Yahoo Sign-In Seal Protects Against Phishing
Determining if a website is real or fake is one of the greatest challenges for many Internet users. Criminals have honed their skills in the past years to create websites that look in all design aspects as the real deal. Only information displayed by the browser aids in the verification process.
What if there was a way to customize the login page so that it becomes possible to verify the website on first glance?
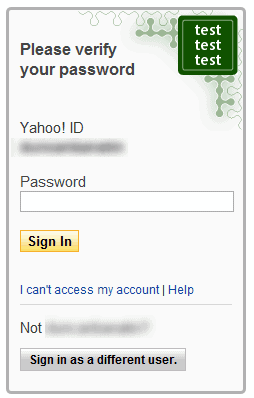
That's what Yahoo decided to do. The Yahoo sign-in seal is a custom text or image seal that is displayed on the Yahoo login page.

The custom text or image is displayed on the sign in page, and users know directly that a website is fake if it is missing or different.
Yahoo users can visit the settings page in their Yahoo account to configure the sign-in seal.
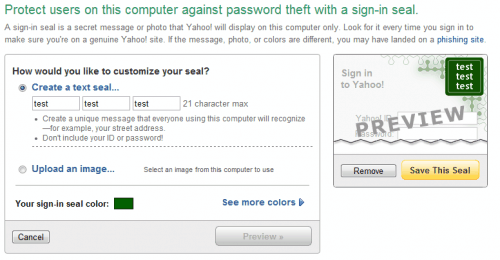
Here it is possible to add a total of 21 characters divided into three groups as a text seal, or upload an image from the local computer to use the image as the verification seal.
Finally, it is possible to select a specific color for the seal, to make identification even easier.
Yahoo users should make sure not to use their ID or password as part of the sign in seal. Yahoo suggests to use something that every user on the computer understands, a street address or name for instance.
Yahoo's Sign-In Seal is an excellent addition that improves the account security a lot.
What's your opinion? Let us know in the comments.
Advertisement

















I recently returned to Egypt and within 48 hours my Yahoo was phished and I fell for it. I had noticed the night before that my Skype was not working properly, but in my experience there are many irregularities on the web and I just assumed this was one of those. The next day when I signed on to Yahoo it behaved very strangely. But just like many people have remarked, not all users can or even try to identify the entire string in the URL. So I signed in and when I opened my mail I was horrified to watch my entire address book and all my saved emails vanish before my eyes. I shut down immediately but didn’t know what else to do. Next time I opened Yahoo I received many notes from friends asking if the phishing mail (stranded in London, etc) was really from me. Since then I have added the anti-phishing seal to my Yahoo mail and changed my password, but because the first sign of trouble was on Skype I wonder if the fraudster got in through Skype. If a seal at least provides an alert to pay better attention, I think Skype should make it available also. I have searched the Skype site for how to do this but cannot find anything. Can anyone give me any advice? And yes, please, I admit I was stupid, no need to rub it in. Mercy and compassion are virtues we should all attempt to practice in all aspects of our lives. Thank you!
> actually the seal does in fact prove you’re dealing with the right
> site – what it doesn’t prove is that there isn’t a 3rd party hijacking
> the session (man-in-the-middle/man-in-the-browser).
Which means you are NOT dealing with the right site but with the man in the middle instead (who is dealing with your site) , so I stand by my statement that the seal proves nothing by itself.
Unicode certificates are still identifiable and bad CAs use a different certification path than the real site. However, I’ll admit, a normal user is not likely to notice either of these. But the seal won’t help either if the MitM site is forwarding you back to your intended site.
A seal is an attempt to lower the bar to a level that all users can interpret. The risk is that they will view it as a guarantee.
> except that if your DNS settings are compromised the site name can be
> correct and still point to a fake site.
In which case the site either won’t have a security certificate at all (and thus no https connection and padlock) or the cert on the fake site won’t validate against the hostname.
> that being said, it doesn’t stop man-in-the-middle/man-in-the-browser
Exactly. And though the seal will appear perfectly correct, even an impersonated certificate will still be obviously wrong if examined.
By itself, the seal proves nothing. It merely increases the *probability* that the site is the right one, but it cannot guarantee it.
> Exactly. And though the seal will appear perfectly correct, even an
> impersonated certificate will still be obviously wrong if examined.
not necessarily. if it exploits a unicode character set in the name the cert could appear to be valid. additionally, not all trusted CA’s are actually trustworthy and some could be paid to issue a fake certificate.
> By itself, the seal proves nothing. It merely increases the *probability*
> that the site is the right one, but it cannot guarantee it.
actually the seal does in fact prove you’re dealing with the right site – what it doesn’t prove is that there isn’t a 3rd party hijacking the session (man-in-the-middle/man-in-the-browser).
I have always wondered about this feature but never felt interested to read about it. I guess I did now and I think it makes it more difficult for hackers to make phishing Yahoo sign-in pages but as I said it only makes it more difficult but it will never prevent Yahoo phishing pages.
I think Yahoo should do much better advertising for this feature as I am very sure that at least 50% of Yahoo users don’t know anything about it.
Thanks for the post Martin . Keep it up !
It really isn’t that helpful. If people would pay attention to the site name in their browser address bar, none of this would be necessary.
When people don’t pay attention the hostname or the padlock or other clues that tell them when a site is bogus, why would they pay attention to a seal? “There must be some good reason why my seal is wrong today, I’ll just login anyway.”
I actually saw a guy on TV once say he figured his non-bank had a good reason for asking for his login to his real bank, so he gave it to them. You can’t add something to your web site to fix that.
@king:
“It really isn’t that helpful. If people would pay attention to the site name in their browser address bar, none of this would be necessary.”
except that if your DNS settings are compromised the site name can be correct and still point to a fake site.
“When people don’t pay attention the hostname or the padlock or other clues that tell them when a site is bogus, why would they pay attention to a seal?”
as mentioned above, the hostname can be correct and still point to a fake site. the padlock is also possible to game through a number of tricks – getting a cert isn’t as hard for the bad guys as it’s supposed to be, and nobody actually checks the details for the cert (simply ensuring that there’s a padlock only tells you the connection is encrypted, not that the site is trustworthy.
the seal, on the other hand, is a much stronger form of site authentication. it’s a shared secret between you and the site, just like your password. just as you have to prove you are who you say you are by presenting a shared secret in the form of a password, the site has to prove they are who they say they are with the information stored in the seal.
that being said, it doesn’t stop man-in-the-middle/man-in-the-browser attacks or password stealing malware. it’s stronger than the various safe site indicators like the padlock, but it’s not 100%, and yes people could still ignore the warning bells that ought to go off if the seal data were wrong (or more likely missing altogether). for those of us who don’t ignore details (the only people whose security can be enhanced), though, this is a pretty good feature.
“There must be some good reason why my seal is wrong today, I’ll just login anyway.â€
LOL , you’re totally right about that . Some people just don’t care about security either because of ignorance or because they are just careless !
indeed, banks have been using a similar form of mutual authentication for a while now, but it’s good to see other sorts of sites providing mutual authentication as well.
this is especially important for webmail providers like yahoo, since your email account can often be used to compromise all sorts of other accounts.
DUH! Banks have been DOING this for quite literally years now. Where u been?
Yahoo have been doing it for sometime too , but maybe Martin didn’t notice it or didn’t want to write about it ’till now.