Five ways to help secure Apache on Linux
Apache is one of the most popular web servers available. And most Apache installations are running on Linux servers. Anyone running Linux will tell you that the operating system (be it on a server or desktop) enjoys a level of security many operating systems do not enjoy. But does that mean you can just install Apache and assume it 100% safe? No. There are always ways to improve your security on just about every level.
In this article I will show you five simple ways to make your Linux Apache installation more secure. And of course you should always know that even with five new means of making your install more secure, that doesn't mean it is perfectly safe from attack. Even after securing your installation, you should always keep watch over your server by checking log files and using standard security tools.
With that said, let's get our Apache security on!
1. Update, update, update! One of the biggest no nos Linux administrators make is to "set it and forget it". This should not be your standard policy. There are always updates that close new holes and patch security flaws. This holds true for Apache as much as it does any other system or application. Keep watch, using your normal means of update, for any security update for Apache or any constituent component you have installed. By doing this you will ensure your web server is safe from any new known issues.
2. Disable modules you do not use. If you check the Apache configuration file. Most often this file is called httpd.conf and its location will depend upon what distribution you are running (For example CentOS has this file in /etc/httpd/conf/ whereas Ubuntu locates it in /etc/apache2). If you examine that file you will see quite a few modules listed. These modules will look like:
LoadModule auth_basic_module modules/mod_auth_basic.so
LoadModule auth_digest_module modules/mod_auth_digest.so
LoadModule authn_file_module modules/mod_authn_file.so
LoadModule authn_alias_module modules/mod_authn_alias.so
LoadModule authn_anon_module modules/mod_authn_anon.so
You might have to look up what some of these modules do to know if you need them or not. But there is no reason to load a module if you are not going to use it. To keep a module from loading place a comment in front of the line. You will have to restart Apache for this change to take effect.
3. Limit the request sizes allowed. Denial of Service attacks remain one of the most popular attacks on web sites because they are the easiest to pull off. One way to protect your site from DoS attacks is to use the following directives wisely: LimitRequestBody, LimitRequestFields, LimitRequestFieldSize, LimitRequestLine, and LimitXMLRequestBody within a Directory tag (the document root is probably the best place for this). By default Apache sets these directives to unlimited which means any size of request can be made. You will want to investigate these directives and configure them to suit your web sites needs. Unless it is absolutely necessary, do not set them to unlimited.
4. Use mod_security. This is the most important module you can use. This one module handles such tasks as: Simple filtering, regular expression filtering, server identity masking, and URL encoding validation. It is likely you will have to install mod_security, because the default Apache install does not include this module. Once installed you will want to make sure you at least add the "unique_id" and "security2" directives in your Apache module section and then restart Apache. I will deal with this module in its own tutorial coming up very soon.

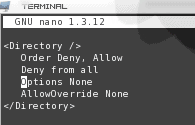
5. Restrict browsing to your document root. The last thing you want is to allow browser to peek outside of the Apache document root (Such as /var/www/html or /var/www/). To do this you will want to configure your document root directory entry as shown in Figure 1. This will
Of course if you want to add options to any directory inside of the document root you will have to give that directory its own Directory entry.
Final thoughts
There are plenty more ways to secure your Apache installation, but these will get you started. Can you think of other ways to secure an Apache installation? If so, share them with your fellow ghacks readers.
Advertisement














that’s ferry annoying paulus. anyway, thx for the article
Thanks Jack one of your best reads. Ferry useful this article hopefully you will find the time to wright much more extended, about security. This because i personal think that security still is among the poor and that it would be ferry smart, to raise the level of security extensively in the ferry near future.