Crystal Anti-Exploit Protection new security software released
The new security software Crystal Anti-Exploit Protection has just been released in a first beta version. The program adds another layer of defense to the system that protects applications that it protects from a number of exploits that they may be vulnerable for.
Update: Please note that the program and the developer website are no longer available. We suggest you use programs that offer a comparable feature set such as Malwarebytes Anti-Exploit or the built-in Windows Defender on Windows 10. End
It is not a replacement for antivirus software, other security software or common sense, but can protect the system from exploits that target vulnerabilities that have not been fixed yet.
Crystal Anti-Exploit Protection is available for 32-bit and 64-bit versions of Windows XP, Windows Vista and Windows 7 at the time of writing. It requires the Microsoft .Net Framework 2.0 on the system and administrative privileges.
How does it work?
CrystalAEP operates by running within every instance of a protected program (for example the web browser), performing checks at key points within the program's life-time in an attempt to ensure that it is not under attack. Crystal also alters the behaviour of protected programs to render them more difficult targets for malicious software seeking to be installed on a user's system - if the vulnerable program malware is targeting is in an unknown and constantly changing state many traditional methods for exploiting flaws within the software are made significantly more difficult.
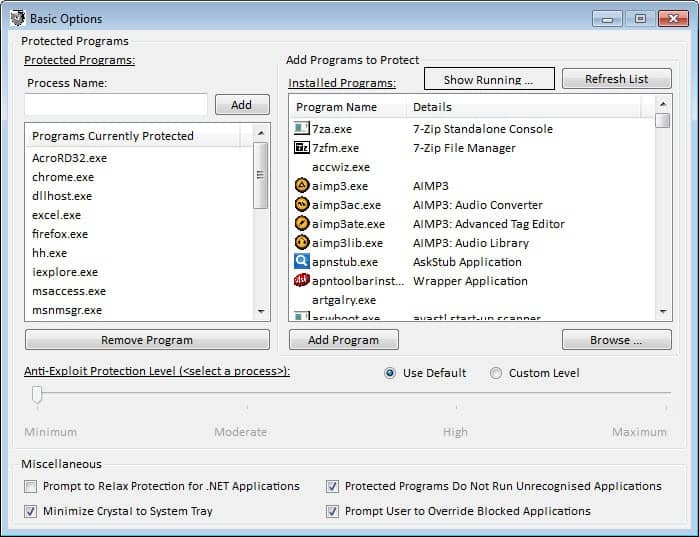
The program protects a number of high profile processes automatically after you have installed it. This includes web browsers such as Internet Explorer, Google Chrome or Firefox, Acrobat Reader, Excel, VLC or Winamp. The protection level is set to minimum, the lowest available level by default to avoid issues when running the programs on the system.
- Minimum – Provides only the basic protection, none of which should be invasive or disrupt delicate programs. This mode provides a backstop against some classes of threat and is surprisingly effective considering the limited features that it enables, but is not recommended for most programs as little is done to disrupt exploit attempts.
- Moderate – A good improvement on Minimum, this mode aims to provide a compromise between reliability and security, erring on the side of reliability. This mode is recommended for applications which do not cope well with the High mode of protection, but is otherwise not recommended.
- High – Provides an equal balance between reliability and security. Most of the particularly effective anti-exploit techniques are enabled when using this mode. This is the recommended mode for most users.
- Maximum – This mode provides the highest level of protection which Crystal affords, enabling nearly all of the protection features the product can offer. Occasionally Maximum protection provides too locked-down an environment for flexible programs to operate under, and is therefore not recommended above High for most users. Maximum can be enabled for systems for which security is absolutely paramount above software reliability.
You can click on Configuration > Basic Options to modify the protection levels, or add running or installed programs to the list of protected applications. It is possible to configure different protection levels for processes, so that high profile applications like Java, Firefox or Internet Explorer run on a higher level than programs like SnagIt or Wordpad.
