Verify the File Integrity of Backups
While it is essential to create regular data backups to avoid data loss due to file corruption or theft, there are other precautions that administrators and users should take to ensure the integrity of their backups.
Depending on where and how backups are stored, backups can become corrupt over time which would render them useless for exactly the reason they have been created in first place.
It can for instance happen that backups become unreadable if they are stored on optical discs.One option that you have is to verify the integrity of backups regularly so that you can be certain that files can be restored if the need arises.
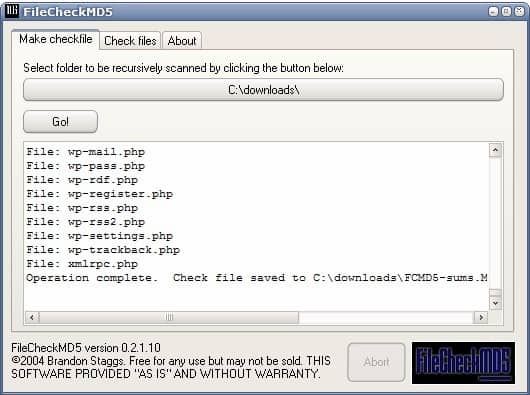
File Check MD5 is a small portable software for Windows that has been designed for that specific purpose. It can be used to compute MD5 hashes of all files in a specific root folder including files in all subfolders. All MD5 hashes will be stored in a text file in the root folder.
The Check Files option can then be used to check files in the backup storage location. It uses the original MD5 hash text file for comparison and reports back to you any issues that may occur.
One interesting option of the software program is to test md5 hashes that have been previously generated if the text file is located in the same folder as the executable. It would then only be a matter of adding the File Check MD5 software and the text file with the MD5 hashes to the root of the backup to automatically verify the file integrity. This is great for optical discs for example as you can add all means of verification to the root of the disc.
The only thing that is missing is the ability to select a different storage location for the MD5 hashes. This would make it possible to run the software on read only devices as well.
Update: The author has retired the program and created ExactFile instead which serves a similar purpose. It is an advanced version of the application. Among the features that it adds are options to select a different output path for the verification file, switch to another hashing algorithm, or run a benchmark.
It can furthermore be used to test single files using more than ten different hashing algorithms.
Advertisement















I agree with Dotan. I would love to see the link at the end of the page. Sometimes I read a headline and want to try the software right away, and I have to scour the article to try to locate the link. If it’s always at the end, then we, the readers, would know to just skip to the end if we want to download the software and read the article later. All the other things Dotan mentioned are good ideas too. Those you should include in your articles Martin.
Thx, but i use http://www.md5summer.org/
Thanks for the tip, Martin. Might I make a suggestion? It would be nice if software reviews had a small summary of critical information, such as:
1) Name of program with link to homepage
2) A _one_line_ description of what the software does
3) What OS the software runs on
4) If the software can be run from removable media, ie, if it is portable software
5) Licensing terms and cost of the software
Thanks!
Dotan the current design of the site would only allow for the information to be displayed at the bottom. I try to add the information in the article as good as I can at the moment.