How to Create a Hidden Encrypted Volume With True Crypt
A judge recently ordered a US citizen to decrypt storage space on a computer so that police forces could analyze protected files on the system. In this particular case, the defendant was ordered to decrypt the hard drive of her Toshiba notebook no later than February 21, or face the consequences "including contempt of court".
The ruling may still get overturned, but at this point in time it is not clear how this will turn out.
Encryption makes sure that only authorized users can enable access to data provided that there is no loophole or backdoor built-into the software itself. People traveling to the US may have their mobile computers analyzed by federal agents even without probable cause.
Users have a number of options at their disposal to protect their data from prying eyes. Encryption for instance requires a pass phrase or key to be entered to decrypt the contents of the storage device. If you forget the password, you cannot open the encrypted contents anymore.
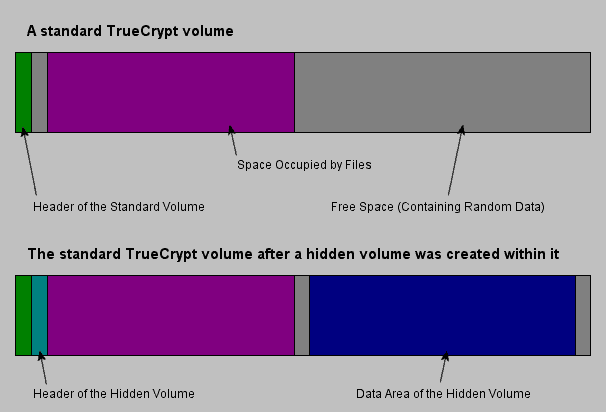
There is however a better option for users who want to make sure that they private files stay personal. True Crypt supports so called hidden volumes. These volumes are encrypted volumes inside an encrypted volume. True Crypt calls the concept plausible deniability. You put your important files into the hidden volume, and other files that you do not mind to share with others in the regular encrypted container. When someone asks you to decrypt your data, you enter the password to decrypt the first volume that you do not mind sharing with anyone.
It may happen that you are forced by somebody to reveal the password to an encrypted volume. There are many situations where you cannot refuse to reveal the password (for example, due to extortion). Using a so-called hidden volume allows you to solve such situations without revealing the password to your volume.
The principle is that a TrueCrypt volume is created within another TrueCrypt volume (within the free space on the volume). Even when the outer volume is mounted, it should be impossible to prove whether there is a hidden volume within it or not*, because free space on any TrueCrypt volume is always filled with random data when the volume is created** and no part of the (dismounted) hidden volume can be distinguished from random data. Note that TrueCrypt does not modify the file system (information about free space, etc.) within the outer volume in any way.
Hidden volumes can be created quite easily in True Crypt. New True Crypt users should read through the tutorial posted on the site first to understand the basics of creating encrypted volumes on the computer.
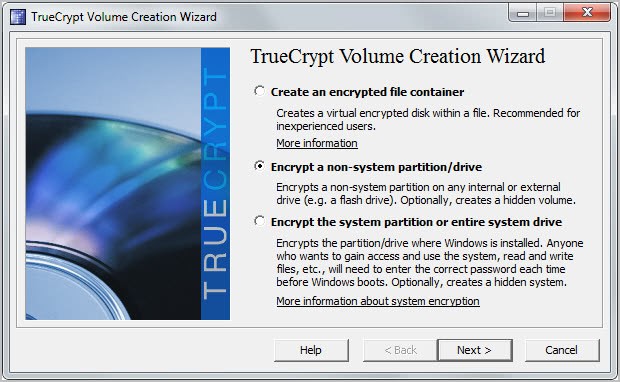
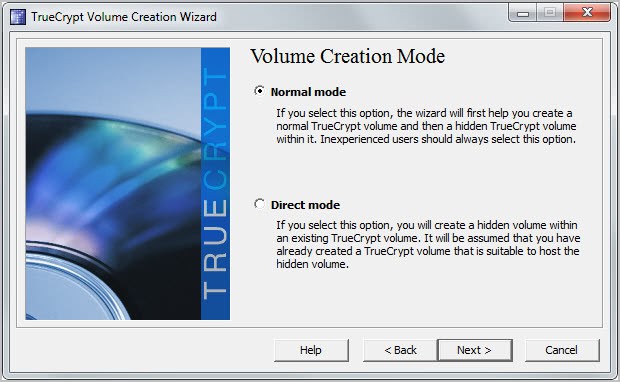
You have the option to create both volumes in one go though, by following the process outlined below. Click on Tools > Volume Creation Wizard. You have two options now how to proceed:
- Create an encrypted file container: This option can be used to create an encrypted file on one of the computer's hard drive and add a hidden file container to it, or add a hidden file container to an existing encrypted file.
