Adobe Reader Vulnerability Exploited By Botnet
Security issues with Adobe products seem to be in the news quite frequently this year. No week passes by without yet another report about a security vulnerability or update of a popular Adobe software program.
Recently an Adobe Reader vulnerability was discovered that allows attackers to execute code on a target machine. This is done by specifically preparing a pdf with an executable embedded in the code.
To be fair: This vulnerability does not only affect Adobe Reader but also some tools from third party developers like Foxit.
Adobe did not patch the issue on last week's patch day but explained how to protect programs so that the malicious code cannot be executed even if a specifically prepared pdf document is loaded.
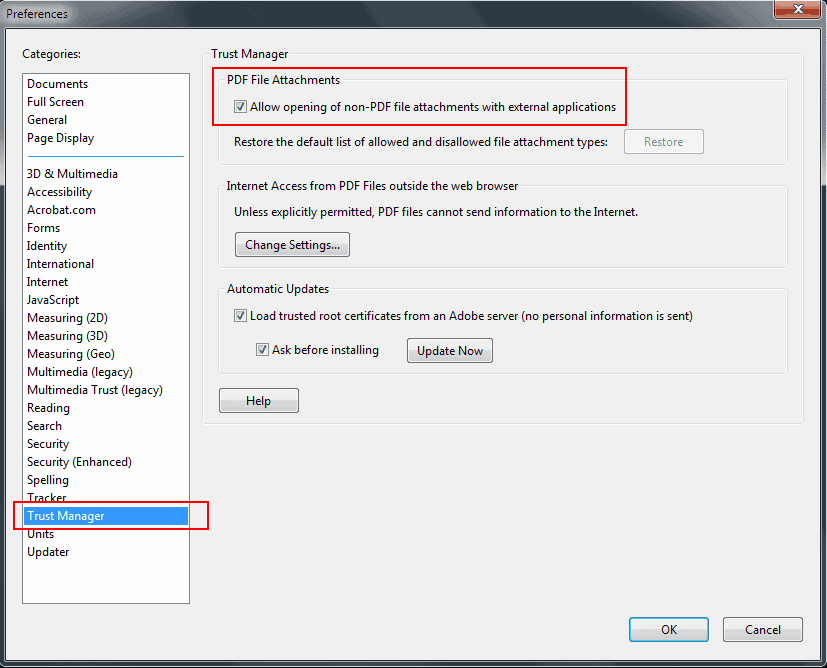
Computer users who want to protect their system from the attack need to open Adobe Reader, click on Edit > Preferences to open the options, select Trust Manager from the categories menu and uncheck the PDF File Attachments option that reads "Allow opening of non-PDF file attachments with external applications".
The security issue is currently actively exploited by the Zeus Botnet according to an article on PC World with several thousands of attacks underway. The pdf documents used in the attack embed code in the document that displays a save prompt to the user when the pdf document is opened. The user is asked to save a pdf called "Royal_Mail_Delivery_Notice.pdf" which in fact is a disguised executable that will run malicious code on the user's computer.
It is nearly impossible for users to determine if a pdf document is legit or if it contains an embedded executable with malicious code. It is therefore highly recommended to make the change that Adobe suggests.
The best way to handle the issue is to make the configuration change in Adobe Reader to protect the system, for now.
If you are using a different program to open pdf documents on your system, you may want to search for a comparable option in those programs, or verify that the program that you use to open PDF documents is not affected by the vulnerability.



















Evince reader works well 4 PDF files and 4 various image files including JPEGs.
It’s open source and It’s pretty stripped out.
Sumatra PDF FTW!
http://blog.kowalczyk.info/software/sumatrapdf
Open source too. Works great..
I removed the check from the box for “Allow opening of non-PDF file attachments with external applicationsâ€, closed the page, and did a file exit of Adobe. Reentering Adobe and returning to Trust Manager, noted the item (above) was again checked. Repeated the removal, closure, and exit, then return, only to find the same situation…the item (above) returns to the original (checked) state, or I need to do something else.
Seems you need to start the program as an administrator.
Foxit Reader 4 Life
Why not just uninstall Adobe Reader?
If you are using one of the many free aftermarket readers, I don’t think you need Adobe’s Reader at all.
I use PDF XChange Reader and I do not have Adobe Reader installed.