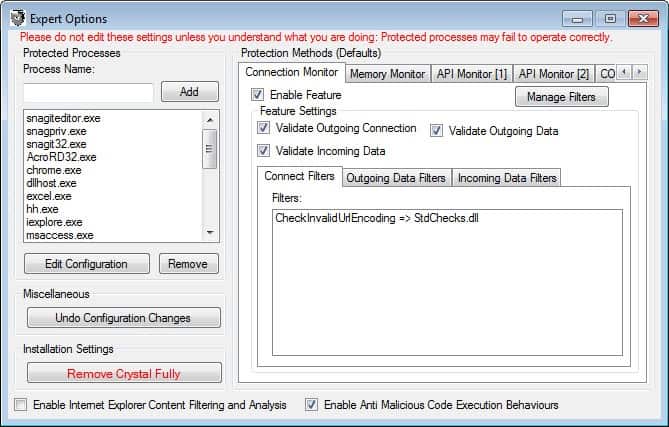
You can alternatively open the Expert Options and configure the protection methods for each process in greater detail. Only users who know what they are doing should bother to make changes to these features as they require a great deal of security know how.
There is also a content filtering option, but it is not selected by default, and only available for Microsoft's Internet Explorer.
The program displays the most recent alerts in the main program window. Here it is also possible to enable realtime alerts and to disable the protection that it provides.
A good start to get to know the program is to read the excellent user manual in pdf format that it ships with. Here you find information about an introduction to the program and its configuration modes. Each expert setting is displayed here, and the explanations should be enough to give you a basic understanding of what they do.
You may run into issues with some programs after installation. The developer recommends that basic users should start with the minimum protection settings first to avoid these issues. He recommends that experienced users set the level to high before switching to the expert options to modify the settings further.
Closing Words
The program is not a run and forget type of program. You will spend some time configuring processes on your system. The developer has added the basic options mode for inexperienced users who want to add some level of extra protection to their system. And while that's working well to a certain degree, the real strength only becomes visible in the program's advanced options and higher protection levels. It is definitely a program to keep an eye on.
Advertisement





















Thank you for this article. This program appears to be interesting and I’ll be testing it sometime soon :)
In the past (some years ago), I used SystemSafety Monitor, but it was left unsupported when XP SP3 was released and no longer works… This one appears to be similar, but it has more protection checks and options for the user to control how each process is protected.
Sounds like yet another version of the “HIPS” tools various antivirus and antispyware programs have been using for years.
The main issue with these things is the constant nagging. Many of them are supposed to “learn” and then stop nagging – but that almost never happens because the programs being watched are frequently updated and break the identification method used by the HIPS. Firefox, for example, gets updated almost every week and every time the HIPS will have to be retrained for it.
I also am not aware of any studies done on how easy it is to bypass these things. Antivirus signatures are painfully simply and can be bypassed by any malware writer in a matter of minutes. HIPS rules, while not based on simple static code sequences, nonetheless can be bypassed once you know them.
It’s similar to Web Application Firewalls which supposedly prevent SQL injection. They check for strings like “and 1=1” – so the hacker changes his code to “and 2=2” – and beats the firewall…
Bottom line: I almost always don’t enable a HIPS feature for my clients because 1) it will drive them crazy, and 2) there’s little evidence that it works…
Could someone compare it with EMET from M$ ? (differences& advantages)
EMET uses techniques to _prevent_ some kind of well known way of attacks and is useful for defending any process, while this software claims that it can _detect_ various (yet unknown) attacks targeting those programs.
Though I agree to Morley this Crystal looks a bit fishy as a quality security software doesn’t use .NET for it’s frontend…
This looks very interesting, Martin.
I will have to keep an eye on this. It sounds like it could have great potential if the developers are committed to this project.
Unfortunately, as soon as you say “requires dotNET 2.0” you lose me. That has yet another layer of vulnerabilities that I am not currently saddled with.
If you have Windows Vista or 7(for sure), dotNET 2.0 is preinstalled as part of operating system. I tried manually uninstall it and had to do system restore.