How Secure Is A Password?

New technologies and more powerful computer systems have made it important in the last years to create secure passwords to avoid successful automatic password cracking attempts via brute force and dictionary attacks.
But how do passwords have to look like to be considered secure? And who determines that? There is no authority with guidelines on the creation of secure passwords. Companies, organizations, software developers and end users all have their own definition of secure passwords.
While some may think it is sufficient to select a password with numbers in it, others demand a password with upper and lower case chars, numbers, special characters and a minimum length of 16 or more.
Defining the format of a secure password is however only one side of the medal. It does not do anything good if the software, website or service is not compatible with those settings. A website that restricts the password to a length of 10 characters without special characters would be incompatible with a secure passwords policy that requires at least 14 chars and one special character.
Generally speaking, a password becomes more secure with the length of characters it contains, and the different types of characters used.
Several companies have created online tools that give users feedback on the complexity of passwords entered. Is that password secure is a common search term for those services. Lets take a closer look at some of them, but before that, lets define some typical passwords that we will feed them.
password 1: password
password 2: 4wOe409r
password 3: !S8I5U39YDnt8f
password 4: E&4!74mneGrTmOJ!HIr0
password 5: DP12c*0J!dM5mfdq2r!&WmMi!#g3
Update: Microsoft Password Checker is no longer available.
Microsoft password checker: Offers a simple form field which accepts a password. The ratings go from weak to best.
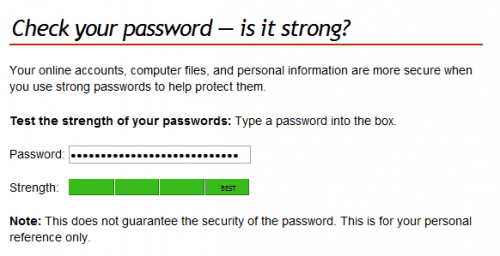
password 1: weak
password 2: weak
password 3: strong
password 4: strong
password 5: best
How Secure Is My Password: Does not display a rating, but tries to estimate the time it would take to crack the password.
password 1: One of the 500 most common passwords, It would be cracked almost instantly
password 2: It would take About 252 days for a desktop PC to crack your password
password 3: It would take About 564 billion years for a desktop PC to crack your password
password 4: It would take About 100 sextillion years for a desktop PC to crack your password
password 5: It would take About 100,603,110 nonillion years for a desktop PC to crack your password
The Password Meter: Compiles a list of all characters used and rates the passwords accordingly.
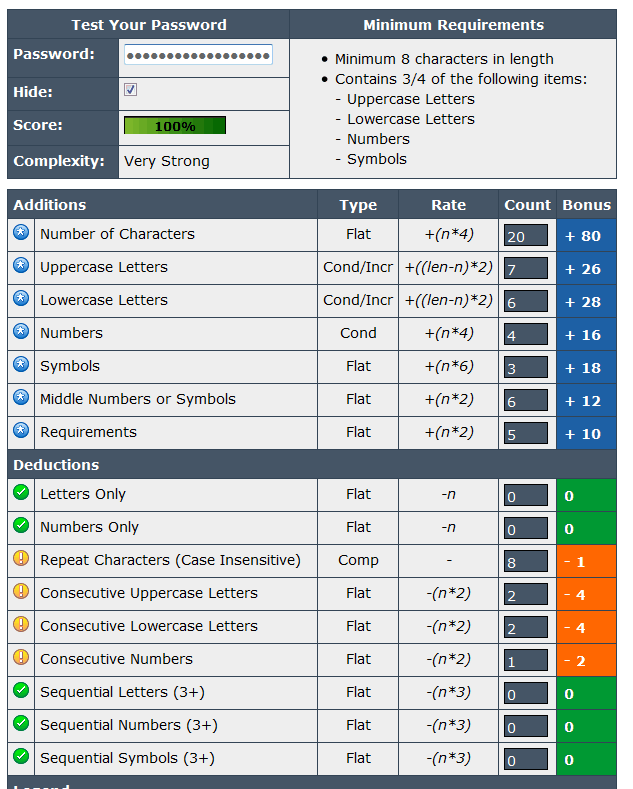
password 1: Very Weak, score 7%
password 2: Very Strong, score 81%
password 3: Very Strong, score 100%
password 4: Very Strong, score 100%
password 5: Very Strong, score 100%
The three password security checkers seem to disagree on the strength of some of the passwords used. All see the first password as a weak password, but similarities end there, as the second password is considered weak by Microsoft, but very strong by Password Meter.