- Encrypt non-system partition/drive: This is basically the same option as above, only that it works partitions and hard drives, and not with files. Please note that all contents of the selected hard drive/partition will get deleted in the process.
I suggest you start with an encrypted file container to see how the process works.
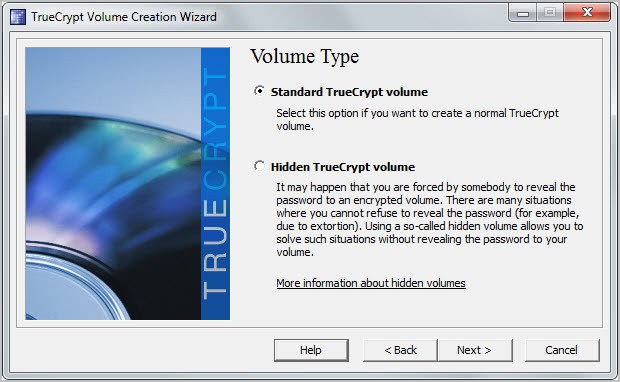
Select Hidden TrueCrypt volume on the next page
Now you have the option to select normal or direct mode. Normal mode creates both the outer and the hidden volume in the process, while direct mode creates a hidden volume inside an existing True Crypt file container.
Lets pick normal mode to demonstrate how both the standard encrypted container and the hidden container within are created.
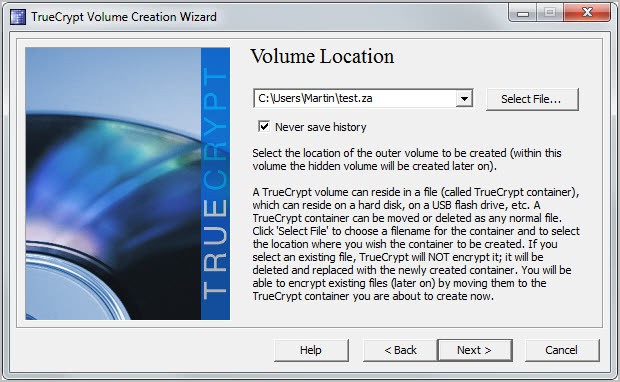
You now need to select a file name for the outer container. Pick any directory and file name that you want. You can use the file name to your advantage, for instance by making it a .tmp file or a .avi.
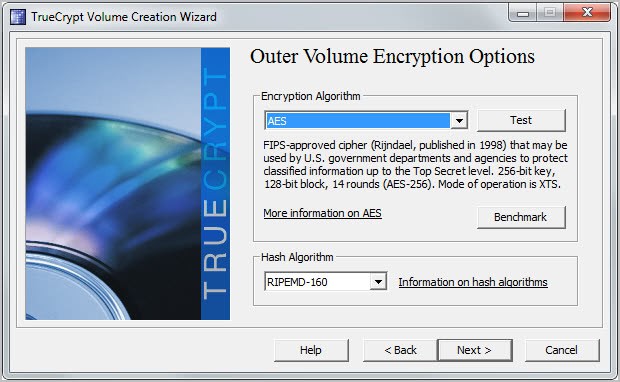
You are then asked to select the encryption algorithm and hash algorithm for the outer volume. Pick one each or keep the default settings.
You are then asked to select a size for the file container. Keep in mind that the hidden volume is added to this container file as well. Select a password on the next screen. This password is used to decrypt the files stored in the outer volume. The volume will be formatted afterwards. Move your mouse around to create random values. Click on Format afterwards to create the file. Depending on the size, you may need to switch the file system from FAT to NTFS.
Now that you have created the outer volume, you move on to the next step, the creation of the hidden volume.
