Improve PC Security by Changing the RDP Port
PC security is comprised of effective firewalls, efficient anti-malware software, WPA and WEP codes as well as several other software-related tweaks and applications. When Remote Desktop is enabled, additional precautions must be taken to minimize the possibility of malware infection and hacking. If the tech at a software company can remotely operate your computer, then so can anybody else with the knowledge and ability. To protect against bots and script kiddies, the RDP Port must be changed.
The remote desktop protocol drives Remote Desktop Services through Port 3389 by default. Any Remote Desktop connections are made through Port 3389. This is the case for every user reading this unless you have already changed the port. Basically, this means that this port is an easy target. By changing the RDP port, security is enhanced because bots and kiddies are designed to target RDP Port 3389. Change the port!
For this to be truly effective, implement a strong account lockout policy. This defends against the use of RDP protocol to obtain the administrator password. If the password is attainable due to the absence of an account lockout policy, then the RDP Port can be found regardless of what it has been changed to.
Changing the default RDP port is achieved through a simple registry hack. Another method is to change the RDP port with a third-party utility. Always set a restore point before making changes to the registry.
The Registry Hack
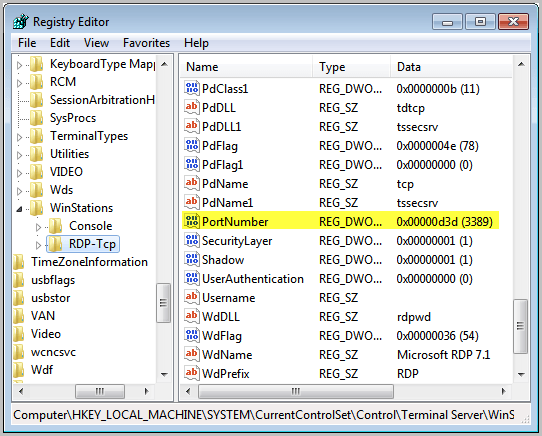
Run regedit from the start menu to open the Registry Editor. Navigate to HKEY_LOCAL_MACHINE, SYSTEM, CurrentControlSet, Control, Terminal Server, WinStations and RDP_Tcp. Find the PortNumber dword and right-click.
Select Modify. Alter the base to Decimal and enter the new port number with a value between 1025 and 65535, as long as the port is not in use. Click OK.
The Software Hack
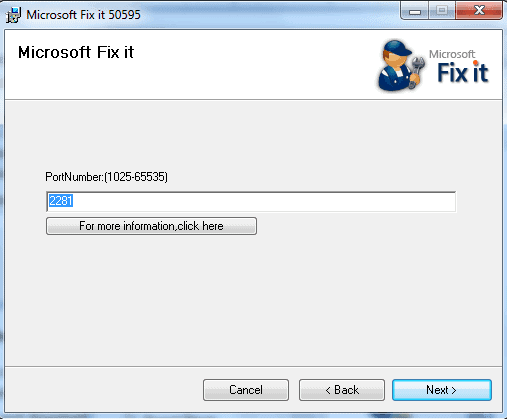
The Microsoft Fix It Wizard can be used to change the RDP Port. It is available through the Microsoft website. Here is the download link: http://go.microsoft.com/?linkid=9759545. Click this link and download the free utility. Click Next to initiate the Wizard. A PortNumber screen will be presented. Enter the value of an unused port that you want to use as the new RDP Port. Again, the value must be between 1025 and 65535. Click Next and you are done.
Reboot the system to put the changes into effect.
The next time you connect to your system with RDP you are going to have to provide the new port number. Be sure that you write it down in a safe place so you do not forget. From the Remote Desktop client, append a colon after the ip address or after the host name and enter the port number after the colon. This will set everything up to operate normally.
This may be a simple task, but it certainly is an effective step to avoid security problems with Remote Desktop operations. A good account lockout policy and changing the RDP Port goes a long way to keep the PC bad guys at bay.
Windows users who do not use Remote Desktop can alternatively disable the service completely to close down access completely. This is done with a click on the Start button and the selection of Control Panel.
There you need to open the System Control Panel applet and select Remote Settings from the options.
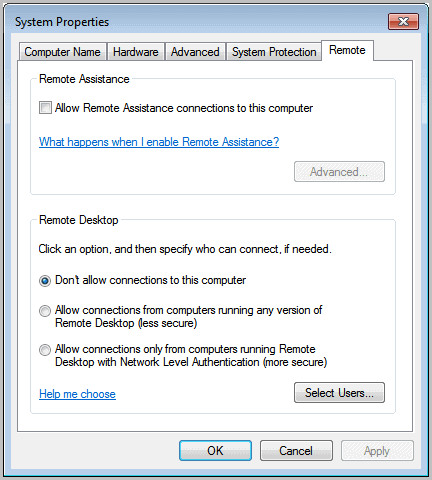
Uncheck "allow remote assistance connections to this computer" and activate "don't allow connections to this computer" under Remote Desktop.
Advertisement
















Yoics offers a solution for RDP connection that does not use Port Forwarding at all. Yoics sets up an encrypted peer to peer connection between a remote user and a computer on a LAN. No port configuation or VPNs to deal with and it is free. See http://www.yoics.com/rdp
I don’t see “don’t allow connections to this computer†in my system. Is it because I am using W7 Home Premium? I think this is only available to W7 Professional users.
Security through obscurity is not security. This is not a fix nor will it make you any more secure in the process. It only makes it take longer to find a way in.
If this port is open on the internet facing adapter or router interface, a port scan would find it open. nmap can identify it, even when its on an alternate port, so this is not a way to safegaurd against brute force attacks on RDP.
RDP should never be exposed to the internet. Instead, you should use a VPN into your network, and then RDP into machines through the VPN. RDP in itself isn’t insecure so much as it is easily brute forced when leaving the username administrator or admin as a possible account on the system running RDP.
The download link above is bad.
You are right, corrected it.