The question now is how you can come up with a password policy to make sure that you only use secure passwords. The answer is simple: Always use a password that comes close to the maximum length allowed. That value is highly software and site specific. Here are a few suggestions:
- Never use a password with less than 16 chars unless the site limits the maximum character length to less than that
- Always use upper and lower case characters
- Always use at least one number in the password
- Always use at least one special character in the password
- Never use dictionary words as part of the password or the password
This leads to a problem: Remembering the passwords. The easiest way is to use a password manager like Last Pass or KeePass for this. Password managers can create passwords based on the user's parameters. Last Pass users for instance only need to press Alt-G to open the password creation window in the web browser.
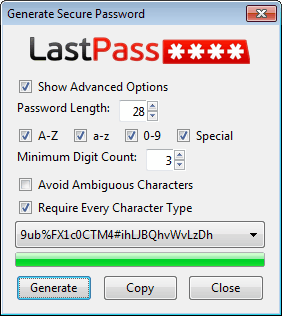
The password can then be copied and entered during account creation. These passwords can also be used for non-web services, and stored in the password manager for retrieval.
Password managers will automatically save passwords and accounts that have been created, so that there is no need to remember the password. Only the master password, which is the password providing access to the password manager's database needs to be remembered and should be uber-secure as it protects all accounts.
A simpler solution is to write down the passwords locally, and either carry them with you all the time, or store them in a secure location so that third parties cannot use them to access the accounts.
Do you have a password policy? Let us know in the comments.



















Extensive coverage of the password & security issues:
http://preibusch.de/publications/password_market/
http://www.lightbluetouchpaper.org/?s=passwords+in+the+wild
To top it all, take a look at this:
Study Reveals 75 Percent of Individuals Use Same Password for Social Networking and Email
http://www.securityweek.com/study-reveals-75-percent-individuals-use-same-password-social-networking-and-email
Related to:
The Limits of Privacy. Is This Your Password?
http://www.malwarecity.com/blog/the-limits-of-privacy-is-this-your-password-865.html
“What`s the point of even creating a good one if then you are going to send it in the wild using an Internet connection. ”
Well the same must hold true when passwords are used to log on to a website? In such cases when they are released into the ‘wild’ they are usually allied to the user name as well. Sites like https://www.pwdhash.com use encrypted connections and as with http://wijjo.com/passhash/passhash.html they can do downloaded for use on your computer, without the need of an internet connection, as all the work of these password utilities is done within a browser.
The problem of submitting a password to a test site is really only a risk if it can be linked to a user name and the website service such accesses. Though I understand research indicates many people recycle and use the same password for many sites, which might be why the word “one” in terms of a “good one” (password) was used in the quoted comment above.
Of course if an open unencrypted wifi connection is used and a site like tumblr.com is logged onto and whilst it is be used, all of your passwords/usernames can be intercepted as Tumblr, unlike nearly all other blogging services has no encryption facilities what so ever and they have not responded to follow queries I made asking them why…
To prevent some of your data going wild, I suggest taking a look at: http://www.eff.org/https-everywhere
Now all of the caveats are worthless if your computer is infested by malware and in situations when you really, really need to protect high value online assets maybe take not of these suggestions:
Avoid Windows Malware: Bank on a Live CD
http://voices.washingtonpost.com/securityfix/2009/10/avoid_windows_malware_bank_on.html
I think its not realize wise to use online tools to check the security of your passwords. What`s the point of even creating a good one if then you are going to send it in the wild using an Internet connection. Knowing the general rules one should be fairy sure about the quality of passwords he/she can come with
Interesting that cracking 4wOe409r will take 252 days. Replace the last character with an !, and it jumps to 3 years. However, not all special chars appear to be equal: braces like { and ] are no stronger than the “r”, but symbols like # and , are equivalent to the !
I use Password Safe since several years now and it’s very good.
http://pwsafe.org/
Has a password generator where you can specify different policies (e.g. for normal and administrative accounts)
It also has a password history feature that helps you avoid generating passwords that are not compliant with the password history policies.
