University Of California: 3 Banks Can Stop Majority Of Botnets
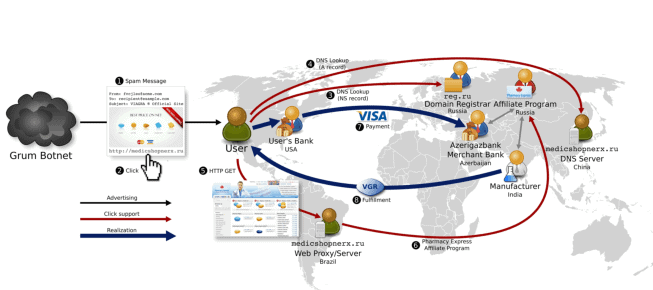
I never really understood why it was this difficult to identify the people benefiting from running a botnet. I mean, while it is relatively easy to use chained proxies, middleman and other means to stay anonymous, it is not as easy to anonymize the flow of money. Eventually, the money will land in the hands of the people who run the botnet.
A recent study of the University of California, entitled Click Trajectories: End-to-End Analysis of the Spam Value Chain comes to a similar conclusion, albeit from a different point of view.
95% of spam-advertised pharmaceutical, replica and software products are monetized using merchant services from just a handful of banks.
According to the university's study the most effective approach of taking down botnets is to stop the money flow at the bank level.
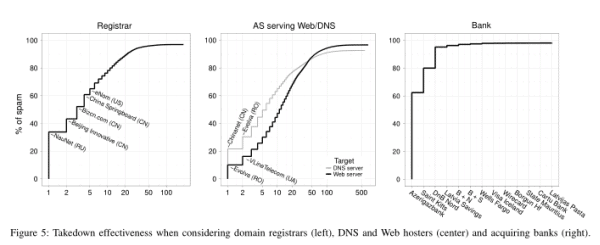
Considering that it is only three banks that "provide the payment servicing for over 95% of the spam-advertised goods in [the] study" it is safe to say that payment processing is the biggest bottleneck in botnet operation.
The researches analyzed other possible bottlenecks, domain registrars and hosting companies for instance, but came to the conclusions that this angle was not as effective as the payment processing angle:
For example, while only a small number of individual IP addresses were used to support spam-advertised sites, the supply of hosting resources is vast, with thousands of hosting providers and millions of compromised hosts. The switching cost is also low and new hosts can be provisioned on demand and for low cost.
By contrast, the situation with registrars appears more promising. The supply of registrars is fewer (roughly 900 gTLD registrars are accredited by ICANN as of this writing) and there is evidence that not all registrars are equally permissive of spam-based advertising. Moreover, there have also been individual successful efforts to address malicious use of domain names, both by registries (e.g., CNNIC) and when working with individual registrars (e.g., eNom). Unfortunately, these efforts have been slow, ongoing, and fraught with politics since they require global cooperation to be effective (only individual registrars or registries can take these actions). Indeed, in recent work we have empirically evaluated the efficacy of past registrar-level interventions and found that spammers show great agility in working around such actions. Ultimately, the low cost of a domain name (many can be had for under $1 in bulk) and ease of switching registrars makes such interventions difficult.
When it comes to payment processing and banks, the researchers concluded:
Finally, it is the banking component of the spam value chain that is both the least studied and, we believe, the most critical. Without an effective mechanism to transfer consumer payments, it would be difficult to finance the rest of the spam ecosystem. Moreover, there are only two networks—Visa and Mastercard—that have the consumer footprint in Western countries to reach spam’s principal customers. While there are thousands of banks, the number who are willing to knowingly process what the industry calls “high-risk†transactions is far smaller. This situation is dramatically reflected in Figure 5, which shows that just three banks provide the payment servicing for over 95% of the spam-advertised goods in our study. More importantly, the replacement cost for new banks is high, both in setup fees and more importantly in time and overhead. Acquiring a legitimate merchant account directly with a bank requires coordination with the bank, with the card association, with a payment processor and typically involves a great deal of due diligence and delay (several days or weeks). Even for so-called third-party accounts (whereby a payment processor acts as middleman and “fronts†for the merchant with both the bank and Visa/Mastercard) we have been unable to locate providers willing to provide operating accounts in less than five days, and such providers have significant account “holdbacks†that they reclaim when there are problems.21Thus, unlike the other resources in the spam value chain, we believe payment infrastructure has far fewer alternatives and far higher switching cost.
It needs to be noted that other banks can be used by botnet operators and it is likely that this is going to happen if the three banks mentioned in the study block payments to the operators of said botnets.
The study, available as a pdf document confirms that the most effective way of seriously impact the operation of botnets is at the payment processing level.
Advertisement
















The situation very much depends on the country. IF online banking is the prevalent method (as in .se, .fi, .ee .lt etc) AND interbank payments/transfers are moving fast (e.g. 9x per day as in .ee) THEN “follow the money” principle will be defeated.
There exist a concept of “money microlaundering”. It means that crooks will use an external application for bookkeeping and internet banking and some seemingly random identificator will be put onto the “Comments” field of any transfer. This way bigger sums are transformed info seemingly innocent small but random amounts. After that, a round of 5-10 sequential transfers will be done with the money, changing these “magic identificators” and sums on each stage and then, these “micropayments” are re-assembled onto bigger transfers again. Now imagine the investigation paperwork needed to reclaim all these transfers!
Until somebody have the overall picture over all participant banks and, is able to track and spot seemingly random identificators in real time, or, unless the crooks’ computer will be not arrested, that kind of laundering cannot be analyzed in real time. Provided there is a sufficient number of pwned accounts and human mules on the black commodity market, the money will be sucked out of the system with the speed exceeding the speed of analysis.
It means in countries with advanced e-banking, these mule and laundering networks will be used with the maximum effectiveness and the fight against realtime is not efficient anymore. The same idea worded otherwise – only ancient banking and slow services enable the sustained usability of “follow the money” principle.
In the linked PDF the banks are listed in Table V (search for it) and the 95% comes from Figure 5, where Azerigazbank tops at ca 50%, a Saint Kitts a further ca 30% and ca 15% via DnB Nord which is a more or less Norwegian bank that we could probably pressure into looking better at what customers they have. I suggest any norwegians reading this to send an email pointint out that DnB is dealing with spammers and reference them to the PDF link and figure 5.
You never understood why it was so “difficulty”?
Which 3 banks are those?
Cannot remember the names but the bank with the most payments is located in Azerbaijan. The two others were located in the Caribbean and Norway.