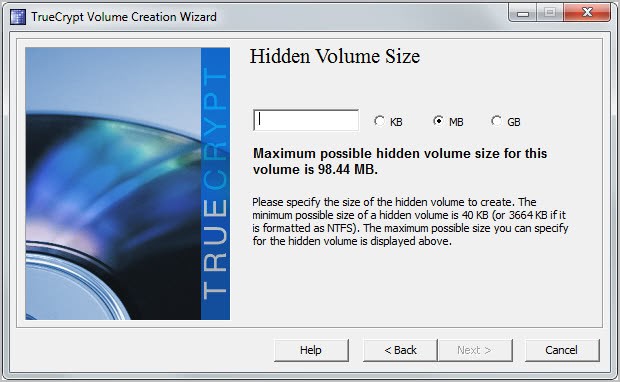
The process is nearly identical. You first select the encryption and hash algorithms, then the file size. True Crypt will display the maximum possible hidden volume file size on that screen. Don't select the maximum if you plan on adding files to the outer volume as well.
The remaining steps are identical. You now have one outer volume, one hidden volume and two pass phrases to decrypt the volumes on your computer.
Mounting the hidden volume
To mount either the outer or hidden volume do the following:
- Select a free drive letter in the True Crypt interface.
- Click on Select File and browse to the encrypted file that you want to mount.
- click on mount afterwards.
- Enter the pass phrase for the outer volume to mount it, or the password for the hidden volume to mount it instead.
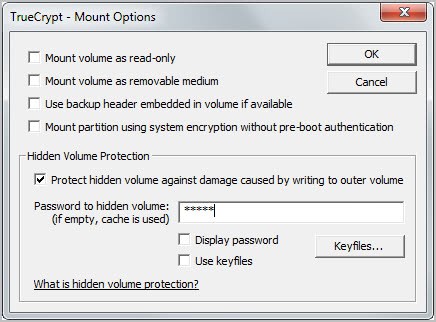
If you mount the outer volume you may want to click on mount options to check the "protect hidden volume against damage caused by writing to outer volume" box to avoid to protect the hidden container from being partially or fully overwritten. You need to supply the hidden volume password though for this option.
The very same principle applies to the creation of a hidden volume inside an encrypted partition or hard drive.
What's your take on this new ruling?
Advertisement


















That went well. Converted the truecrypt container, installed the new VeraCrypt and now the container can’t be opened anymore. It says the password is wrong or the container is not a VeraCrypt volume. This action basically destroyed my files, 9GB of them. I am not dumb, I have a backup. But VeraCrypt is dumb and this conversion thing does not work. Amateurish and and embarrassing. Let’s wait 7-8 more years, maybe they will manage to fix their garbage new program.
Linking the article I’m posting on because comments are ending up on wrong articles: https://www.ghacks.net/2023/10/02/veracrypt-1-26-7-update-brings-major-changes-read-this-before-updating/
I refuse to use anything other than TrueCrypt. I’m very suspicious of the events that caused TrueCrypt to morph into VeraCrypt. Yes it’s evidently still open source, but who is auditing the code? I don’t trust Vera, only TrueCrypt.
The new portable version, on Windows, seems unable to open a 256 bit AES VeraCrypt folder, but it still opens in v. 1.25.9.
Lot of 2012 comments need clearing out.
Regarding
VeraCrypt Portable 1.25.9.exe
https://www.veracrypt.fr/en/Downloads_1.25.9.html
Testing with Public key
https://www.idrix.fr/VeraCrypt/VeraCrypt_PGP_public_key.asc
GNU Privacy Assistant says signing key ID 680D16DE wrong; GPA throws up a message box which doesn’t allow copying of full message. Great.
I look at forum regarding PGP key change, trying to find the correct one:
https://sourceforge.net/p/veracrypt/discussion/general/thread/fcd0da57/
tried its link to this
https://pgp.mit.edu/pks/lookup?op=vindex&search=0x821ACD02680D16DE
and get:
Proxy Error
The proxy server received an invalid response from an upstream server.
The proxy server could not handle the request GET /pks/lookup.
Reason: Error reading from remote server
That’s enough time-wasting for now.
No, some information in the Comments is way off–especially the last comment made by Martin.
The first thought I had: Why would anyone even think of taking a personal phone during international travel? It’s absolutely insane.
