How quickly can your password be cracked?
As more and more of us live more of our lives online with banking, shopping, photo galleries and social networking etc. a part of our daily lives, it becomes more and more important to have secure passwords. But there are problems in remembering complex passwords when there are so many websites you have accounts with. My tip, choose one or two super-strong passwords and change the passwords on every website you have an account with to those.
The easiest passwords to crack are those that are simple words. If your password is your date of birth, dog's name, child or favourite place then I'd suggest changing them for a stronger password today. These types of password will always be the easiest to crack, with the perpetrator only needing to know minor details about the victim, things that you may already have included as public information on your Facebook or MySpace profile page. Unwittingly, you may be publicly providing the very information that criminals need to empty your bank account, steal your identity or run up huge bills on your credit cards.
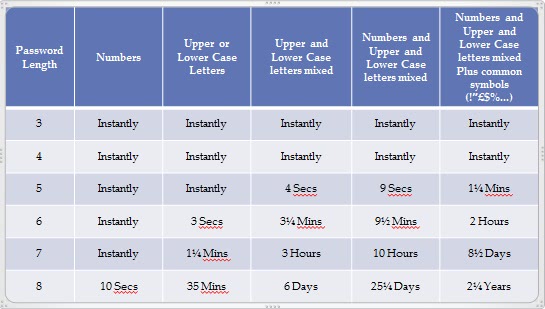
The chart below details how long it would take an average PC to crack different types and lengths of password. Where does your fit in the chart?
So how do you create a super-strong password? The ideal one would contain a mixture of upper and lower-case characters with some numbers and maybe even somthing like a # or % sign thrown in. But how can you create one of these you won't forget?
There are several easy ways to make sure your password is secure. First is to remember that numbers can be substituted for words. The password wo0dy with a zero in the place of the second "o" is much more secure than the name as it's really spelt. You can increase this security even further, perhaps by making a character upper case. wo0Dy is a password that's even more secure and that could provide all the protection you need, unless...
You should try and make sure that your secure password or passwords are a minimum of six characters in length. This is because if you want to use the same password on every website they will demand that they be that long at least. Some websites will demand eight character passwords so if you can have one of those to begin with then all the better.
You can mix things up if you are short on ideas. If Woody was born in 1982 then you could use wo0DyIi982 or wo0DyI1982 where the 1 in the year is substituted for the letter "i" in either lower or upper case.
One final word of advice, your secret question. Most websites will require you to have a secret question to unlock your password if you forget it. Try and avoid choosing your mother's maiden name, place of birth or first school if at all possible, as these are things that can be found out by criminals all too easily. If you have to choose an option like this because a website forces you to, an answer such as amst3rdam# might be enough to remind you of your favourite place.
If you follow these rules then you will have a much happier and far more secure time online. And a daunting password may look like that at first, but you'll be amazed at how quickly you get used to using it.
Advertisement
















Yes, exactly like Oneide said. Use a password manager, which has only one strong password as hell and then all your passowrds are safe. So I use Sticky Password manager, which is a great tool for protecting online identity.
This is really, really really really really quite incorrect. That table must have been made up on the spot, there’s no research behind it whatsoever. Passwords are stored as hashes, and even a plain text eight character all one case would take a good few days on a brute force method, provided that the password wasn’t in a dictionary. UGH. Do your research Ghacks, seriously. I’m pretty tempted to unsubscribe because this post misses the point so badly.
Yeah, it looks like the numbers are out of proportion. Using the 35-minute value would indicate that the computer searches through 50 million possibilities a second (assuming it refers to the average time for a bruteforce search), in which case the 10-second value is totally wrong, but the rest of the numbers “make sense”.
The main reason why this chart doesn’t apply to the services in question is that most of them have anti-hacking measures built in, such as limiting the logins to 1 per second or locking the account after 10 consecutive failures etc. For a system without such measures (stored unsalted hashes, and zip file passwords, say) it might still be possible to achieve high speeds, but for those with stronger protection it is just not practical.
Of course, it is also likely that more than 1 PC will be cracking, so don’t relax too soon. The point still stands, since weak passwords are still easier to crack (or at least, will be cracked first). The more valuable the data/access, the more important the password strength is.
How about lastpass or something of the kind? Just one solid password and as many strong (generated) passwords as sites you subscribe. So, you don’t compromise your security if one of it is disclosed.
I agree with Oneide here, LastPass or any password manager is the way to go. Just make sure you select a secure master password and generate ultra strong passwords for all the sites that you use.
What a loaded topic! Many things go into this:
1. Does the site specify what you have to use for the password (min and max lengths, specific directions on what you can and can’t use in your password)? The more directions the site gives you, the easier it is to shape the keyspace that you have to attack.
2. If the site says that you can’t use certain characters in your password and/or tells you that it can be longer than a certain length, that means that they are either storing it in cleartext or with reverseable encryption. Why brute the login when you can hack the database and get a list of cleartext passwords?
3. Is the attacker going to bruteforce the login or is he going to get a list of hashes and attack them directly? How are the hashes stored, salted or bare?