Use 3-letter passwords. Nobody will guess them!!
The Microsoft password checker seems useless to me. It only looks at the length of the password.
When i type password:
microsoft
it says Weak.
When i add a couple of ones after that it says Best:
microsoft1111111111111111
Leon you seem to be right. Using only length as an indicator of password strength is not good at all. You can for instance add 111.. and so on and will get a best rating eventually. Length is only part of the strength, users need to make sure to add character variations as well.
The length of the password seems to be the deciding factor for all 3 password checkers, since all 3 give the following password an indication Very Strong (or similar terms):
microsoft1111111111111111
While only the word “microsoft” is indicated as very weak.
+ this might be ueful:
http://www.passwordcard.org/en
for the likes of wifi, this can be handy:
https://www.grc.com/passwords.htm
and for an insight into password use and keeping a copy in your wallet:
Schneier on Security: Write Down Your Password
http://www.schneier.com/blog/archives/2005/06/write_down_your.html
I prefer to use password methods that all I need to remember is one master-password and have online ways to recover and use them and they operate within my browser, without having to be online. I suggest checking out:
http://wijjo.com/passhash/passhash.html
https://www.pwdhash.com/
Both of the above can be download locally.
I like PasswordChart, but the site seems to be spawning malware:
http://safebrowsing.clients.google.com/safebrowsing/diagnostic?client=Firefox&hl=en-US&site=http://www.passwordchart.com/
Using these online password recovery tools: also defeat some of the problems mentioned at http://bit.ly/9s5aFS as there is no locally stored hash file of passwords to attack, this is because the master passwords are stored in the users memory or on a printed chart. Or maybe just keeping them in your wallet is after all a good idea.
Awesome websites , especially the third one Password Meter , it’s so accurate and reasonable .
and to crack a p/\$$\/\/0rD
It would take
About 100 million years
for a desktop PC to crack your password
wow
Saw the item below and though of this ghacks.
Scientists claim GPUs make passwords worthless
http://www.pcpro.co.uk/news/security/360313/scientists-claim-gpus-make-passwords-worthless/print
Background:
Teraflop Troubles: The Power of Graphics Processing Units May Threaten the World’s Password Security System
He says any password shorter than 12 characters could be vulnerable – if not now, soon.
http://gtresearchnews.gatech.edu/graphics-processing-units-security/
What is not covered is the how feasible it would be to recover or brute force passwords to access online services, unless the attacker has access to an encrypted password protected file that contains the likes of bank account password/username details. They can’t simply go to a banks website and try out millions of password/username combinations, in such situations websites will just freeze access to an account or block the attackers IP address.
Now many service like lastpass/roboform/keepass etc keep a local database file of passwords and so if the attacker can get a copy they could use this GPU power to brute force the password to the database. So I suggest the weakness would be using any system that stores passwords locally on a computer and this computer is easy to access and thus compromise.
Plus lets not forget access to our online account passwords, for the average person, is based on malware infecting our computer, which can report back keystrokes or actually mimic our actions and log in out accounts and steal the money.
Tip: I protect my online accounts by using unique hard to guess email addresses like:
E&4!74mneGrTmOJ!HIr0@hotmail.com
and I do not share the email address for any other purpose/service.
As a lot of online accounts use an email addresses as the usename, maybe this technique acts like having two ‘secure’ passwords. Plus email services like fastmail.fm allow lots of virtual email addresses to be set up that all go to one main mail email account and I never share the ‘real’ fastmail account address with any third party and the email service offers secure SSL/HTTPS access.
I love LastPass and use it myself for everything BUT financial websites (online banking and credit card accounts). I’d give it that, too, but my problem with LP is that it effectively amounts to using the same password for every site, since LP itself is protected by a single password, and cracking that password yields access to all of the others stored there.
There are some websites that don’t allow numerals or special characters in their password, so unfortunately using numbers and special chars is also site-specific.
i can rest i guess
“It would take About 65 years for a desktop PC to crack your password”
Martin, this one is off topic have you had a chance to see Tab Candy new prototype from firefox (which may land up in firefox 4)
http://www.azarask.in/blog/post/tabcandy/