÂ sets the security level to very high
- WEB_JAVA_SECURITY_LEVEL=HÂ sets the security level to high
- WEB_JAVA_SECURITY_LEVEL=MÂ sets the security level to medium
- WEB_JAVA_SECURITY_LEVEL=LÂ sets the security level to low
The option to disable Java from being used in web browsers is an excellent addition that should help users who only need Java support locally and not on the Internet. The security levels too improve the overall security on systems where Java is installed, especially if they are customized or set to high or very high. It may take some testing to find out the best security level for your system though.
Advertisement
















this is a nice move by Oracle to make Java more secure. High time to upgrade my java.
Thanks for the post Martin.
@David
Thank you !
If you’re missing the new Control Panel in XP SP3, here is the binary:
%PROGRAMFILES%\Java\jre7\bin\javacpl.exe
I don’t have Java console in Control Panel anymore with this update (on XP sp3).
Others have the same thing?
Same thing for me on XP sp3 pro.
This particular version of JRE 7 is the first version certified with our Oracle EBusiness Suite application. We will be migrating from JRE 6 to JRE 7 in the near future.
I foresee headaches and stress with this setting. Java on the desktop when you have multiple separate independent organisations using your app is a nightmare. :-/
Sorry Java fans…
Very nice. Java is following Adobe’s footsteps. Finally they are realizing that people are steering away from Java due to safety reasons. Though it is not Java’s or Flash’s fault. It is a wide-spread usage of the 2 programs that make them popular to black-hat’s exploits.
There are less talked-about programs that are highly vulnerable to exploits as well. Powerpoint for instance is one of them, especially when slideshows are viewed inside the browser like in Gmail, Hotmail or Yahoo mail services. All PDF-s viewed inside internet browser is potentially highly dangerous as well, especially in Adobe’s reader. Foxit Reader is not immune to such attacks too, so it is better to view PDF-s inside the pdf viewer itself.
No matter what the programs is, it will eventually became dangerous to use once it is popular enough. IE is example. Firefox is following its path here. Chromium is a bright exception here due to its sandbox and the fact that it has probably the smartest developers behind. Also, Google prevents exploits of it’s browser smartly by organizing Hacking contest every year. It is relatively cheap to cash those 10k$ to one individual who discovers vulnerability, rather than leave all those black-hats outside working in the wild and selling exploits on the Internet to anyone. 5 stars to Google here, though I am not using Chromium at all.
I believe that I have seen articles about the cooperation between Mozilla and Adobe to sandbox the PDF-viewer inside Firefox.
Yes, Chrome uses a sandbox, but there were already several cases that hackers (e.g. Pinkie Pie) broke out of their sandbox and powned the browser.
I believe it was achieved twice. By the same person if I recall correctly. But compared to other browsers, Chromium’s security is a light year ahead. Being hacked (to prove critical vulnerability) just twice or so makes it extraordinary safe. And that is good news for all those users, who are not technically oriented about PC- security.
For many of us it is all the same whether we use adobe reader, Flash, Java or unpatched IE. You simply open browser and PDF viewer inside Sandboxie or Comodo’s sandbox and security vulnerability of all those unsafe programs becomes irrelevant. It is the majority of PC users like our moms or grandmothers, (who do not know about this stuff) that benefit most from new Java security features, improved Adobe XL etc.
Thanks Martin, am downloading it now. Unfortunately schools, banks and government organizations (all with hiring requirements requiring low IQ levels) still require java.
Well dear, perhaps you dont pay attention. Java is java because apps coded in java are portable. install java virtual machine in your os, and use any java applications (98.5% of them) perfectly fine.
i completely removed java from my system.
java and flash cause Weakness security in your system.
I did the same thing after migrating to apps that do not use Java.