Here’s a much more precise and informative article on border issues and what border officials can do; also, in the US, laptops and desktops, or any item in a home, can’t be seized without a warrant.
https://qz.com/912950/never-bring-your-phone-on-an-international-flight-unless-you-want-us-border-control-and-customs-to-take-your-data
From the article: “It’s totally legal for a US Customs and Border Patrol officer to ask you to unlock your phone and hand it over to them. And they can detain you indefinitely if you don’t. Even if you’re an American citizen.”
The article should help people understand the inanity of taking the personal phone anywhere. In short, “You can’t hand over a device [or lose a device due to theft or short term memory issues] that you don’t have.”
It’s funny: I see people on planes using their phones, cluelessly, as though the phone won’t be stolen, confiscated by authorities, or simply lost–dropped, forgotten somewhere. All that personal information gone, in the hands of a stranger. Major, total disaster–mind numbing thought.
I also have another question — this article is about the gov’t agents seizing laptops. What’s the issue on DESKtops? Also can be seized, or a different story?
They can also be seized, no difference.
This is a really good app. I tested it out by partitioning a hard drive that I planned to use for data. Then I encrypted that partition with True Crypt. I noticed that the partition was visible when I opened up Computer to view all my drives. So I went into Disk Management and removed the drive letter from the partition which made it invisible. True Crypt also has a portable app version so no need to install it on the PC. This makes it hard for even a tech saavy person to get into your guarded files. (unless they know your password, lol)
Of course if you are accused of doing something illegal and are forced to give up your PC to the government forensic labs none of the above will help. Just get a lawyer and see what info/passwords you have to give up :-)
“Of course if you are accused of doing something illegal and are forced to give up your PC to the government forensic labs none of the above will help.”
Not to be rude but you don’t know what you’re talking about. :/
Not to be rude … , but you don’t know what you’re talking about. Have you tried the various TrueCrypt encryption modes? And no, Da Gov’ment don’t have no magic pixie dust that allows them to crack everything.
Just a legal clarification: You are not required to provide your password as this is covered under the 5th Amendment against self incrimination. But should the authorities be made aware that there are files located in certain “areas” than you must provide the authorities with an unencrypted version of those files. As the authorities have a “right” to access the files once they know where it is. I would just say “I’m not aware of any”, and claim my tech guy handles everything, I don’t know tech.
I also travel around with the following file: “a little boy and his priest.avs”. Should anyone seize and opens said file, their computers FRY :)
But this TrueCrypt matryoshka concept is intriguing. Gotta try it out.
DanTe, how can I obtain said file that makes computers fry? How does it work?
Do like I do: troll the usenet for “free software” and see which one promptly got pass your virus scan and kills your stand alone PC. I do this about once a year to get the latest in killer software. Use something like the free SBNews Android or Newsbin Pro and just massively download. I generally look for the small (below 5mB) files that purports to be celebrity sex movies.
I was travelling to the USA once or twice a year but I also a few years ago. Not going to go there again until the craze has disappeared… might be a while!
I used to be a regular visitor to the United States. About every second year. But I stopped going 7 years ago, largely because of border hassles like this. The Canadians now get my money. I know I’m not alone in this.
Ahh but I am pure as the driven snow! (Except for posting on a blog during work.)
… and except for being Bernie Maddoff’s tax advisor!
Yes, I was just about to post that. They specifically address the hidden volume. To fill its purpose, you need to lie to law enforcement/homeland security, which is in of itself a crime. Of course once you get to court you can try to plead the fifth, but you may be forced to reveal its existence and the password in the same vein as the non-hidden volume anyway.
The best solution to someone asking for your password isn’t to plead the fifth, but to simply say you forgot it. This is of course also perjury, but nobody can look inside your head to prove it, so unless you told your cellmate about your cunning master plan, you’re good to go.
Rodalpho, isn’t a Truecrypt hidden volume 100% unidentifiable anyways? I don’t know, maybe an extreme expert would “recognize” certain patterns even if it’s hidden.
Once inside your outer volume, assuming they coerced you enough to get into it, would the US Gov’t have the right to manipulate / alter / delete files as a bargaining technique? I would think it unlawful “officially”, but a little imagination brings up some issues.
Or unless you write on a blog about it ;)
The Electronic Frontier Foundation has issued guidance for getting your mobile device across the border safely and protecting the data on it should it get seized.
https://www.eff.org/sites/default/files/EFF-border-search_2.pdf
Great read, thanks for posting Ilev.