Create a secure data safe with True Crypt
This article is going to show you how you can create a secure data safe on your system using the Open Source program True Crypt. You can use the safe to store personal files or information that no one but you or authorized users can access.
True Crypt makes it very easy to encrypt almost any storage device, be it a hard drive, partitions, usb Flash drives, or just a custom part of a device used to store data.
Once everything is setup you mount the True Crypt whenever you need to access the data. This is done by entering a password into the True Crypt application that you have selected during creation of the encrypted container.
This is actually the only password that you have to remember, everything else can be kept in the encrypted container for safety reasons. A big advantage is the fact that you can start any application from the container once it is mounted including torrent and ftp clients, Usenet software, email programs or web browsers to name a few possibilities.
True Crypt is available for Linux and several Windows editions including all versions from Windows XP onwards. Please download the software from the location above and install it afterwards.
The only other thing that you need is free space on a hard drive or a storage device. I would suggest an usb Flash drive or memory key for instance. I have for instance encrypted my secondary hard drive completely using the software. That is 320 Gigabytes of data that is encrypted by the software.
To create a data safe do the following:
- Launch True Crypt.
- Click on Create Volume.
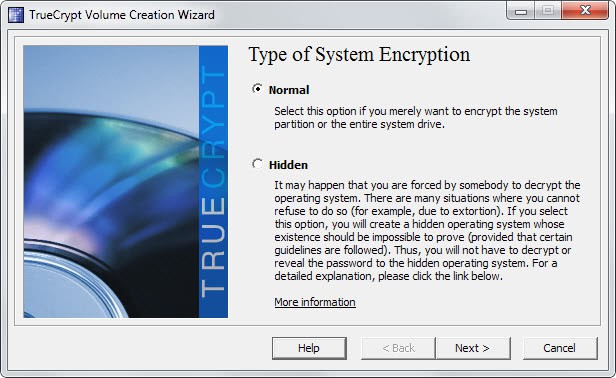
- Decide if you want to create an encrypted container, encrypt a non-system device, or the system partition or entire system drive. The first option uses a set amount of Megabytes from any hard drive or storage device and uses it to create the encrypted container. The second option encrypts a partition that is not the system partition (the one the operating system is stored on), while the third lets you encrypt the partition of the system.
- Select create an encrypted file container and click next.
- Select Standard True Crypt volume on the next screen and click next.
- Browse to a location that you want to store the file and name it, something like test, data or whatever.You can select any file name you want. Click save, then next.
- Select an encryption algorithm, AES is fine for instance. Click Next.
- Select a file size for the container. You can select as much as you want up to the limit displayed by True Crypt. It is usually not recommended to go overboard here though as you may need the data for other things. If you want to encrypt the full drive, select one of the options that lets you do so on the first screen.
- Create a secure password that you can remember. Write it down for the first time if you want to be sure that you do not forget it. Get rid of that paper as soon as possible.
- Click on Next, move the mouse around for a minimum of 30 seconds and click on format afterwards.
- A message should appear that the container was created.
- To mount it simply select a drive letter that is not taken and click on Select File and browse to the file that you created
- click on mount and enter the password that you have selected during installation
- If everything worked out fine the container gets mounted and you can use it like any other drive on your system.You can for instance move important files into the container or create a text file that contains all of your passwords.
- Do not forget to unmount the partition if you leave the computer for a longer time. Booting or shutting down automatically unmounts the drive.
So, where are the advantages of this method over tools that work like password safes? The main advantage is that you can not only store passwords in the encrypted container but also files and everything else that you can think off. Just move the files inside and no one can access them unless they have access to the password.
As I said earlier True Crypt works with big hard drives and there is no visible loss in speed during read and write operations. The devices work as usual once mounted. You could for instance run your favorite torrent client from that drive saving those torrents on it as well.
Advertisement


















I use the “auto-mount devices” function, so the volume is mounted at startup. The password to open the TC container is provided automatically by the credential manager system of my PC. I use a HP notebook with fingerprint reader, so once I logon to XP, the credential manager can automatically provide TC with the password (this saves me from typing it every time I logon).
I agree, I have been using also for about 6 months and it is really great. The only problem I had was when I tried to encrypt on a compressed hard drive; that didn’t work. But other than that it just works!
I have been using True Crypt for a few months now and it is simply awesome, btw I’m using version 4.3 now.